Lab 3: Perform LDAP Enumeration
Lab 3: Perform LDAP Enumeration
Module 04: Enumeration
Lab 3: Perform LDAP Enumeration
Task 1: Perform LDAP Enumeration using Active Directory Explorer (AD Explorer)
LDAP enumeration allows you to gather information about usernames, addresses, departmental details, server names, etc.
Z:\CEHv11 Module 04 Enumeration\LDAP Enumeration Tools\Active Directory Explorer
click agree
in connect to field put in this example windos server 2016 so 10.10.10.16
click ok
expand DC=CEH, DC=com, and CN=Users
Click any username (in the left pane) to display its properties in the right pane.
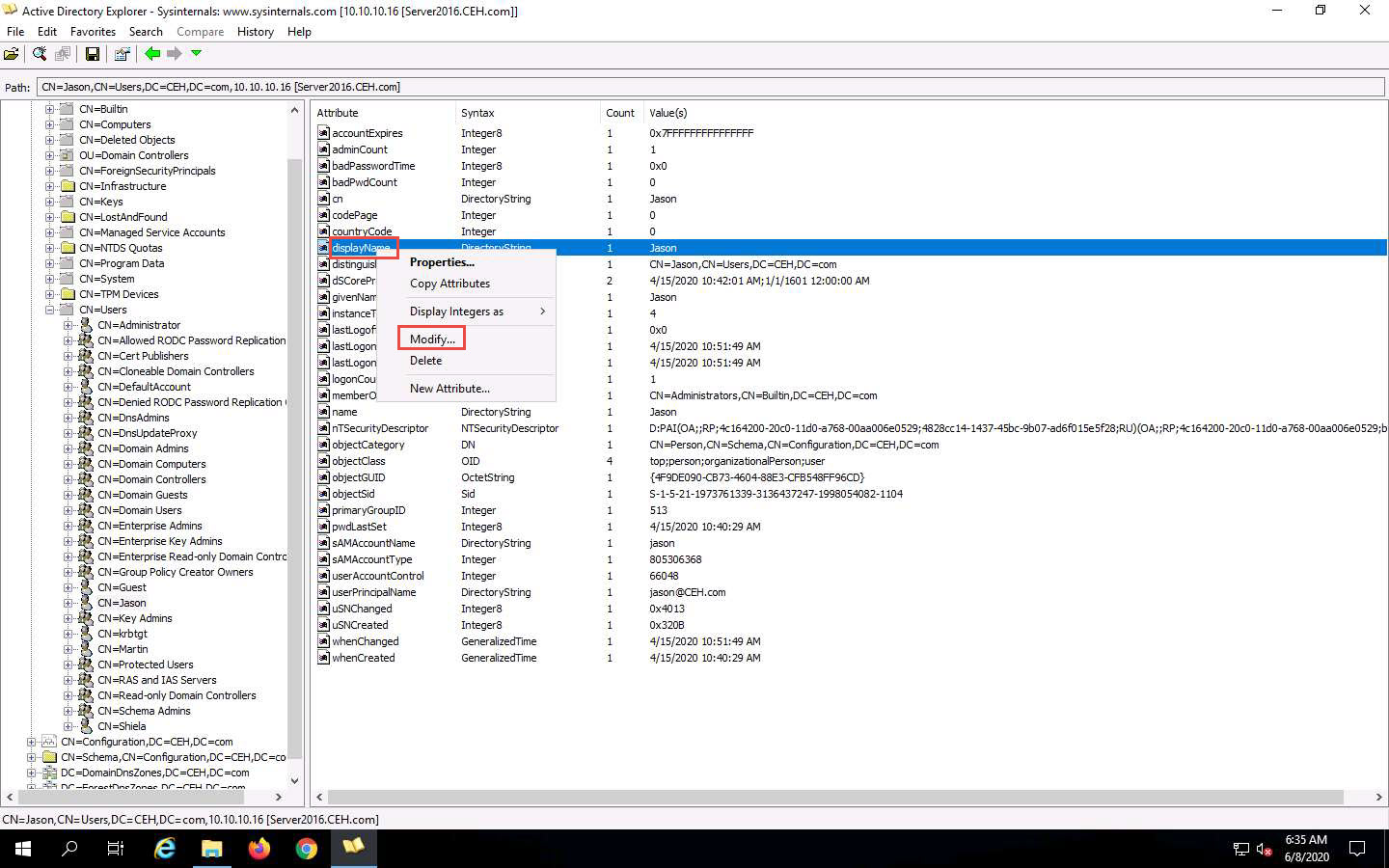
Right-click any attribute in the right pane click modify to modify user profile
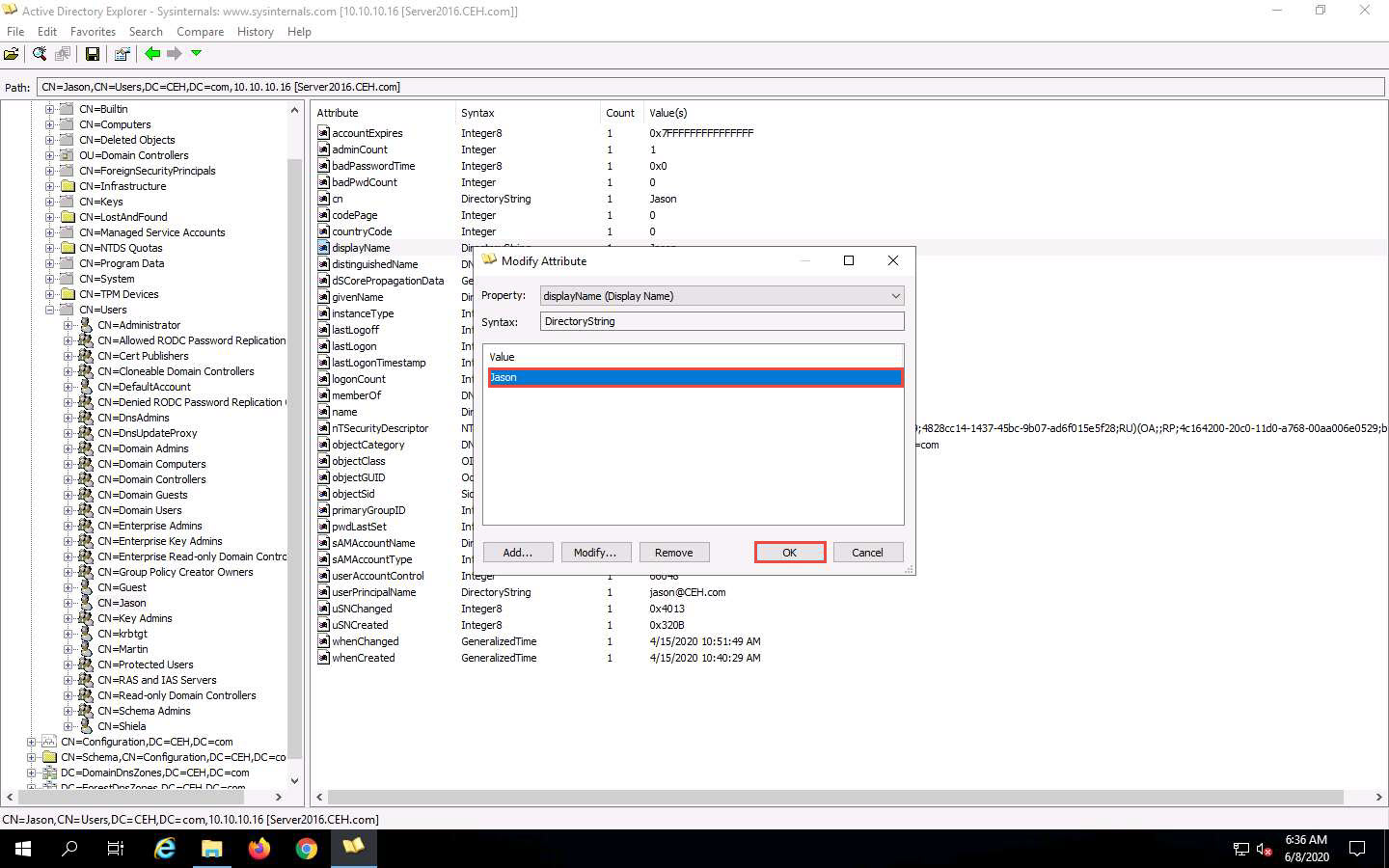
you can edit any info
Lab Scenario
As a professional ethical hacker or penetration tester, the next step after SNMP enumeration is to perform LDAP enumeration to access directory listings within Active Directory or other directory services. Directory services provide hierarchically and logically structured information about the components of a network, from lists of printers to corporate email directories. In this sense, they are similar to a company’s org chart.
LDAP enumeration allows you to gather information about usernames, addresses, departmental details, server names, etc.
Lab Objectives
- Perform LDAP enumeration using Active Directory Explorer (AD Explorer)
Overview of LDAP Enumeration
LDAP (Lightweight Directory Access Protocol) is an Internet protocol for accessing distributed directory services over a network. LDAP uses DNS (Domain Name System) for quick lookups and fast resolution of queries. A client starts an LDAP session by connecting to a DSA (Directory System Agent), typically on TCP port 389, and sends an operation request to the DSA, which then responds. BER (Basic Encoding Rules) is used to transmit information between the client and the server. One can anonymously query the LDAP service for sensitive information such as usernames, addresses, departmental details, and server names.
Task 1: Perform LDAP Enumeration using Active Directory Explorer (AD Explorer)
Active Directory Explorer (AD Explorer) is an advanced Active Directory (AD) viewer and editor. It can be used to navigate an AD database easily, define favorite locations, view object properties and attributes without having to open dialog boxes, edit permissions, view an object’s schema, and execute sophisticated searches that can be saved and re-executed.
Here, we will use the AD Explorer to perform LDAP enumeration on an AD domain and modify the domain user accounts.
In the Windows Server 2019 machine, navigate to Z:\CEHv11 Module 04 Enumeration\LDAP Enumeration Tools\Active Directory Explorer and double-click ADExplorer.exe.
The Active Directory Explorer License Agreement window appears; click Agree.
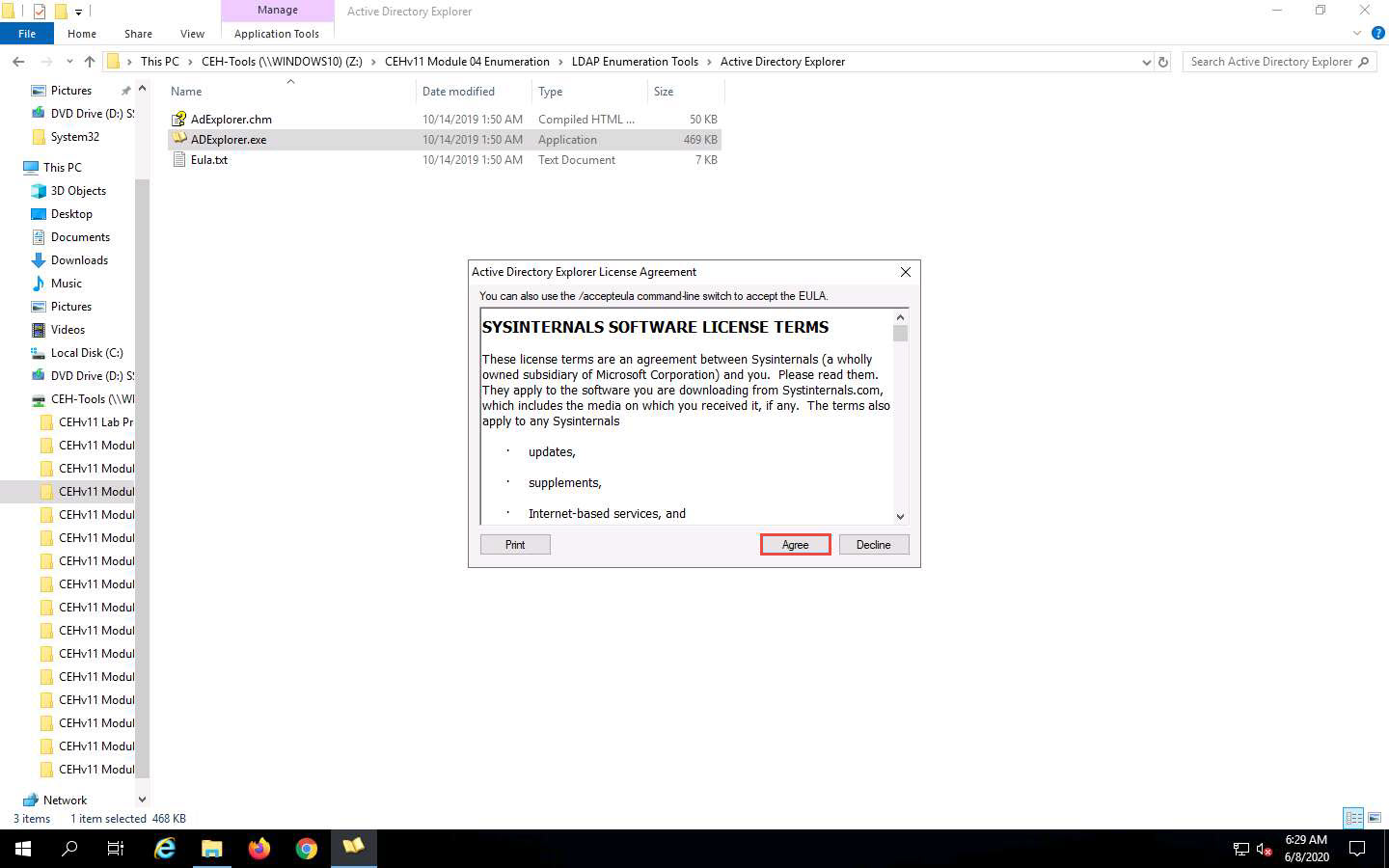
The Connect to Active Directory pop-up appears; type the IP address of the target in the Connect to field (in this example, we are targeting the Windows Server 2016 machine: 10.10.10.16) and click OK.
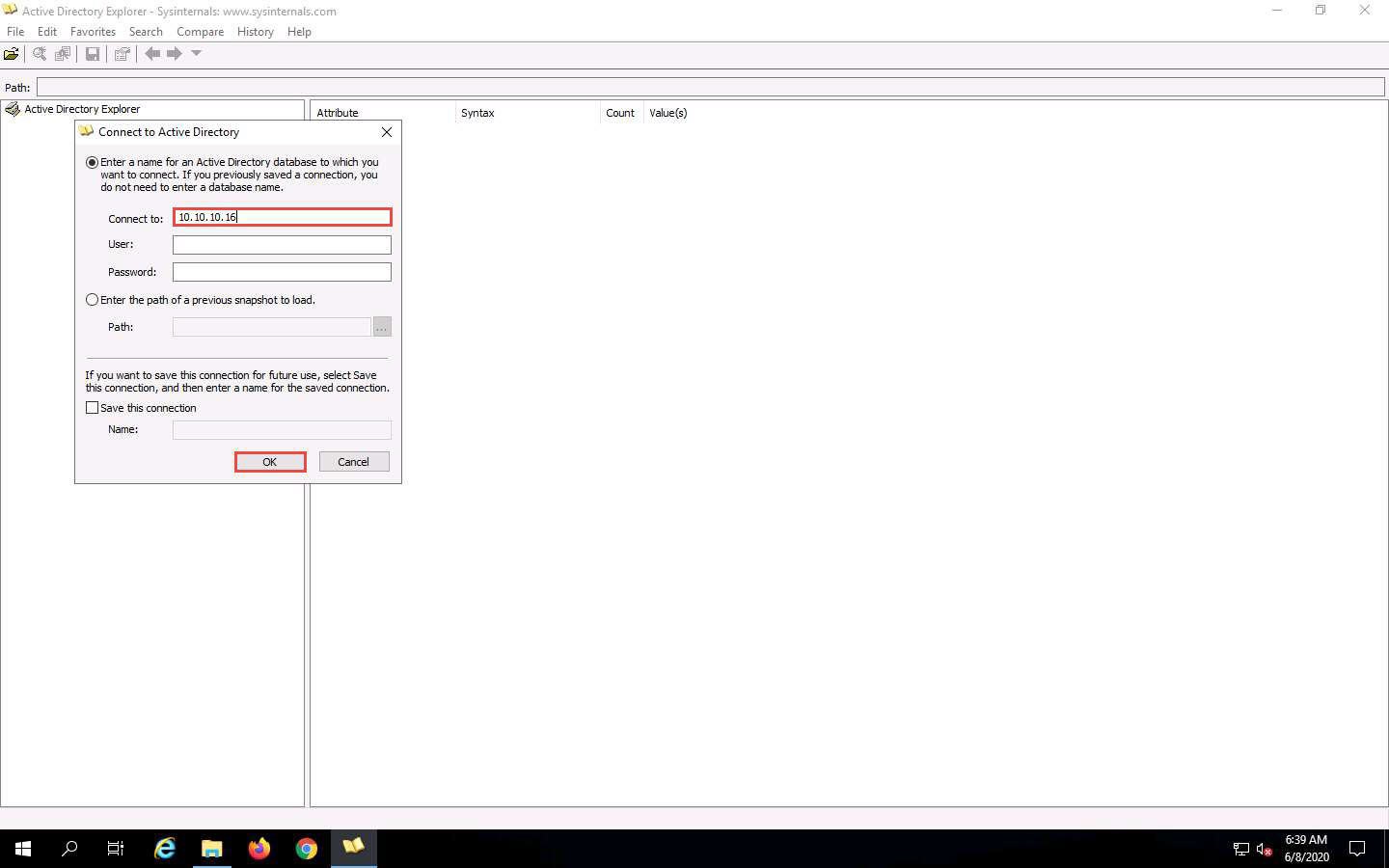
The Active Directory Explorer displays the active directory structure in the left pane, as shown in the screenshot.
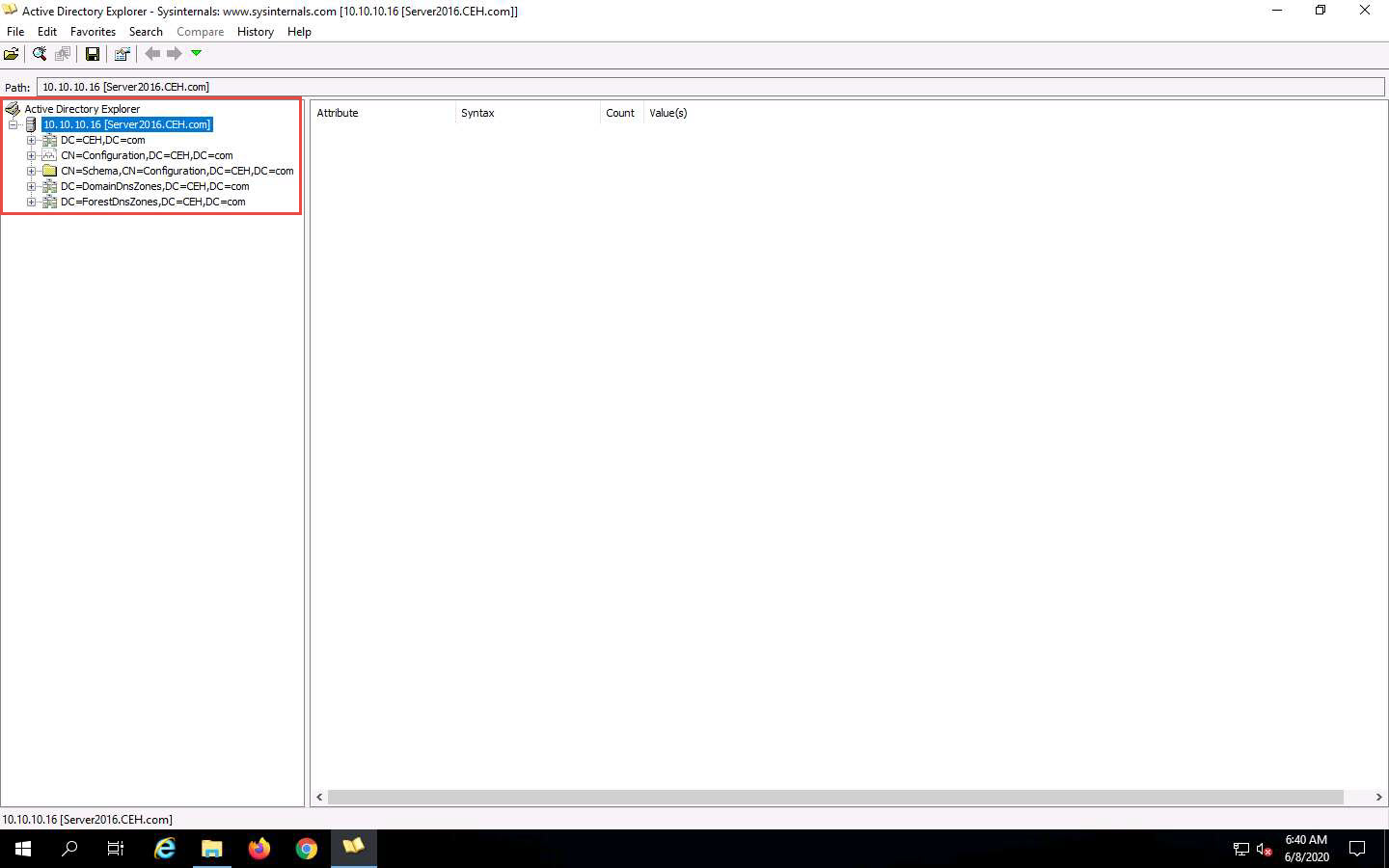
Now, expand DC=CEH, DC=com, and CN=Users by clicking “+” to explore domain user details.
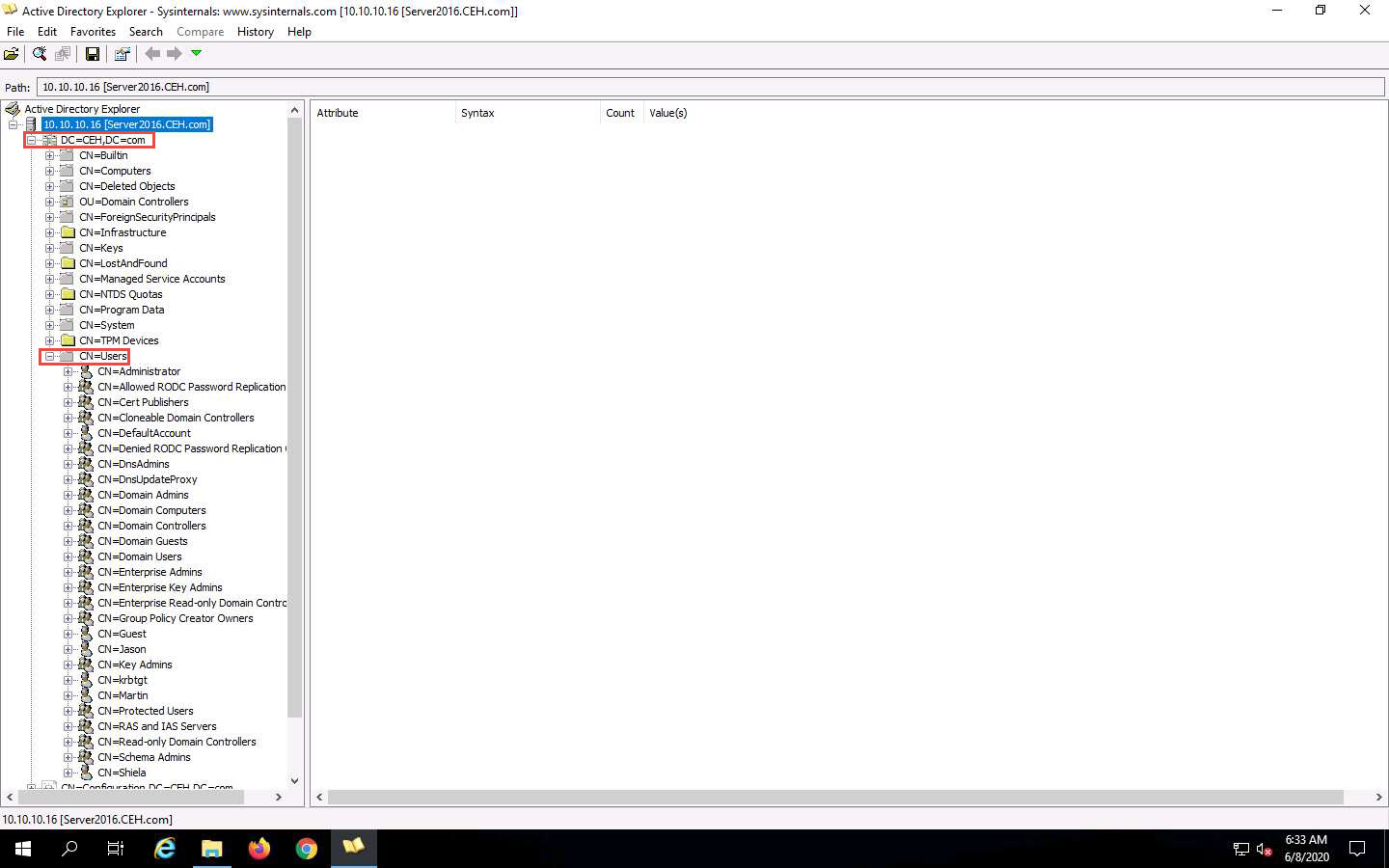
Click any username (in the left pane) to display its properties in the right pane.
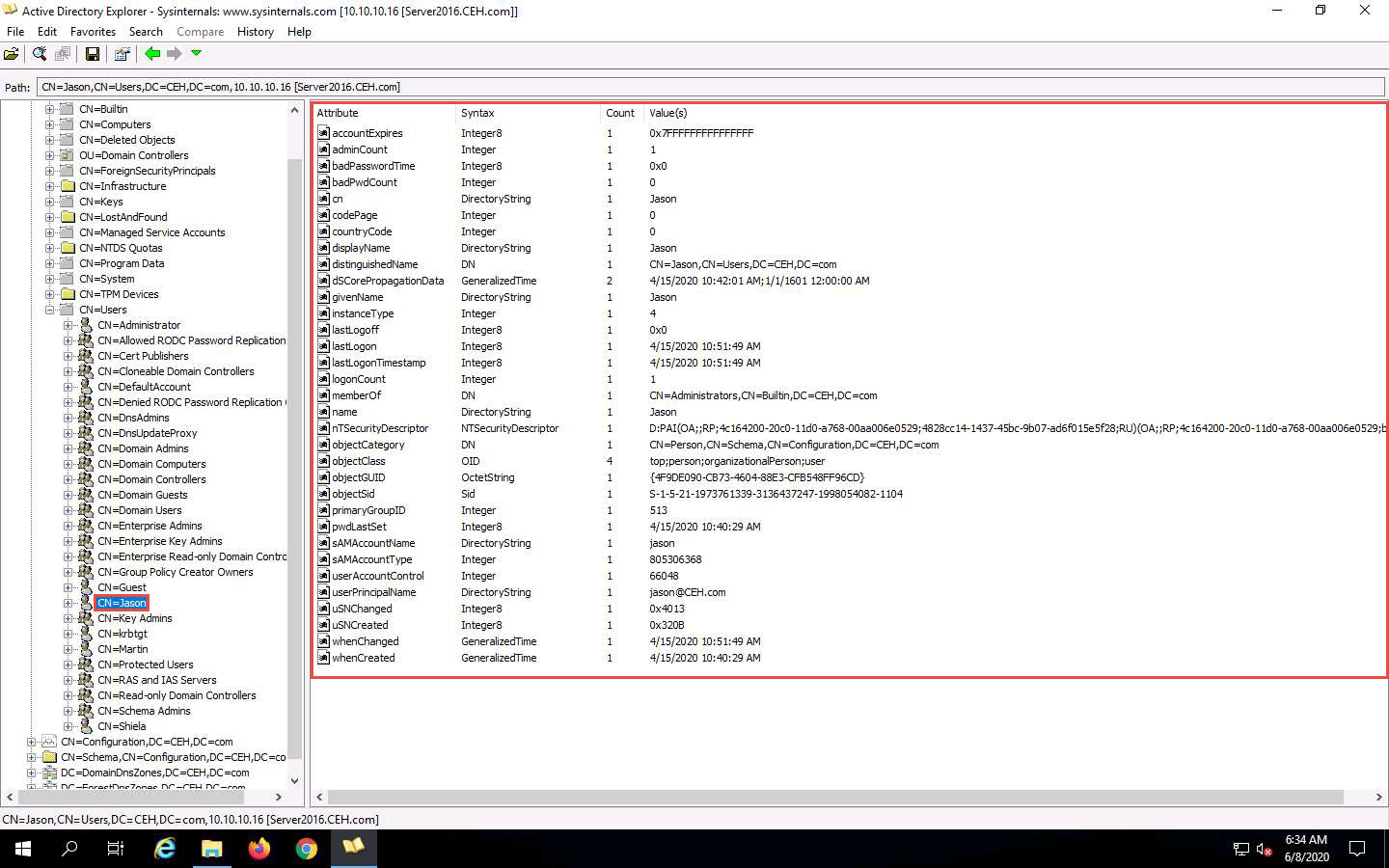
Right-click any attribute in the right pane (in this case, displayName) and click Modify… from the context menu to modify the user’s profile.
The Modify Attribute window appears. First, select the username under the Value section, and then click the Modify… button. The Edit Value pop-up appears. Rename the username in the Value data field and click OK to save the changes.
You can read and modify other user profile attributes in the same way.
This concludes the demonstration of performing LDAP enumeration using AD Explorer.
You can also use other LDAP enumeration tools such as Softerra LDAP Administrator (https://www.ldapadministrator.com), LDAP Admin Tool (https://www.ldapsoft.com), LDAP Account Manager (https://www.ldap-account-manager.org), LDAP Search (https://securityxploded.com), and JXplorer (http://www.jxplorer.org) to perform LDAP enumeration on the target.
Close all open windows and document all the acquired information.
Comments
Post a Comment