Lab 1: Perform S3 Bucket Enumeration using Various S3 Bucket Enumeration Tools
Lab 1: Perform S3 Bucket Enumeration using Various S3 Bucket Enumeration Tools
Lab Scenario
As an ethical hacker, you must try to obtain as much information as possible about the target cloud environment using various enumeration tools. This lab will demonstrate various S3 bucket enumeration tools that can help you in extracting the list of publicly available S3 buckets.
Lab Objectives
- Enumerate S3 buckets using lazys3
- Enumerate S3 buckets using S3Scanner
Overview of Enumeration Tools
Enumeration tools are used to collect detailed information about target systems to exploit them. Information collected by S3 enumeration tools consists of a list of misconfigured S3 buckets that are available publicly. Attackers can exploit these buckets to gain unauthorized access to them. Moreover, they can modify, delete, and exfiltrate the bucket content.
Task 1: Enumerate S3 Buckets using lazys3
lazys3 is a Ruby script tool that is used to brute-force AWS S3 buckets using different permutations. This tool obtains the publicly accessible S3 buckets and also allows you to search the S3 buckets of a specific company by entering the company name.
Click Parrot Security to switch to the Parrot Security machine.
In the login page, the attacker username will be selected by default. Enter password as toor in the Password field and press Enter to log in to the machine.
Click the MATE Terminal icon at the top of the Desktop window to open a Terminal window.
A Parrot Terminal window appears. In the terminal window, type sudo su and press Enter to run the programs as a root user.
If a Question pop-up window appears asking for you to update the machine, click No to close the window.
In the [sudo] password for attacker field, type toor as a password and press Enter.
The password that you type will not be visible.
Now, type cd and press Enter to jump to the root directory.
In the terminal window, type cd lazys3 and press Enter to navigate to the cloned repository.
We have already downloaded lazys3 tool in the Lab setup.
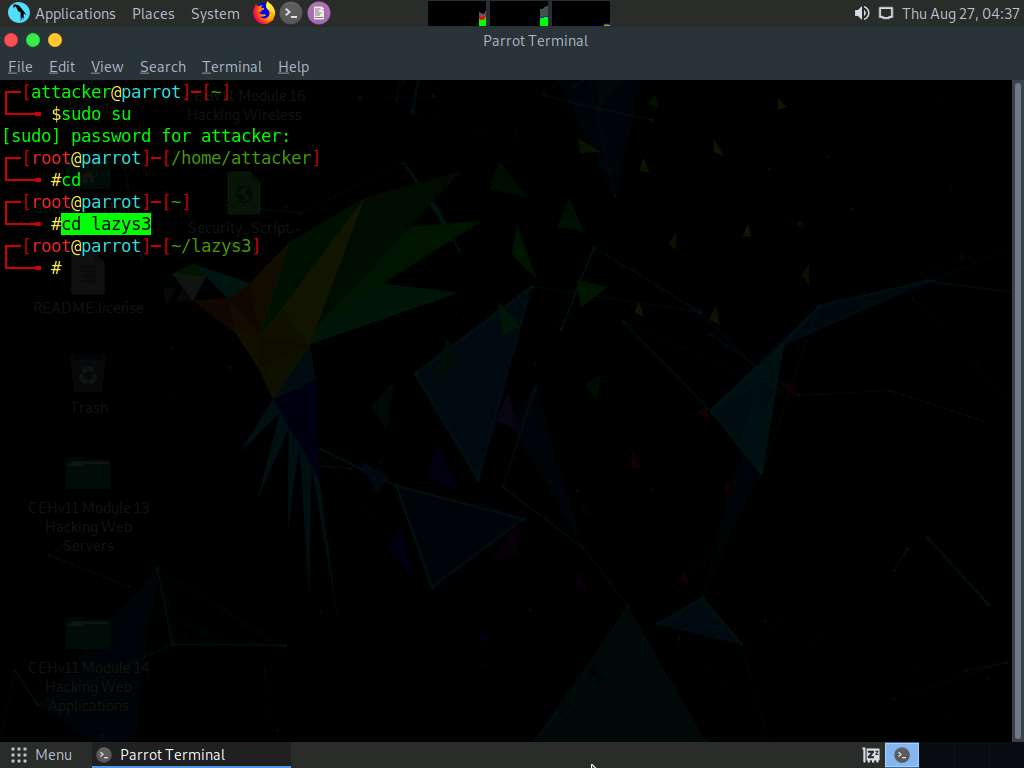
In the lazys3 folder, type ls and press Enter to list the folder content.
The folder content is displayed; here, we will run the lazys3.rb script to find the public S3 buckets.
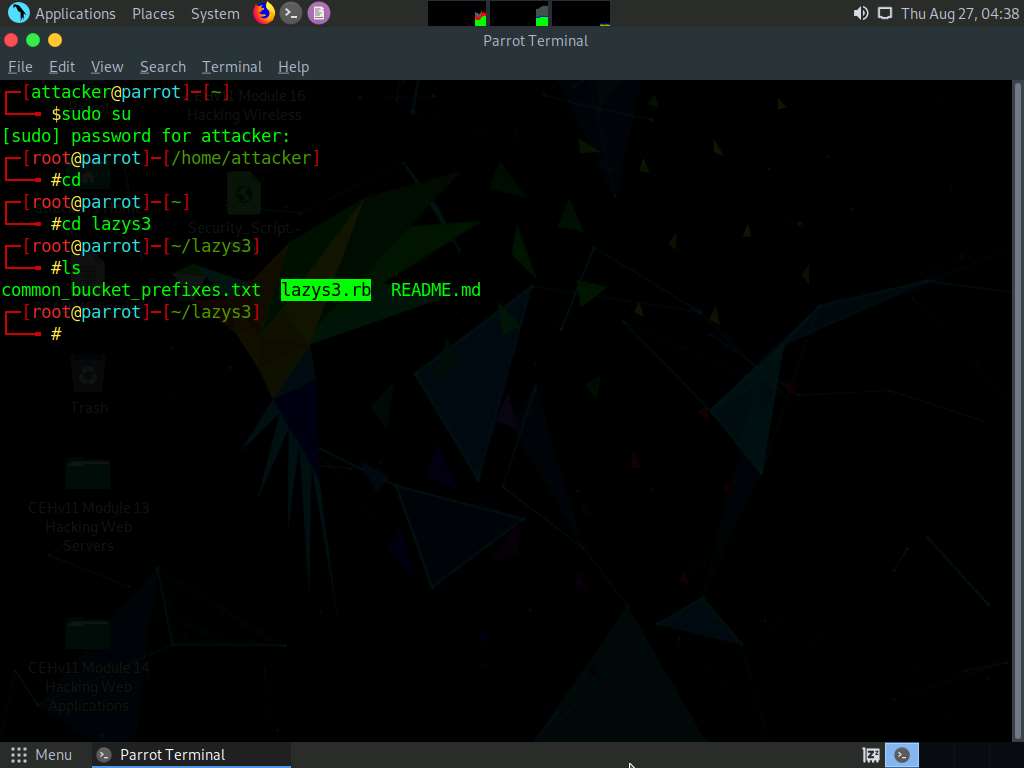
Now, type ruby lazys3.rb and press Enter.
A list of public S3 buckets is displayed, as shown in the screenshot.
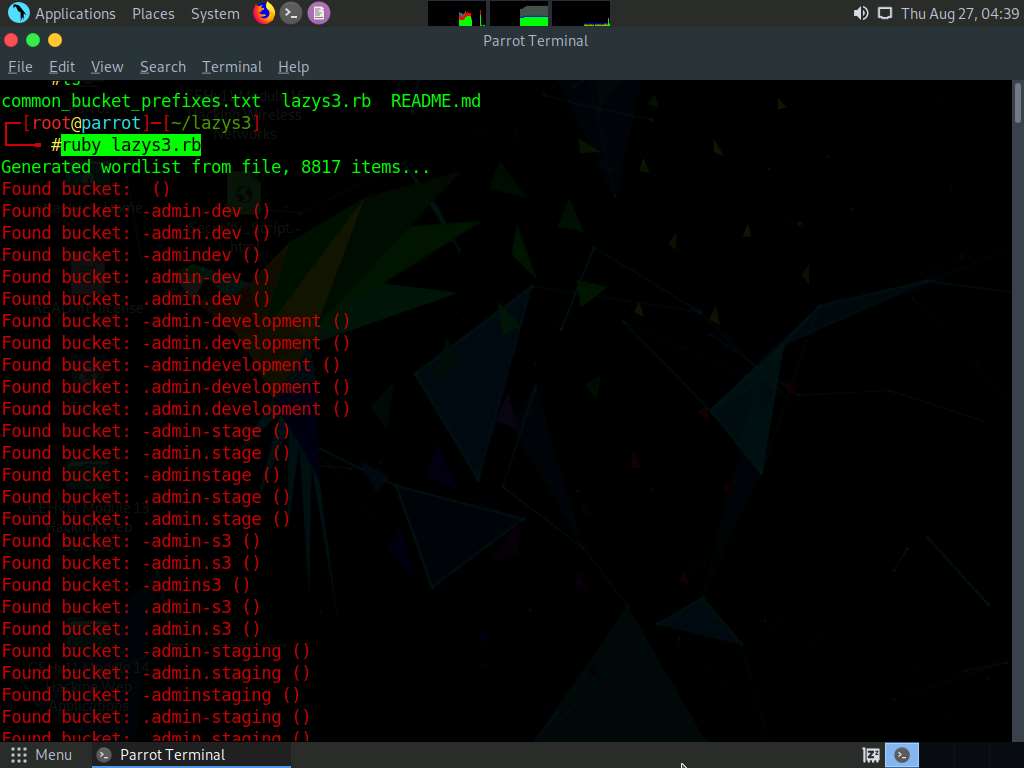
Press Ctrl+Z to stop the script.
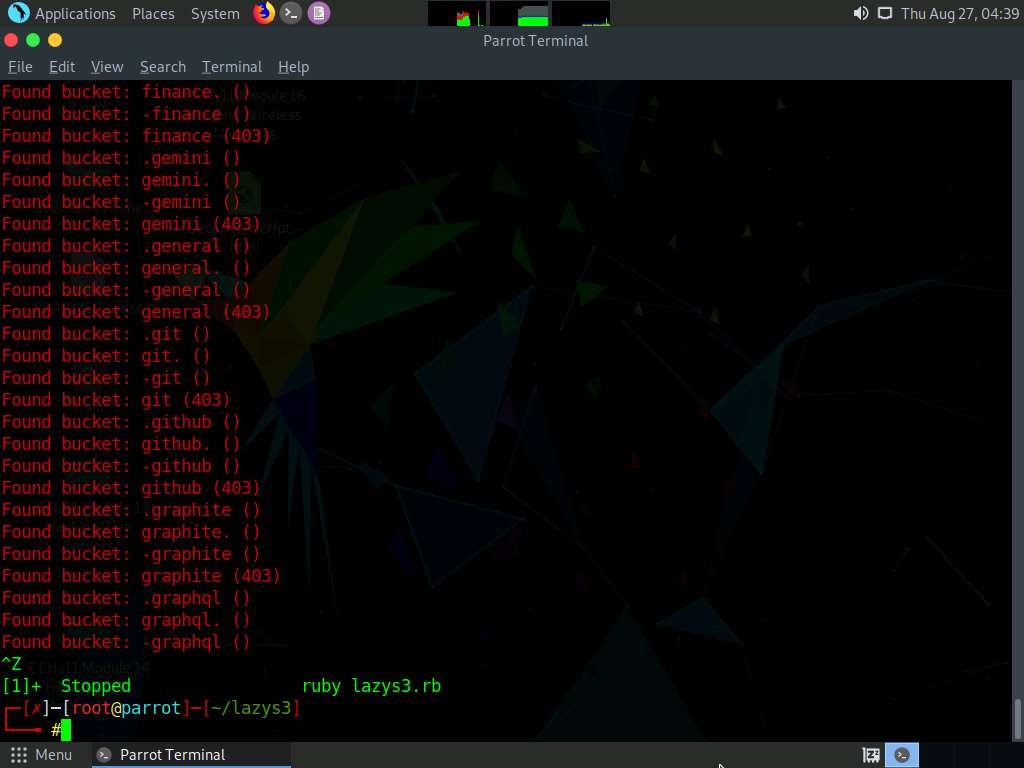
You can search the S3 buckets of specific company. To do so, type ruby lazys3.rb [Company] and press Enter.
Here, the target company name is HackerOne; you can enter the company name of your choice.
The result appears, showing the obtained list of S3 buckets of the specified company.
It will take some time to obtain a complete list of the available S3 buckets.
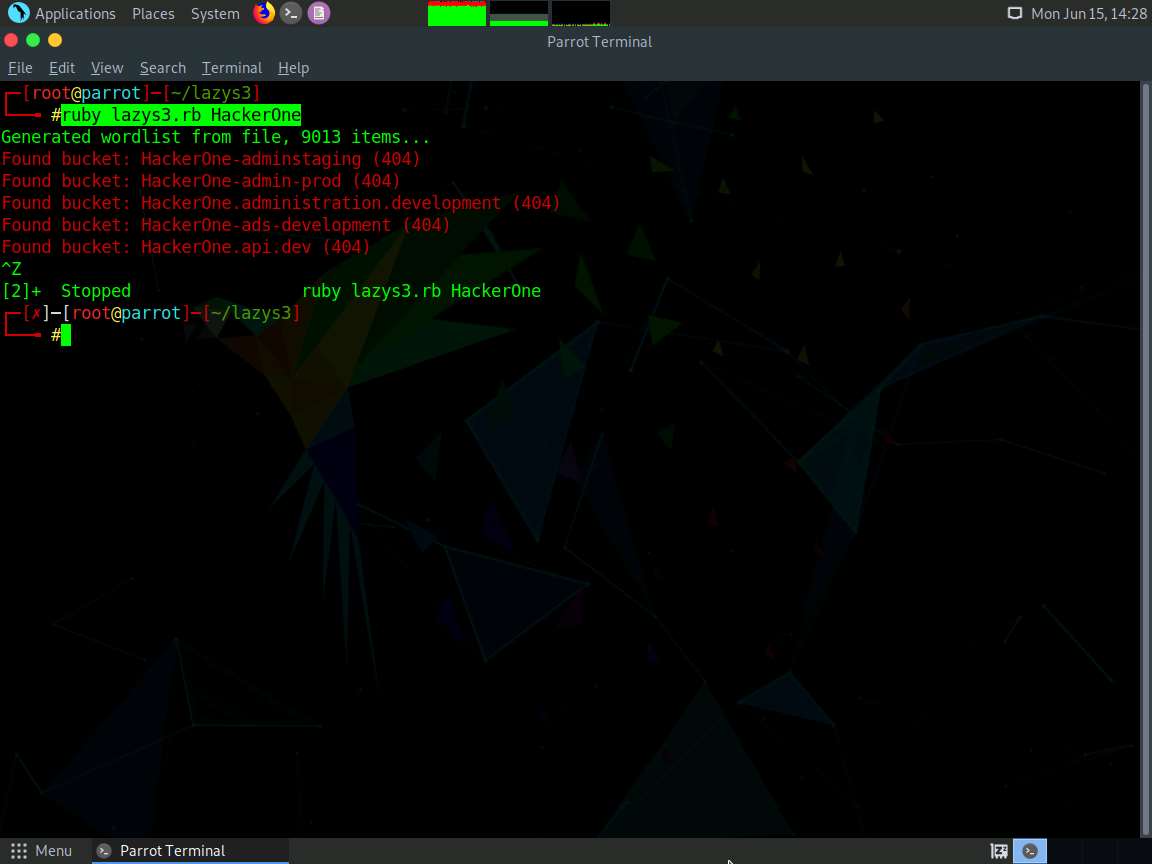
Press Ctrl+Z to stop running the script.
This concludes the demonstration of enumerating public S3 buckets.
Close all open windows and document all the acquired information.
Task 2: Enumerate S3 Buckets using S3Scanner
S3Scanner is a tool that finds the open S3 buckets and dumps their contents. It takes a list of bucket names to check as its input. The S3 buckets that are found are output to a file. The tool also dumps or lists the contents of “open” buckets locally.
Here, we will use the S3Scanner tool to enumerate open S3 buckets.
Click the MATE Terminal icon in the menu to launch the terminal.
A Parrot Terminal window appears. In the terminal window, type sudo su and press Enter to run the programs as a root user.
In the [sudo] password for attacker field, type toor as a password and press Enter.
The password that you type will not be visible.
Now, type cd and press Enter to jump to the root directory.
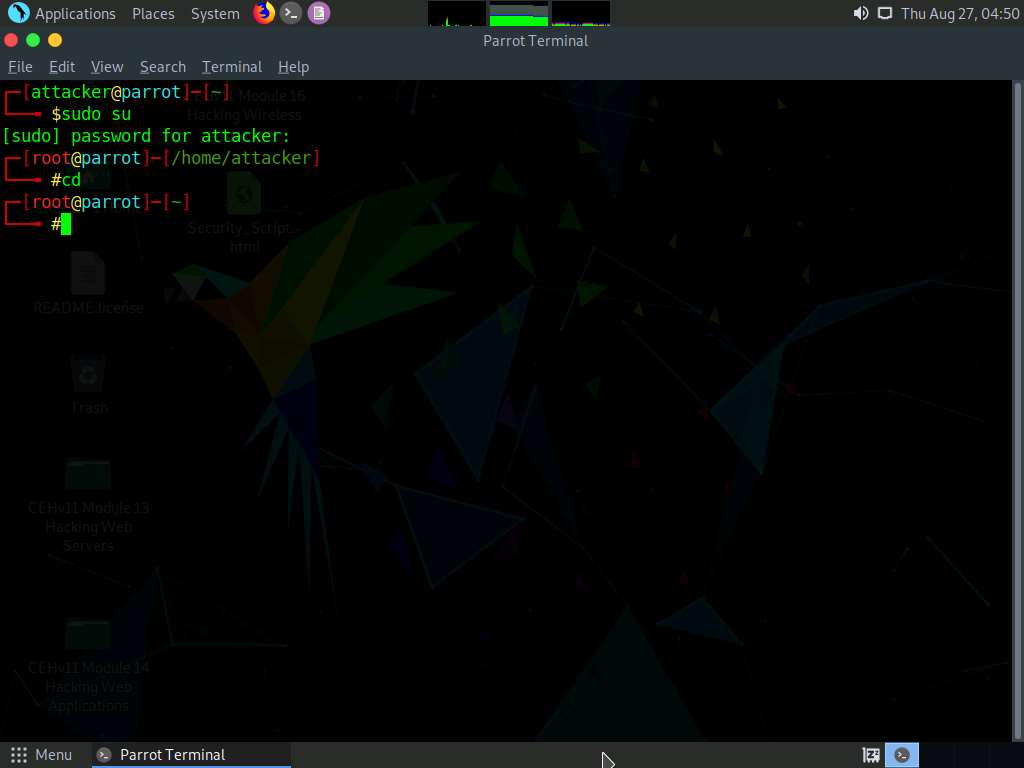
Type cd S3Scanner and press Enter to navigate to the cloned repository.
By default, the tool is cloned to the root directory.
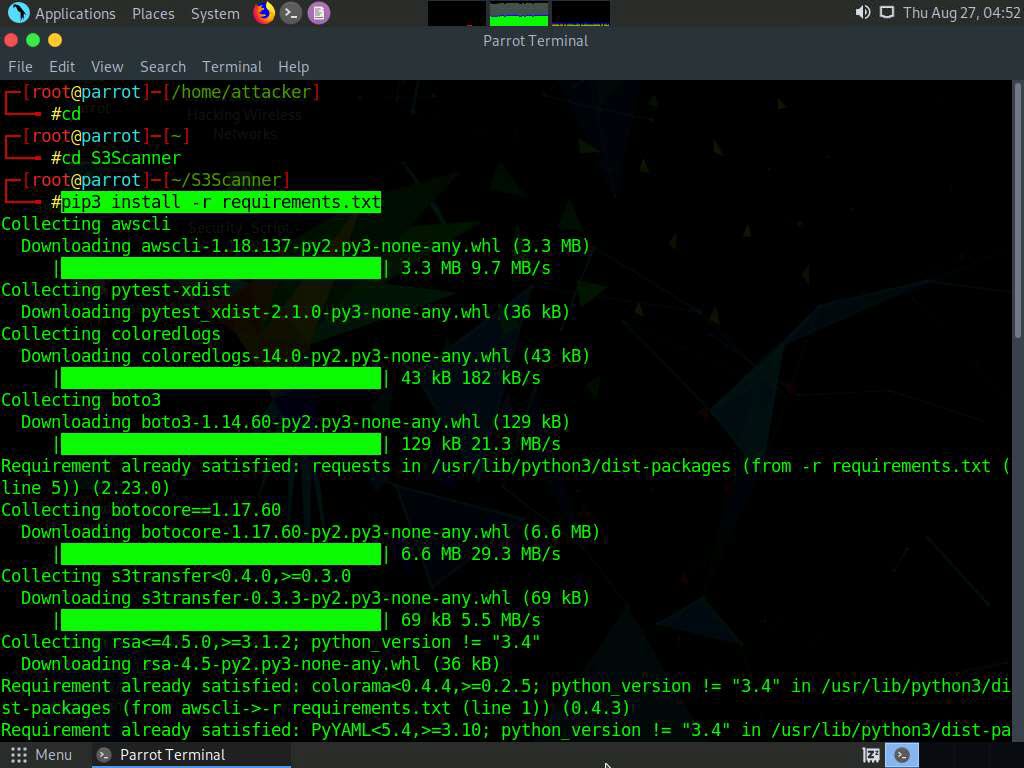
In the S3Scanner folder, type pip3 install -r requirements.txt and press Enter to install the required dependencies.
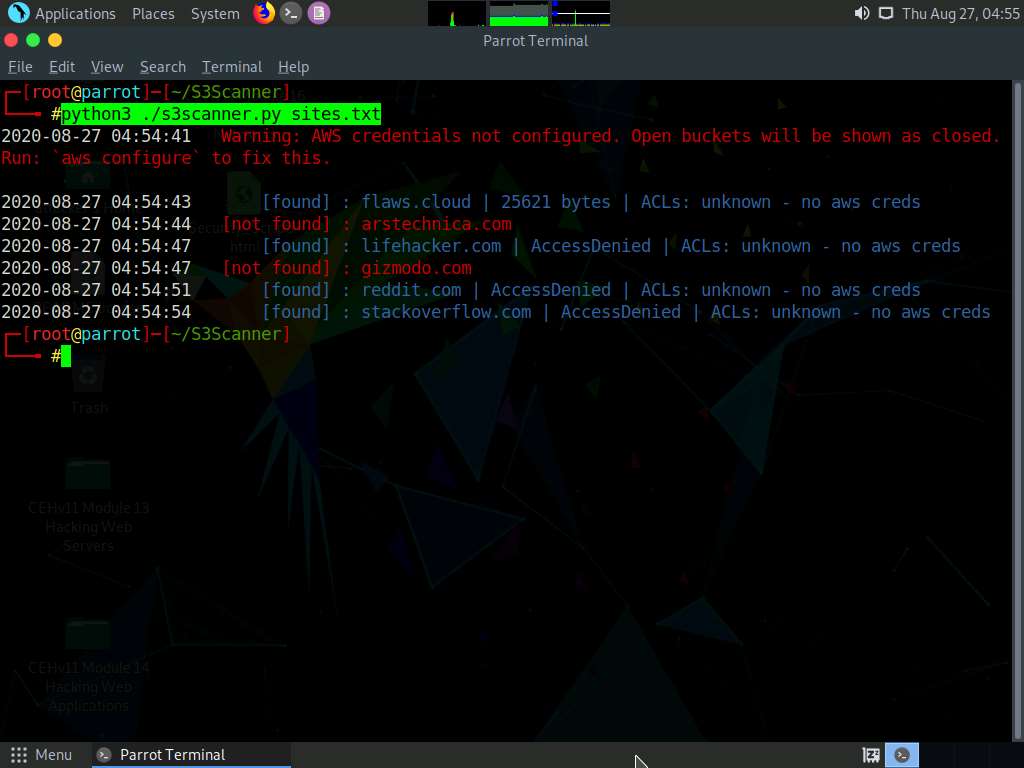
After the successful installation of the dependencies, in the terminal window, type python3 ./s3scanner.py sites.txt and press Enter to run the tool.
Here, sites.txt is a text file containing the target website URL that is scanned for open S3 buckets. You can edit the sites.txt file to enter the target website URL of your choice.
The result appears, displaying a list of public S3 buckets, as shown in the screenshot.
You might encounter the following error: “AWS credentials not configured.” Ignore the error, as we will install and configure the AWS CLI in the next lab.
Apart from the aforementioned command, you can use the S3Scanner tool to perform the following functions:
Dump all open buckets and log both open and closed buckets in found.txt:
python3 ./s3scanner.py --include-closed --out-file found.txt --dump names.txt
Just log open buckets in the default output file (buckets.txt):
python3 ./s3scanner.py names.txt
Save the file listings of all open buckets to a file:
python ./s3scanner.py --list names.txt
This concludes the demonstration of enumerating S3 buckets using the S3Scanner tool.
You can also use other S3 bucket enumeration tools such as S3Inspector (https://github.com), s3-buckets-bruteforcer (https://github.com), Mass3 (https://github.com), Bucket Finder (https://digi.ninja), and s3recon (https://github.com) to perform S3 bucket enumeration for a target website or company.
Close all open windows and document all the acquired information.
Comments
Post a Comment