Lab 1: Perform Footprinting using Various Footprinting Techniques
Lab 1: Perform Footprinting using Various Footprinting Techniques
Module 18: IoT and OT Hacking
Lab 1: Perform Footprinting using Various Footprinting Techniques
Task 1: Gather Information using Online Footprinting Tools
go to whois.com/whois
dont forget /whois
search site (www.oasis-open.org)
This information is about the organization that has developed the MQTT protocol, and it might help keep track of the modifications and version changes of the target protocol.
Whois lookup reveals available information on a hostname, IP address, or domain.
Now, open a new tab, and click on https://www.exploit-db.com/google-hacking-database
search SCADA hit enter
displays the Google dork related to SCADA
go to google.com
search: "login" intitle:"scada login" = this is based on what was found on hacking database
if it says something else just input that into google.
you are looking for a search result like this
SCADA :: seamtec SCADA login ::
if you cant find it try searching: login" intitle:"scada login
click on the scada:: s thing and open the login web page
Similarly, you can use advanced search operators such as intitle:"index of" scada to search sensitive SCADA directories that are exposed on sites.
new tab
open: https://account.shodan.io/login
login bentobox
click shodan in top left corner
type port:1883
Port 1883 is the default MQTT port; 1883 is defined by IANA as MQTT over TCP.
Click on any IP address to view its detailed information.
displaying information regarding Ports, Services, Hostnames, ASN,
Similarly, you can gather additional information on a target device using the following Shodan filters:
Search for Modbus-enabled ICS/SCADA systems:
port:502
Search for SCADA systems using PLC name:
“Schneider Electric”
Search for SCADA systems using geolocation:
SCADA Country:"US"
Using Shodan, you can obtain the details of SCADA systems that are used in water treatment plants, nuclear power plants, HVAC systems, electrical transmission systems, home heating systems, etc.
Lab Scenarios
As a professional ethical hacker or pen tester, your first step is to gather maximum information about the target IoT and OT devices by performing footprinting through search engines, advanced Google hacking, Whois lookup, etc.
The first step in IoT and OT device hacking is to extract information such as IP address, protocols used (MQTT, ModBus, ZigBee, BLE, 5G, IPv6LoWPAN, etc.), open ports, device type, geolocation of the device, manufacturing number, and manufacturer of the device.
Lab Objectives
- Gather information using online footprinting tools
Overview of Footprinting Techniques
Footprinting techniques are used to collect basic information about the target IoT and OT platforms to exploit them. Information collected through footprinting techniques includes IP address, hostname, ISP, device location, banner of the target IoT device, FCC ID information, certification granted to the device, etc.
Task 1: Gather Information using Online Footprinting Tools
The information regarding the target IoT and OT devices can be acquired using various online sources such as Whois domain lookup, advanced Google hacking, and Shodan search engine. The gathered information can be used to scan the devices for vulnerabilities and further exploit them to launch attacks.
In this task, we will focus on performing footprinting on the MQTT protocol, which is a machine-to-machine (M2M)/“Internet of Things” connectivity protocol. It is useful for connections with remote locations where a small code footprint is required and/or network bandwidth is at a premium.
You can also select a protocol or device of your choice to perform footprinting on it.
Click on Windows 10 to switch to Windows 10 and click on Ctrl+Alt+Delete to activate it. By default, Admin user profile is selected, click Pa$$w0rd to paste the password in the Password field and press Enter to login.
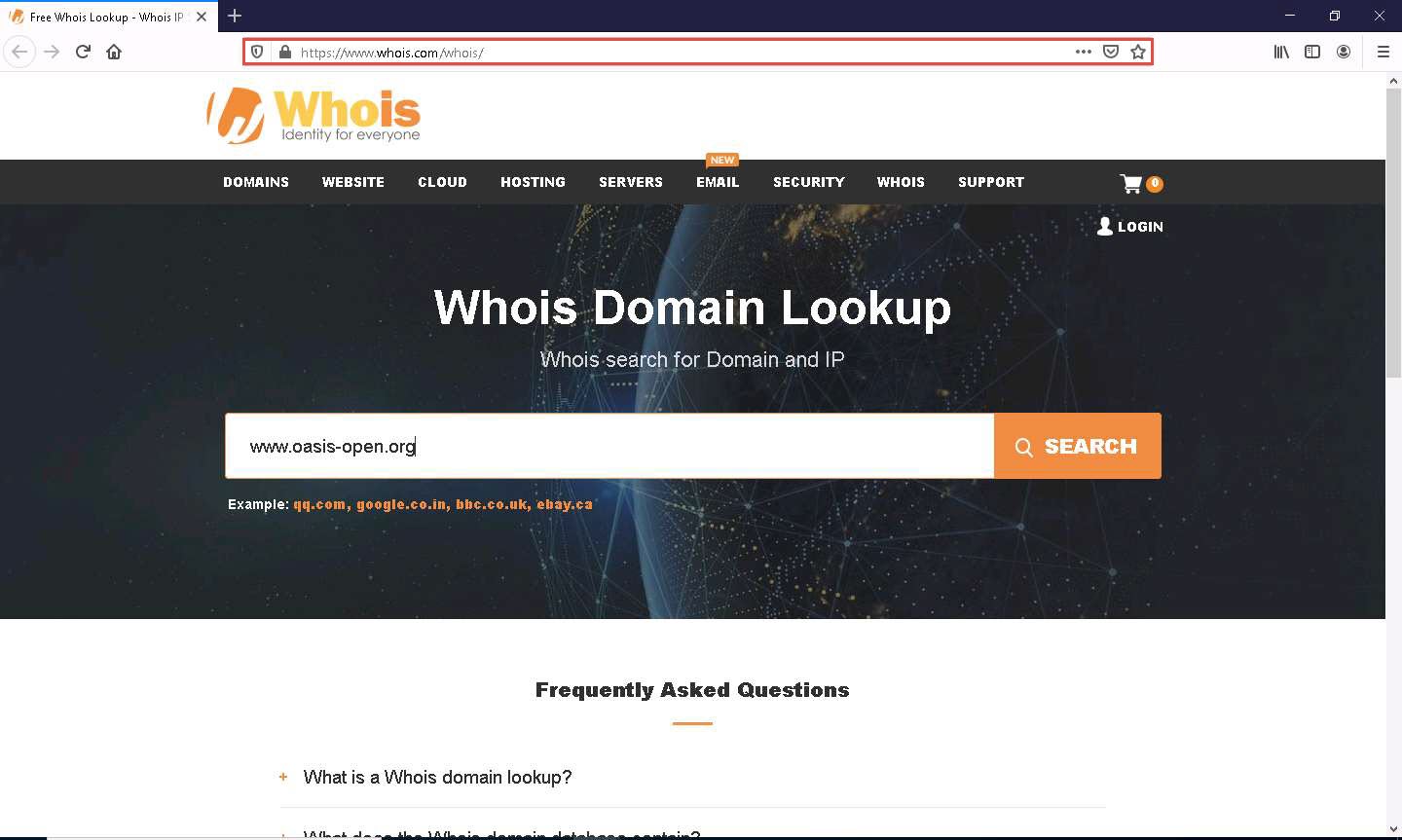
Launch any browser, in this lab we are using Mozilla Firefox. In the address bar of the browser place your mouse cursor and click https://www.whois.com/whois/ and press Enter.
The Whois Domain Lookup page appears; type www.oasis-open.org in the search field and click SEARCH.
Oasis is an organization that has published the MQTT v5.0 standard, which represents a significant leap in the refinement and capability of the messaging protocol that already powers IoT.
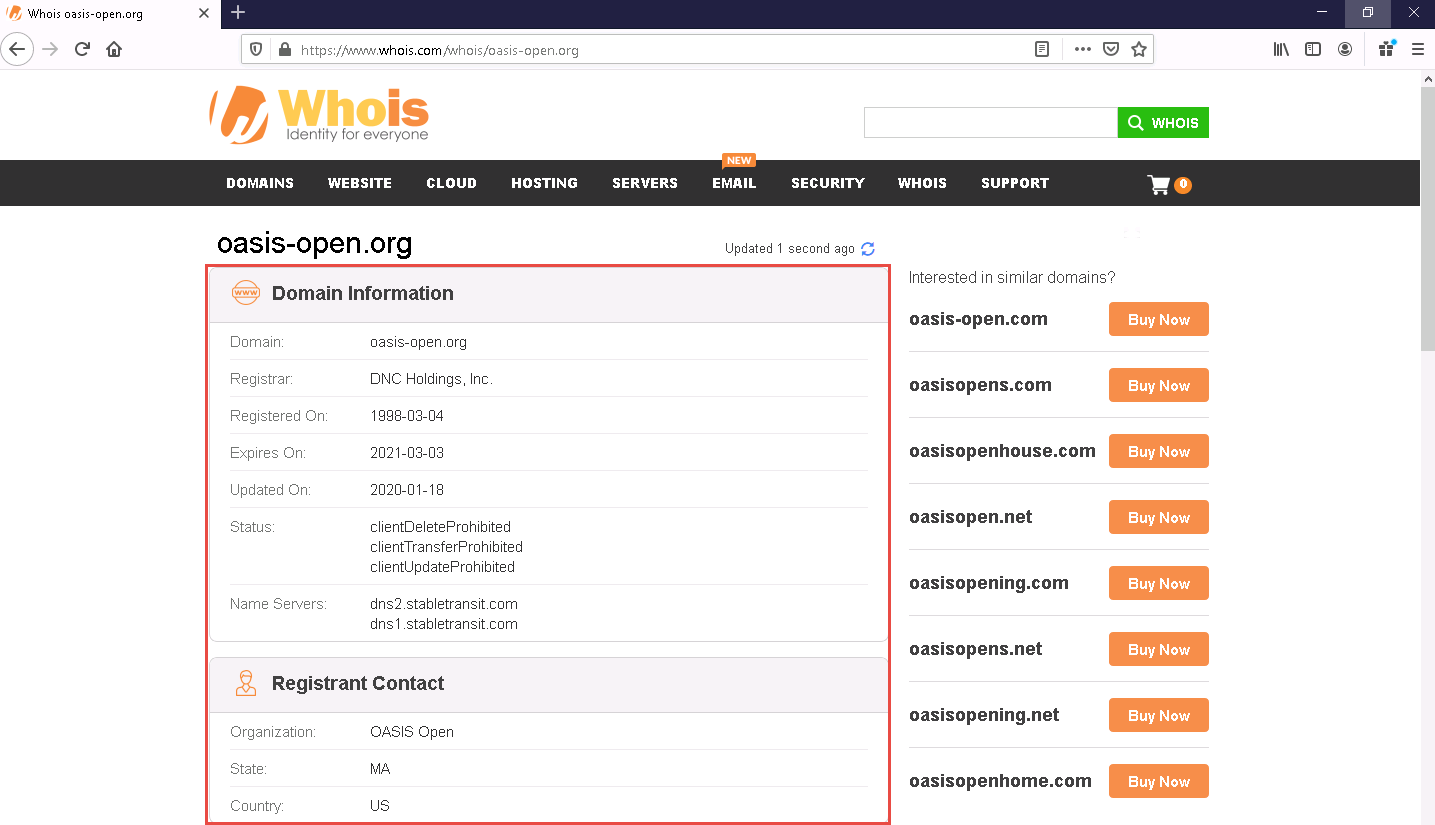
The result appears, displaying the following information, as shown in the screenshots: Domain Information, Registrant Contact, and Raw Whois Data.
This information is about the organization that has developed the MQTT protocol, and it might help keep track of the modifications and version changes of the target protocol.
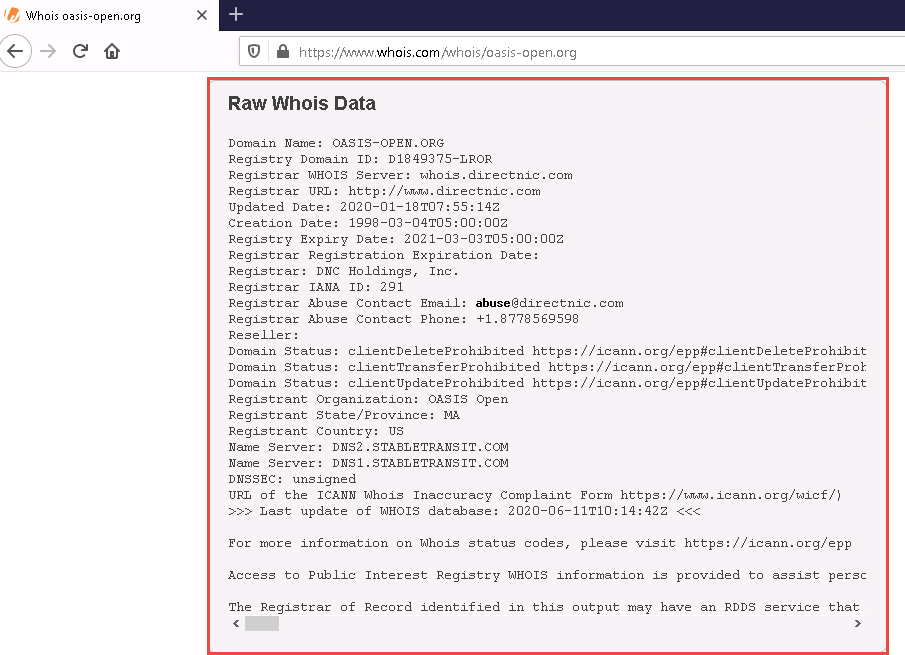
Whois lookup reveals available information on a hostname, IP address, or domain.
Now, open a new tab, and click on https://www.exploit-db.com/google-hacking-database in the address bar, and press Enter.
The Google Hacking Database page appears; type SCADA in the Quick Search field and press Enter.
The result appears, which displays the Google dork related to SCADA, as shown in the screenshot.
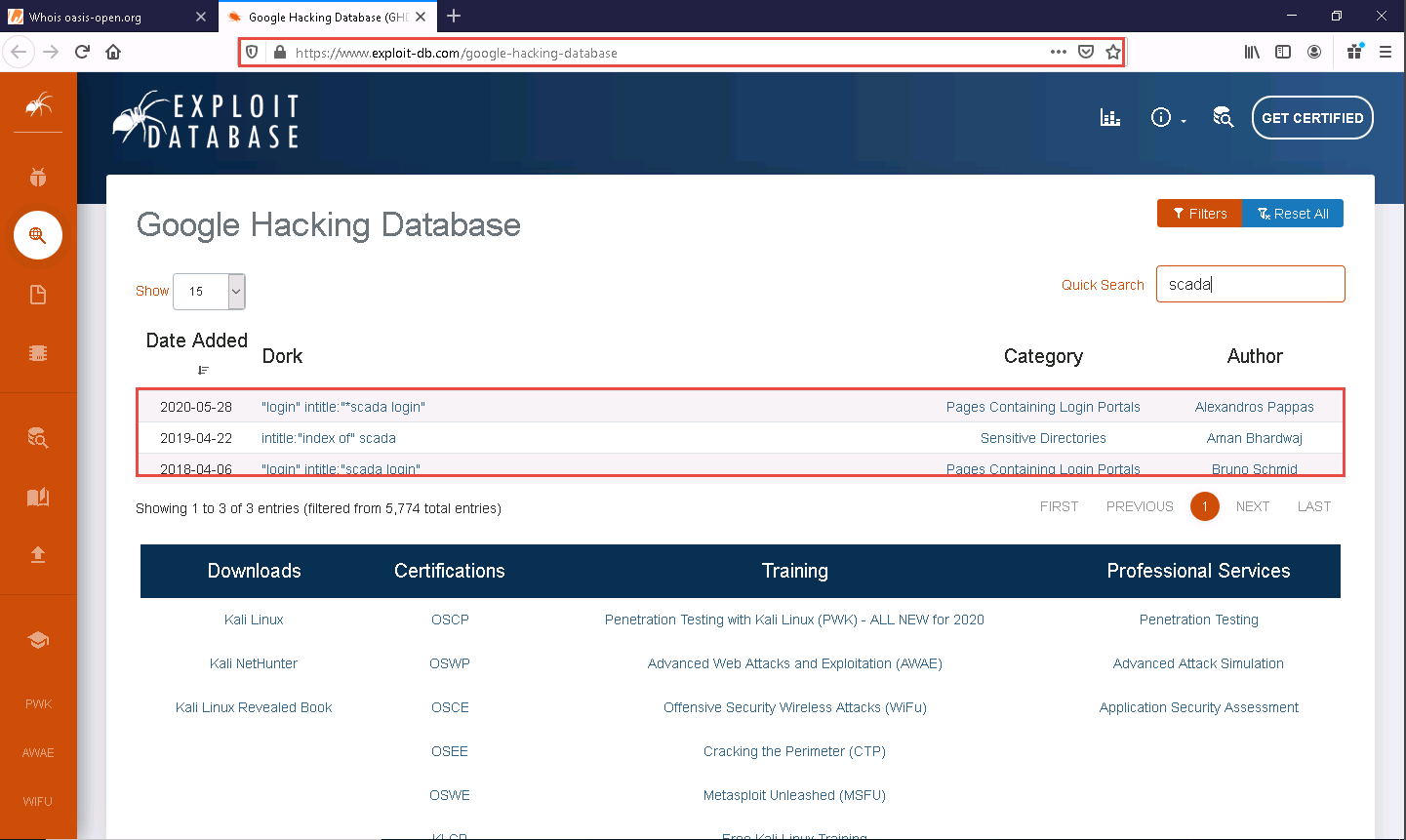
Now, we will use the dorks obtained in the previous step to query results in Google.
open a new tab and click on https://www.google.com in the address bar, and press Enter.
In the search field, type "login" intitle:"scada login" and click the Google Search button.
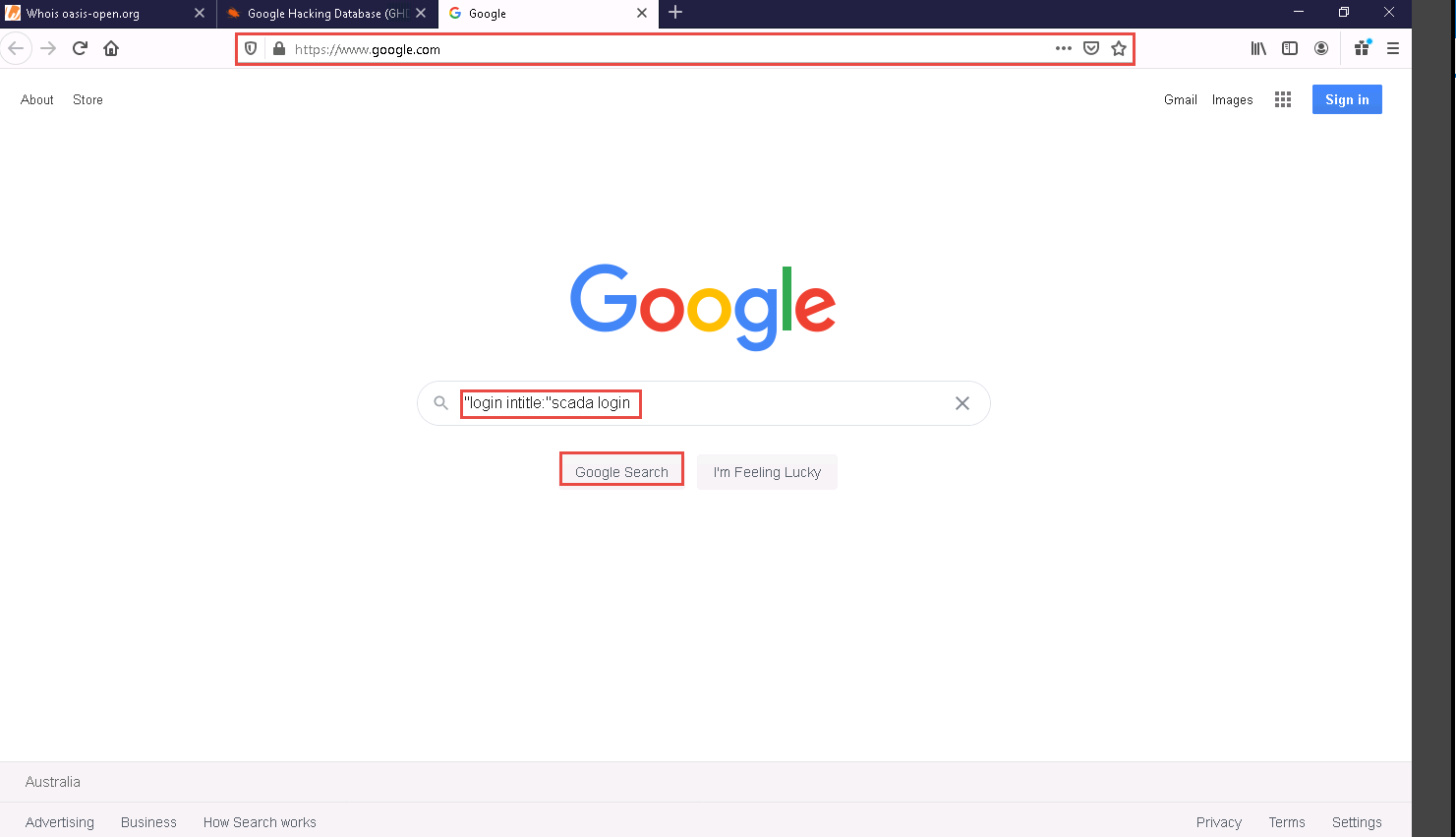
The search result appears; click any link (here, SCADA :: seamtec SCADA login ::).
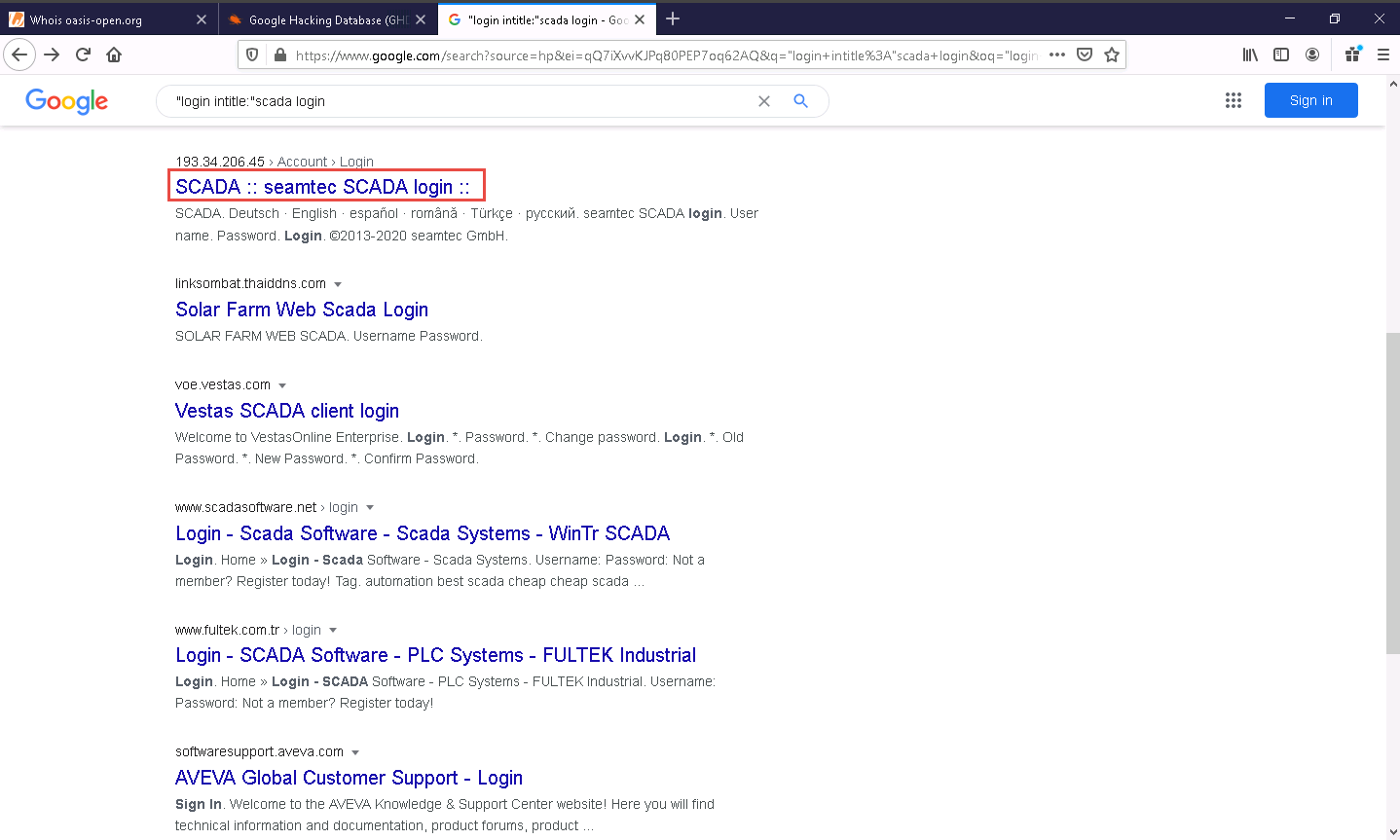
Advanced Google hacking refers to the art of creating complex search engine queries by employing advanced Google operators to extract sensitive or hidden information about a target company from the Google search results.
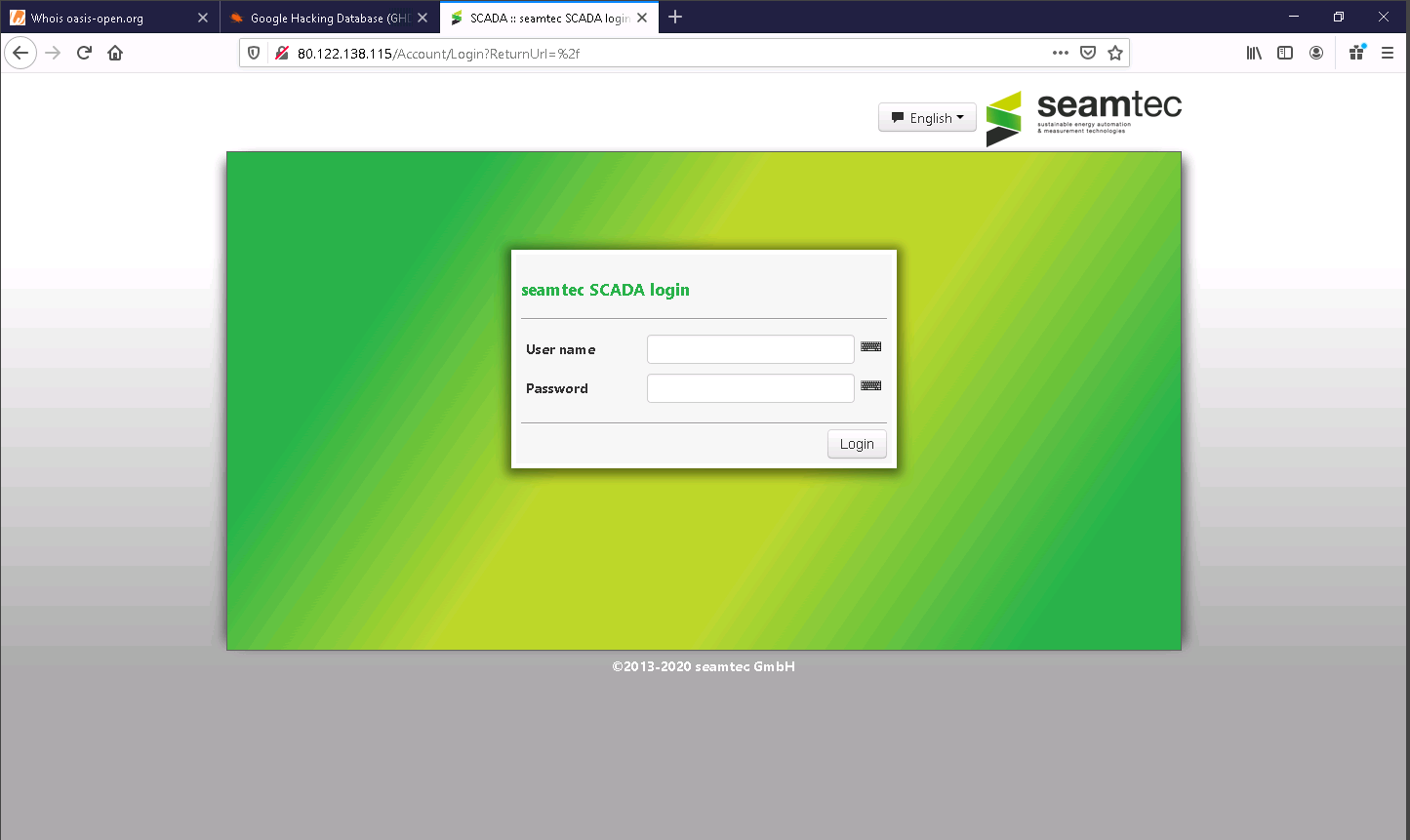
The seamtec SCADA login page appears, as shown in the screenshot.
In the login form, you can brute-force the credentials to gain access to the target SCADA system.
Similarly, you can use advanced search operators such as intitle:"index of" scada to search sensitive SCADA directories that are exposed on sites.
Now, in the browser window, open a new tab click on https://account.shodan.io/login in the address bar, and press Enter.
The Login with Shodan page appears; enter your username and password in the Username and Password fields, respectively; and click Login.
Go to the Register option to register yourself if you do not have an existing account.
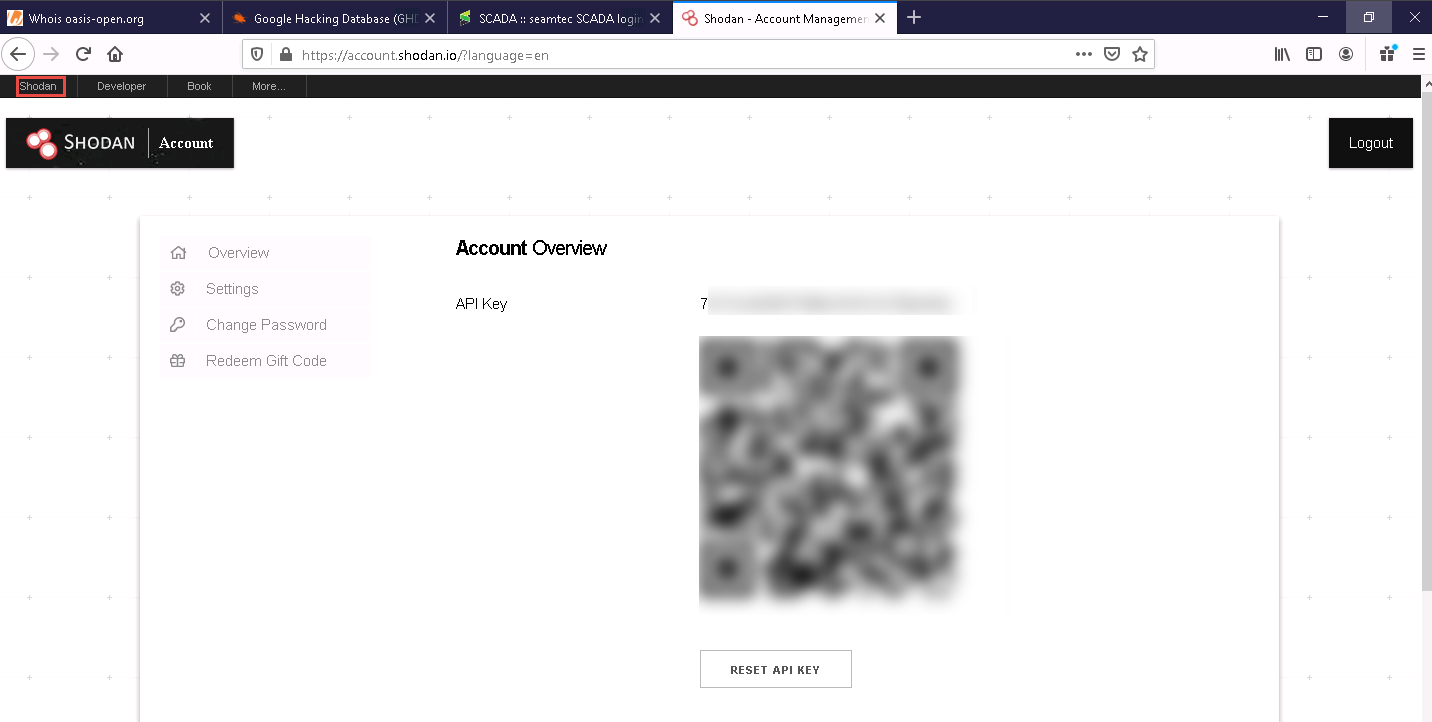
The Account Overview page appears, which displays the account-related information.
If the Would you like Firefox to save this login for shodan.io? notification appears, click Don’t Save.
Click Shodan in the top-left corner of the window.
The Shodan main page appears; type port:1883 in the address bar and press Enter.
Port 1883 is the default MQTT port; 1883 is defined by IANA as MQTT over TCP.
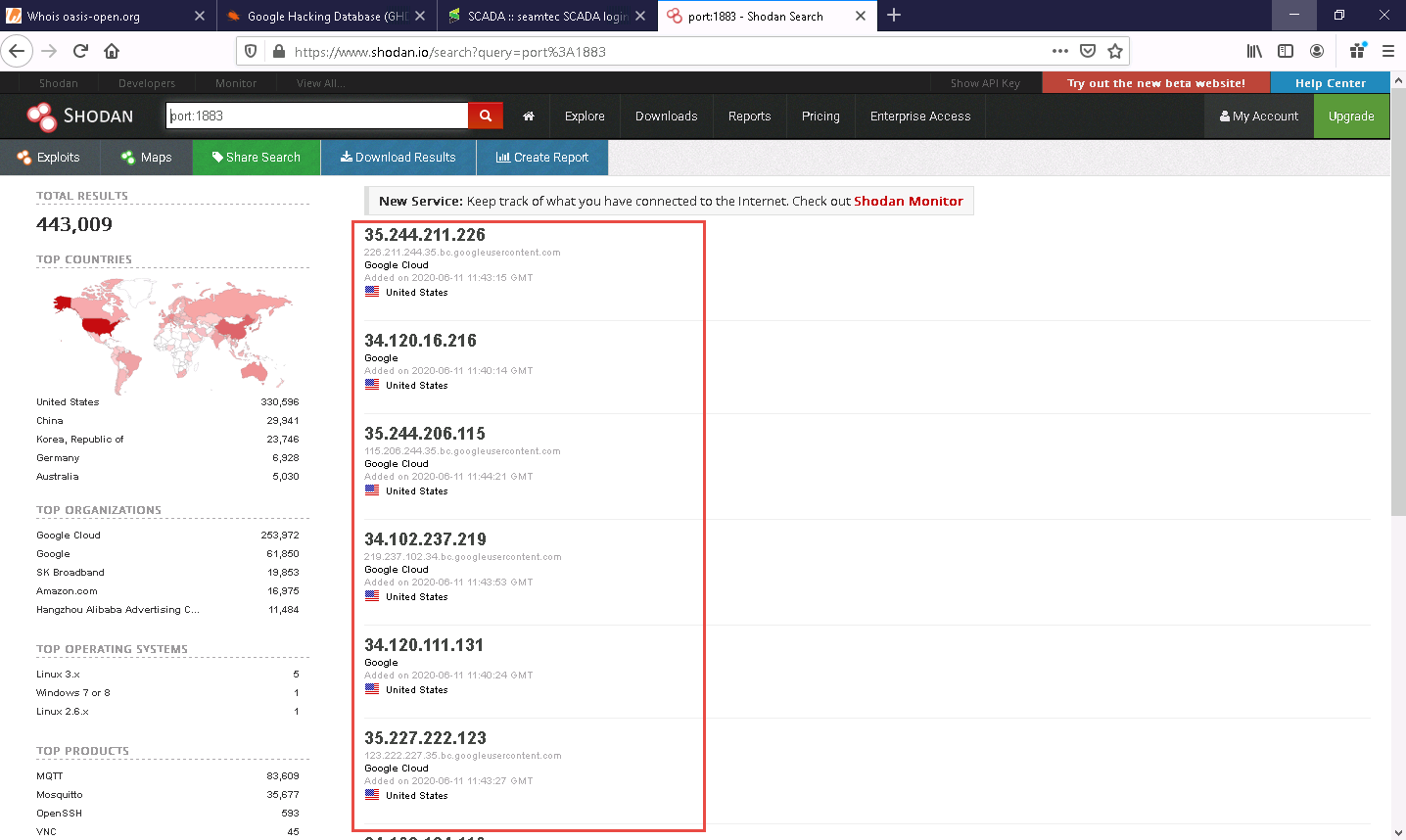
The result appears, displaying the list of IP addresses having port 1883 enabled, as shown in the screenshot.
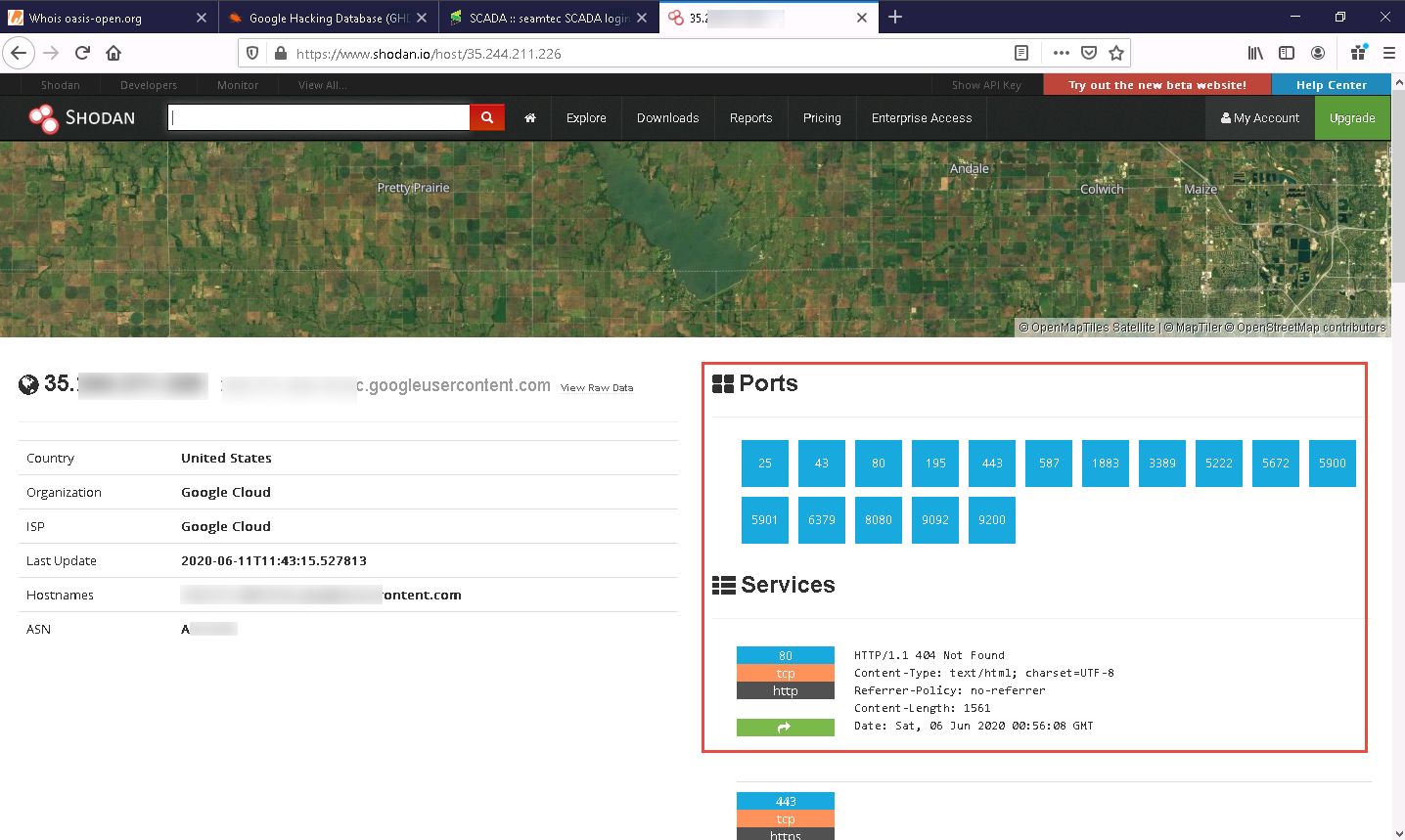
Click on any IP address to view its detailed information.
Detailed results for the selected IP address appears, displaying information regarding Ports, Services, Hostnames, ASN, etc. as shown in the screenshot.
Similarly, you can gather additional information on a target device using the following Shodan filters:
Search for Modbus-enabled ICS/SCADA systems:
port:502
Search for SCADA systems using PLC name:
“Schneider Electric”
Search for SCADA systems using geolocation:
SCADA Country:"US"
Using Shodan, you can obtain the details of SCADA systems that are used in water treatment plants, nuclear power plants, HVAC systems, electrical transmission systems, home heating systems, etc.
This concludes the demonstration of gathering information on a target device using various techniques such as Whois lookup, advanced Google hacking, and Shodan search engine.
Close all open windows and document all the acquired information.
Comments
Post a Comment