Task 2: Perform OS Discovery using Nmap Script Engine (NSE)
Task 2: Perform OS Discovery using Nmap Script Engine (NSE)
Nmap, along with Nmap Script Engine (NSE), can extract considerable valuable information from the target system. In addition to Nmap commands, NSE provides scripts that reveal all sorts of useful information from the target system. Using NSE, you may obtain information such as OS, computer name, domain name, forest name, NetBIOS computer name, NetBIOS domain name, workgroup, system time of a target system, etc.
Here, we will use Nmap to perform OS discovery using -A parameter, -O parameter, and NSE.
In the Windows 10, navigate to the Desktop and double-click Nmap - Zenmap GUI shortcut.
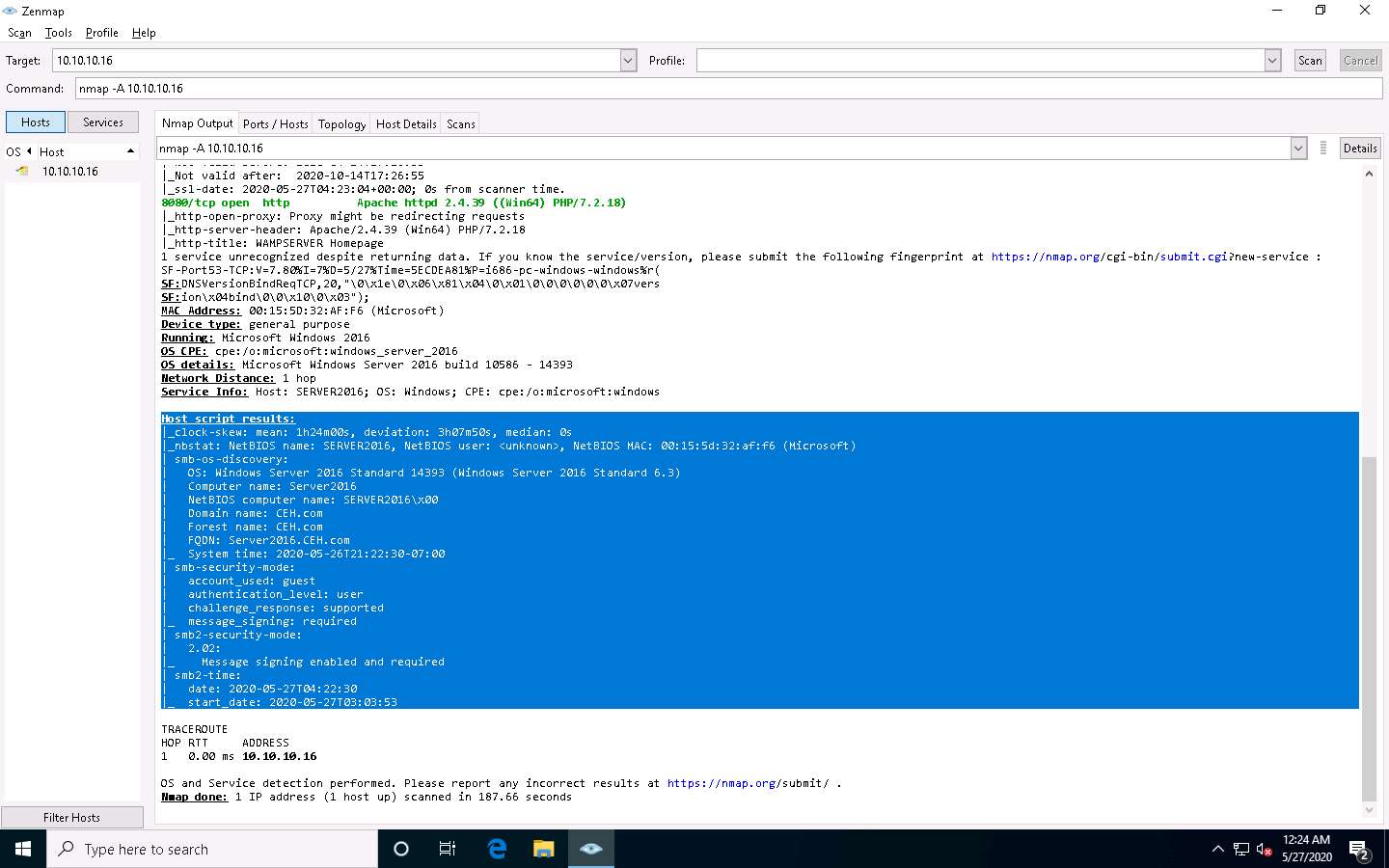
The Zenmap GUI appears. In the Command field, type the command nmap -A [Target IP Address] (here, the target machine is Windows Server 2016 [10.10.10.16]) and click Scan.
-A: to perform an aggressive scan.
The scan takes aprroximately 10 minutes to complete.
The scan results appear, displaying the open ports and running services along with their versions and target details such as OS, computer name, NetBIOS computer name, etc. under the Host script results section.
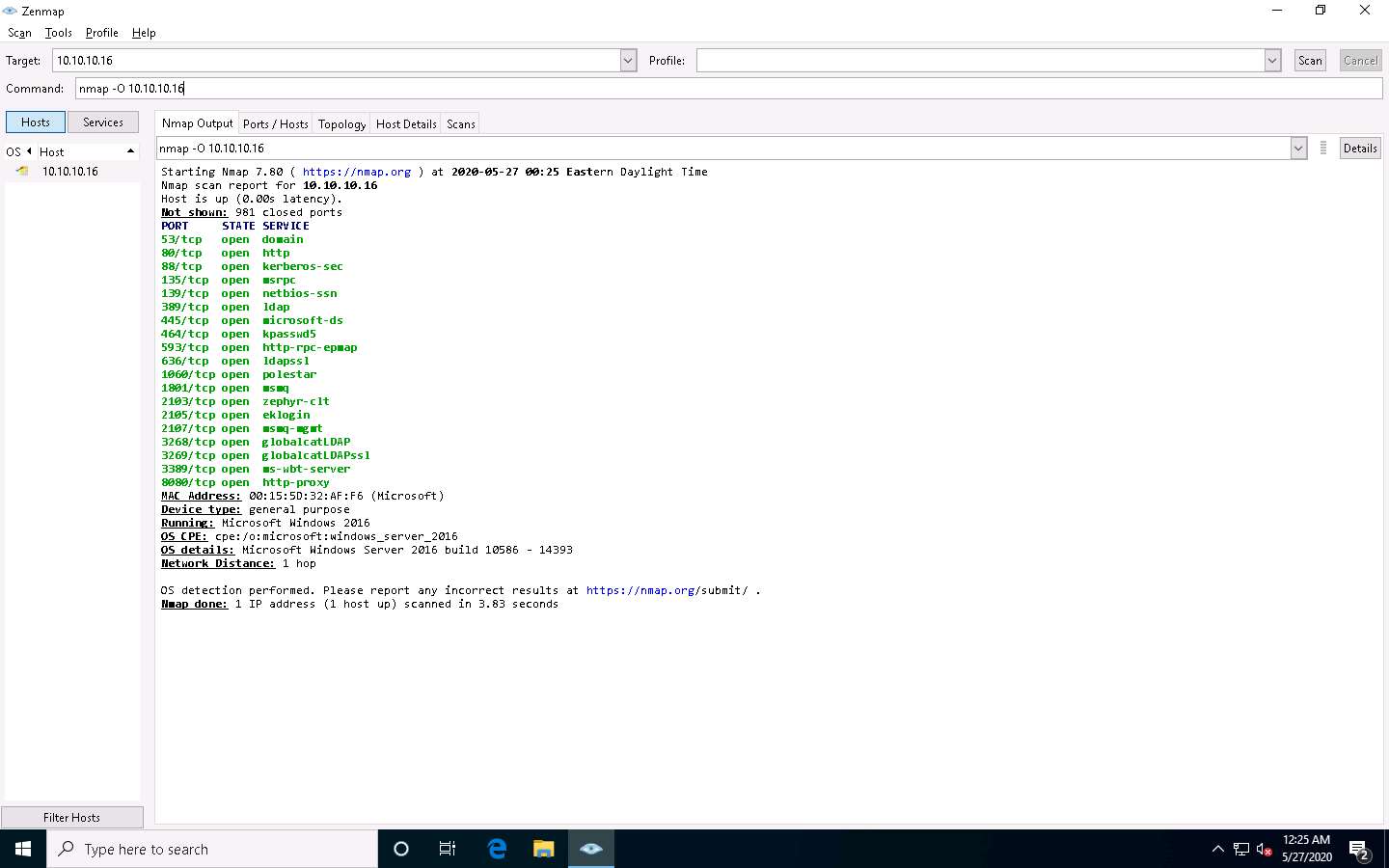
In the Command field, type the command nmap -O [Target IP Address] (here, the target machine is Windows Server 2016 [10.10.10.16]) and click Scan.
-O: performs the OS discovery.
The scan results appear, displaying information about open ports, respective services running on the open ports, and the name of the OS running on the target system.
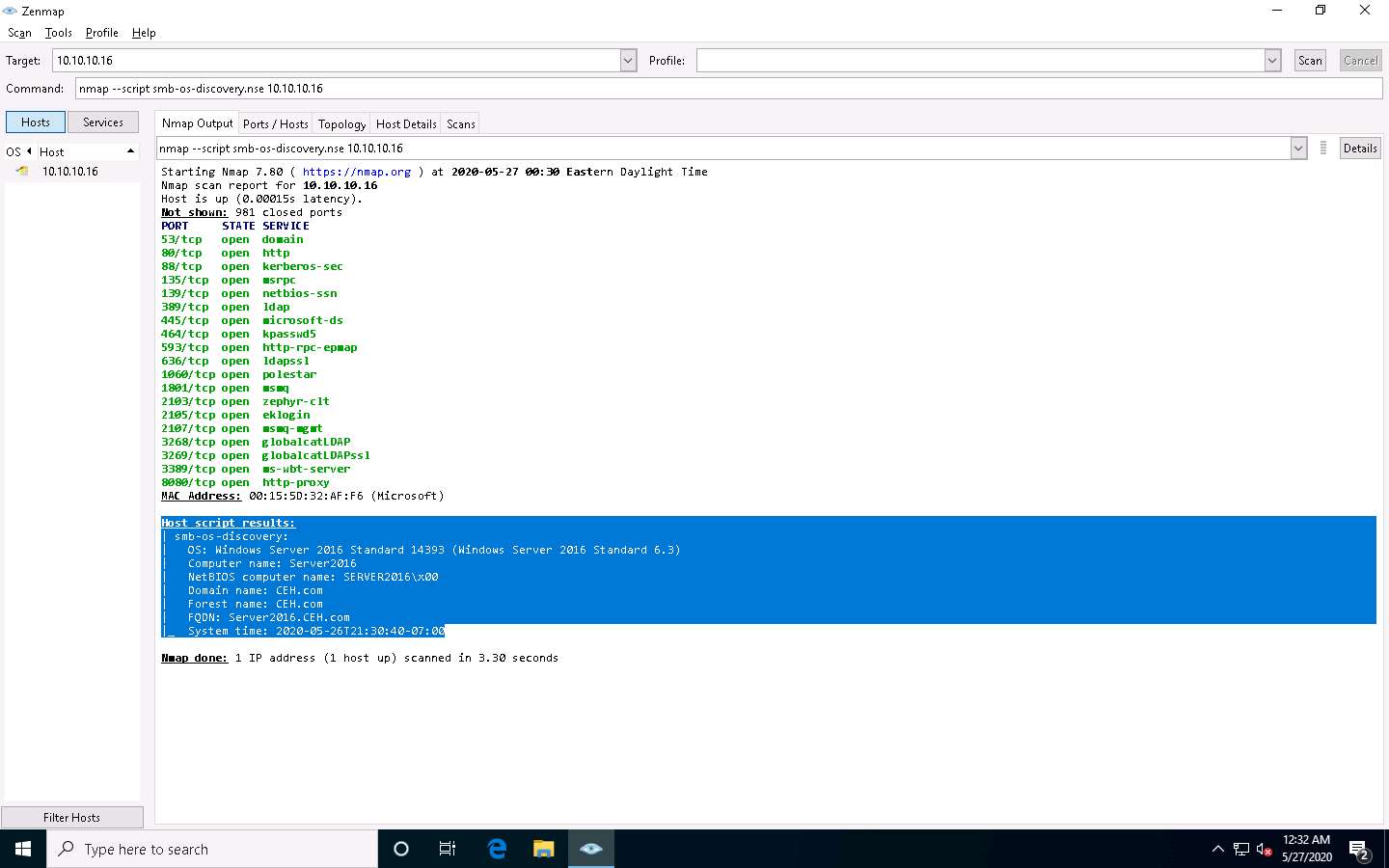
In the Command field, type the command nmap --script smb-os-discovery.nse [Target IP Address] (here, the target machine is Windows Server 2016 [10.10.10.16]) and click Scan.
--script: specifies the customized script and smb-os-discovery.nse: attempts to determine the OS, computer name, domain, workgroup, and current time over the SMB protocol (ports 445 or 139).
The scan results appear, displaying the target OS, computer name, NetBIOS computer name, etc. details under the Host script results section.
This concludes the demonstration of discovering the OS running on the target system using Nmap.
Close all open windows and document all the acquired information.
Comments
Post a Comment